New Vulnerabilities in React Server Components Expose DoS and Source Code Risks Just as the dust began to settle on a significant Remote Code [...]
GitLab, a cornerstone for millions of developers and organizations, recently shipped critical security patches addressing a suite of vulnerabilities. These patches, released on December 10, [...]
In the fast-paced realm of continuous integration and continuous delivery (CI/CD), Jenkins stands as a cornerstone for countless organizations, automating critical development pipelines. However, this [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 CURRENT ACTIVITIES Threat Actors exploiting Buffer Overflow Vulnerability in D-Link routers Indian – Computer Emergency Response Team (https://www.cert-in.org.in) It [...]
Developers Beware: Malicious Extensions Unleash on VS Code Marketplace The digital tools developers rely on are constantly under threat. A recent, alarming discovery highlights this [...]
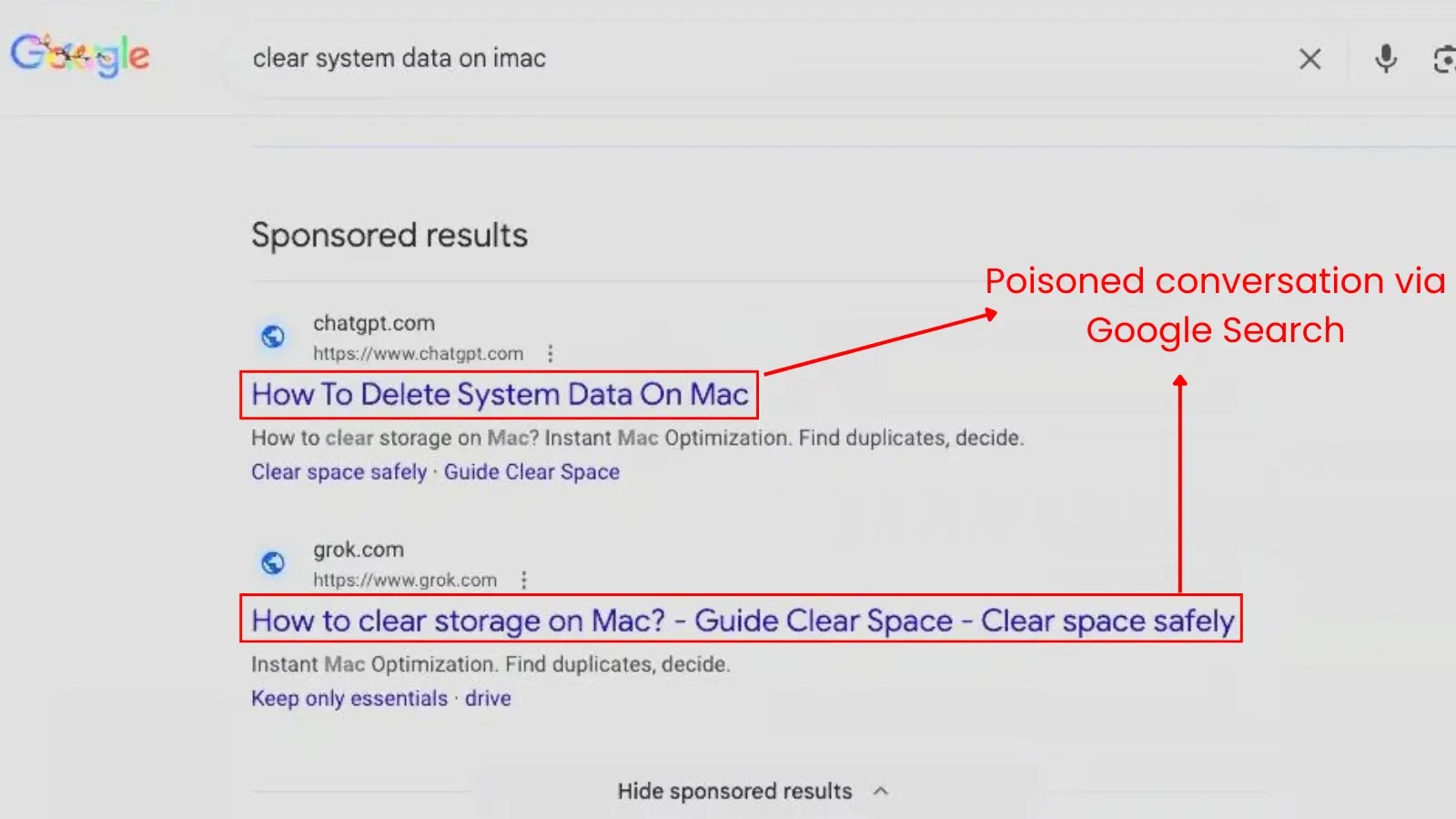
The Deceptive Lure of AI: How Threat Actors Weaponize ChatGPT Against Mac Users with AMOS InfoStealer In an increasingly sophisticated threat landscape, cyber adversaries are [...]
The cybersecurity landscape is constantly shifting, with malicious actors continually refining their tactics. A recent discovery by security researchers at Palo Alto Networks highlights a [...]
A Betrayal of Trust: Cisco-Trained Hackers Weaponize Expertise Against Their Mentor The cybersecurity landscape has been rocked by a deeply unsettling development: two individuals, once [...]
In the constant battle to secure digital environments, the emergence of sophisticated malware strains presents a continuous challenge. Among these, ValleyRAT, also known as Winos [...]
The New Frontier of Cybercrime: Threat Actors Weaponize AI Conversations to Deploy AMOS Stealer Cybersecurity’s battleground constantly shifts. What was once a focus on [...]