converge your vision and values
Stay Ahead of Cyber Threats with Proactive Dark Web & Vulnerability Intelligence
Monitor. Analyze. Protect.
🛡️ Dark Web Monitoring & Vulnerability Analysis Services
Proactively Detect Threats. Secure Your Digital Assets.
At Teamwin Global, we offer intelligent threat monitoring and in-depth vulnerability analysis to safeguard your critical systems before cybercriminals can exploit them.
🌐 Dark Web Monitoring
Keep track of your organization’s compromised data on the dark web.
-
🔍 Real-Time Dark Web Scanning
We monitor underground forums, marketplaces, and paste sites for leaked credentials, customer data, and intellectual property. -
🧠 AI-Powered Threat Intelligence
Our tools leverage AI and machine learning to detect early signs of breach or data exposure. -
📬 Instant Alerts & Reports
Receive actionable alerts when your data is found on the dark web, with mitigation steps. -
👥 Employee Credential Monitoring
Monitor business email domains to detect credential leaks of your staff.
🧪 Vulnerability Assessment & Analysis
Identify and fix weak points before attackers find them.
-
🖥️ Network & Endpoint Scanning
Scan internal and external IT assets for known vulnerabilities using industry-grade tools. -
🛠️ Patch & Configuration Review
Identify outdated software, weak configurations, and unpatched systems. -
🧯 Risk-Based Prioritization
We categorize vulnerabilities based on exploitability and business impact to prioritize mitigation. -
📊 Compliance-Ready Reports
Reports mapped to standards like ISO 27001, NIST, and PCI DSS.🔧 Dark Web Monitoring Tools
-
Have I Been Pwned
-
SpyCloud
-
DarkOwl Vision
-
Recorded Future
-
ZeroFox
-
Constella Intelligence
-
IntSights
-
Cyble Vision
-
KELA
-
Terbium Labs
-
Expertise and Experience:
Highly Skilled Team: Our team consists of certified professionals with extensive experience in various IT domains.
Comprehensive Solutions:
End-to-End Services: We offer a wide range of services, including network management, cybersecurity, cloud solutions, and IT consulting.
why choose us

Our Cyber Security & Secure networking Services
🔒 Security Operations Center (SOC) Ensure your digital assets are protected with our proactive SOC services: 🛡️ Real-Time Threat Monitoring – Detect and respond to [...]
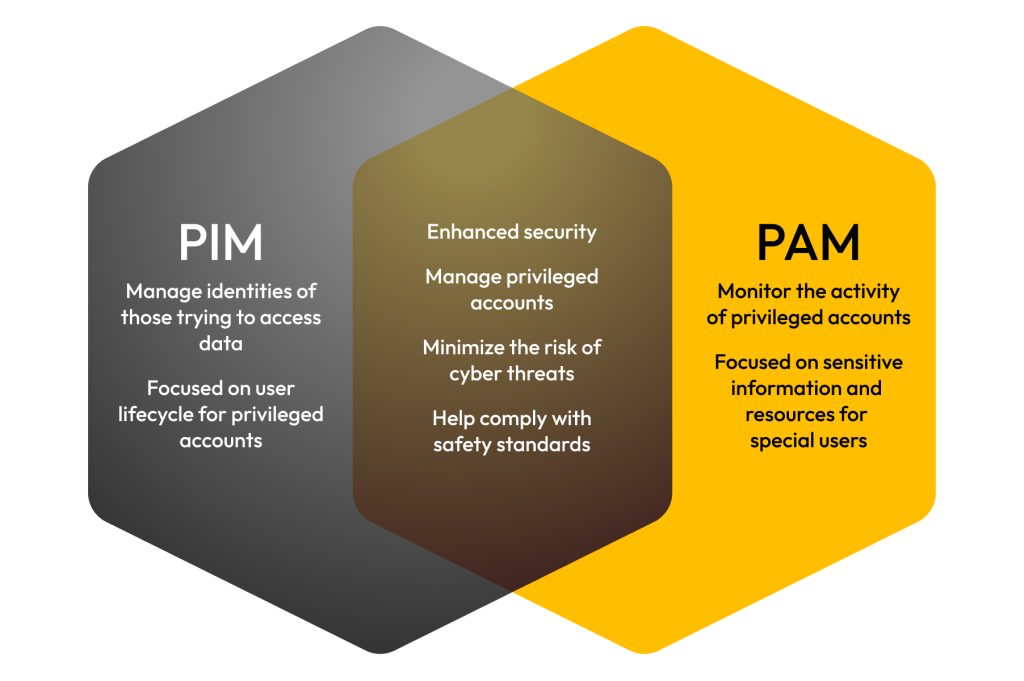
🛡️ PIM & PAM Solutions – Teamwin Global Secure, Monitor & Control Privileged Access.Protect critical assets with advanced Privileged Identity & Access Management solutions. 🔍 [...]
At Teamwin Global, we provide end-to-end cybersecurity solutions built for today’s digital threats. Backed by industry leaders like Seqrite, CrowdStrike, and Microsoft, we help secure [...]
Articles from the latest news
Latest Tech Articles news
A disturbing claim has surfaced in the cybersecurity landscape, sending ripples through the financial and operational structures of a global fast-food giant. On February [...]
Urgent Alert: PoC Exploit Released for Grandstream GXP1600 VoIP Phones RCE Vulnerability The cybersecurity landscape has once again shifted with the emergence of a [...]
In the intricate landscape of telecommunications infrastructure, even seemingly minor vulnerabilities can have significant repercussions. A recent security bulletin from Hewlett Packard Enterprise (HPE) [...]