converge your vision and values
🛡️ PIM & PAM Solutions – Teamwin Global
Secure, Monitor & Control Privileged Access.
Protect critical assets with advanced Privileged Identity & Access Management solutions.
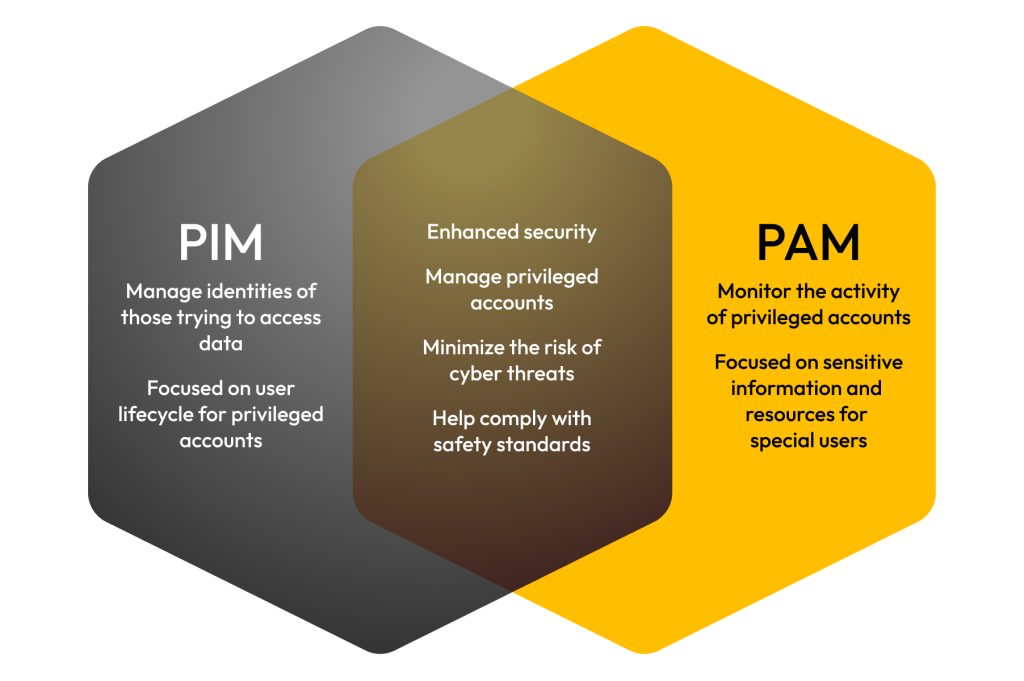
🔍 What is PIM/PAM?
-
Control & audit privileged accounts
-
Prevent insider threats & data breaches
-
Support Zero Trust & compliance
🎯 Why It Matters
-
🛑 Block unauthorized access
-
📋 Ensure compliance (ISO, GDPR, HIPAA)
-
👀 Full visibility of privileged sessions
🧩 Vendor Solutions We Offer
| Vendor | Category |
|---|---|
| CyberArk | Enterprise PAM, Vaulting |
| BeyondTrust | Endpoint & Session Mgmt |
| Delinea (Thycotic) | Vaulting & Policy Control |
| ManageEngine PAM360 | Affordable PAM for SMBs |
| One Identity | Session Monitoring |
| HashiCorp Vault | Secrets Management |
| Wallix | EU Compliance Focused |
| ARCON | Identity Governance & PAM (India) |
| Secureden | Lightweight PAM for SMEs |
⚙️ Key Features
-
🔑 Privileged Access Control
-
📈 Session Recording & Auditing
-
⏱️ Just-in-Time Access
-
🔐 Password Vaulting
Expertise and Experience:
Highly Skilled Team: Our team consists of certified professionals with extensive experience in various IT domains.
Comprehensive Solutions:
End-to-End Services: We offer a wide range of services, including network management, cybersecurity, cloud solutions, and IT consulting.
why choose us
Our Cyber Security & Secure networking Services
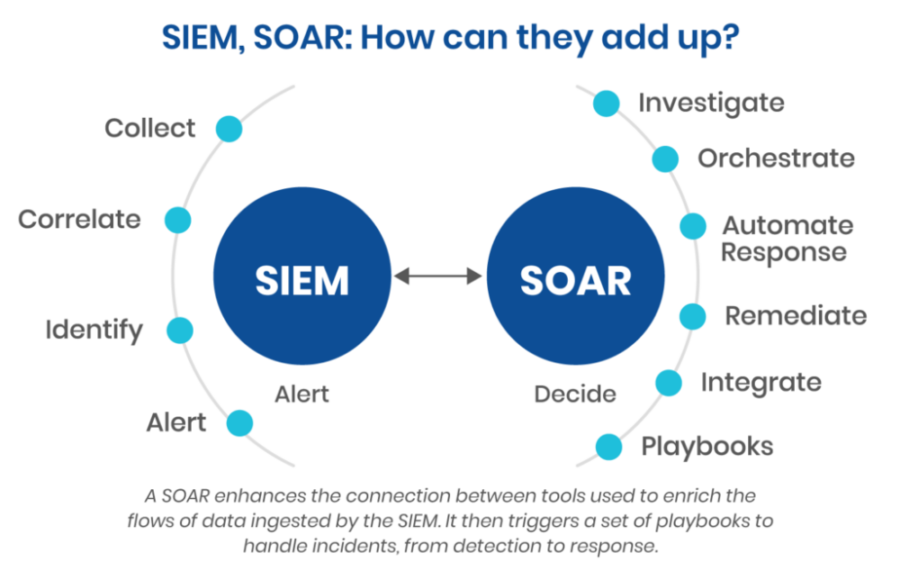
🧠 SIEM & SOAR Solutions | Real-Time Threat Detection & Automated Response – Teamwin Global 📌 Overview Centralize your security data and automate incident response [...]
🛡️ PIM & PAM Solutions – Teamwin Global Secure, Monitor & Control Privileged Access.Protect critical assets with advanced Privileged Identity & Access Management solutions. 🔍 [...]
🔐 Network Security Assessment by Teamwin Global Identify Vulnerabilities. Mitigate Risks. Secure Your Business. Stay ahead of cyber threats with Teamwin Global’s expert-led network security [...]
Articles from the latest news
Latest Tech Articles news
Windows 11 KB5074109 Update: A Stability Nightmare Prompts Microsoft’s Urgent Recall In the intricate ecosystem of operating systems, routine security updates are a cornerstone of [...]
The digital shadows hide many types of actors, but few are as insidious and foundational to the cybercrime ecosystem as initial access brokers (IABs). These [...]
In the high-stakes world of cybersecurity, a disclosed vulnerability often grants attackers a roadmap to exploit systems. However, a more immediate and insidious threat emerges [...]