The digital landscape is a constant ebb and flow of innovation and challenge. This past December, enterprise administrators faced an unexpected and critical disruption to [...]
Unmasking Storm-0249: From Phishing to Stealthy EDR Evasion The threat landscape is constantly evolving, and cyber adversaries are becoming increasingly sophisticated. A prime example of [...]
The digital threat landscape constantly shifts, with cybercriminals consistently seeking novel methods to bypass defenses and deploy malware. A recent and particularly insidious social engineering [...]
The relentless pace of cyber threats demands innovative solutions. Traditional penetration testing, while crucial, often struggles to keep up with the speed of modern web [...]
In the constant battle against cyber threats, a new and insidious adversary has emerged, specifically targeting Windows users with a penchant for cryptocurrency and valuable [...]
The Alarming Rise of AiTM: A New MFA Bypass Threat to Microsoft 365 and Okta Users Organizations worldwide face an escalated threat from a sophisticated [...]
Unearthing Secrets: How Researchers Revived a 20-Year-Old “Blinkenlights” Attack to Dump Smartwatch Firmware In a fascinating demonstration of cybersecurity ingenuity, researchers at Quarkslab have successfully [...]
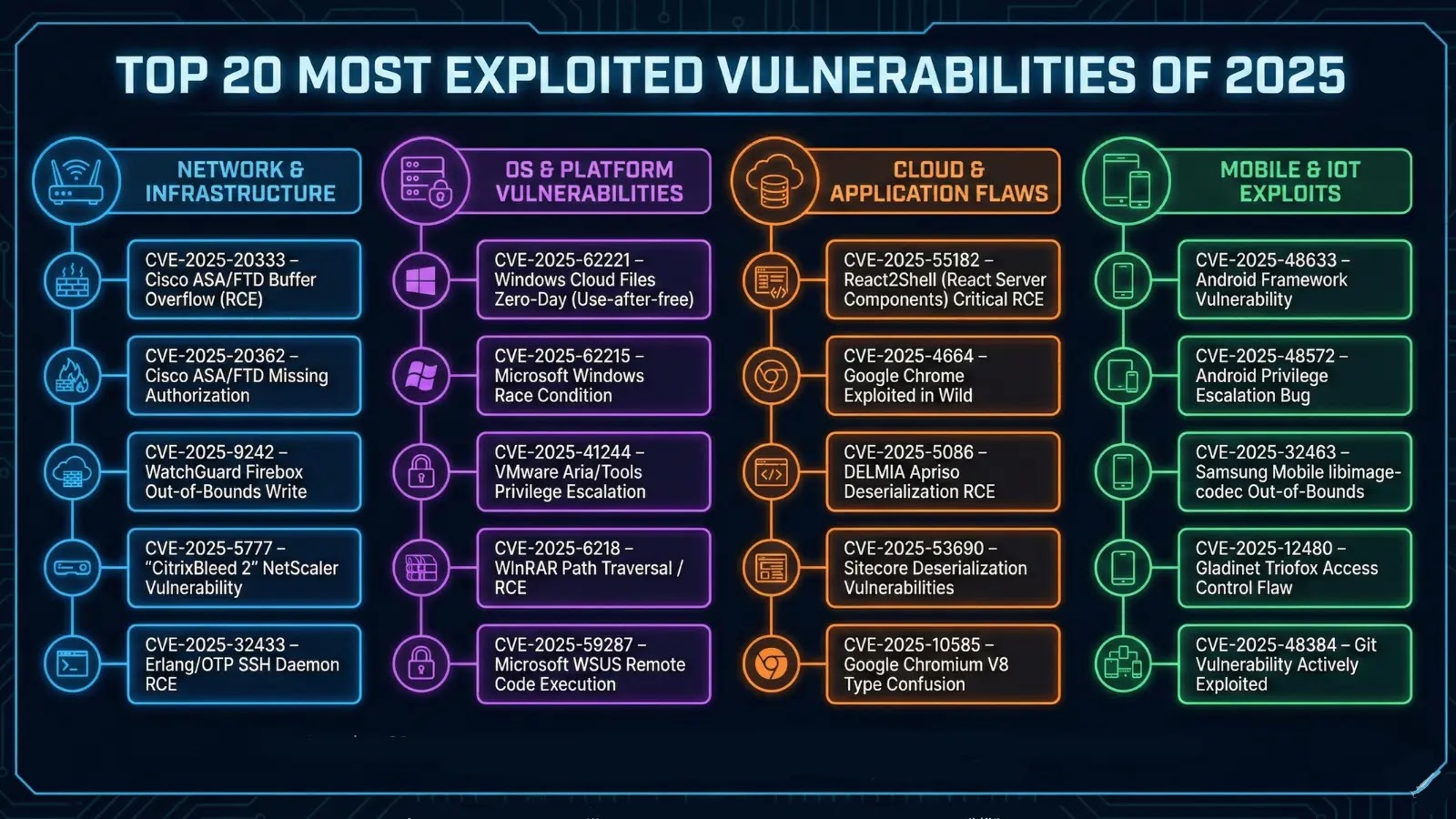
The year 2025 has cemented its place in cybersecurity history as a period of relentless and sophisticated vulnerability exploitation. Organizations across every sector, from nascent [...]
In the relentlessly evolving landscape of cyber threats, understanding the tactics and tools of adversarial groups is paramount for effective defense. Today, we delve into [...]
In the relentless landscape of cyber threats, a sophisticated new phishing technique has emerged, targeting Microsoft accounts with alarming efficacy. Dubbed “ConsentFix,” this attack bypasses [...]