A new, highly sophisticated cyber campaign has surfaced, employing a deceptive technique dubbed “ClickFix” to propagate a custom remote access trojan (RAT) known as [...]
For organizations relying on WordPress, a new and insidious threat has emerged, silently compromising websites to PUSH malware onto unsuspecting users. A threat actor, [...]
A disturbing revelation has sent ripples through the cybersecurity landscape: Conduent Business Services, LLC, a prominent government technology contractor, has been entangled in a [...]
Anthropic Claude Under Large Scale Distillation Attacks By Chinese AI Labs with 13 Million Exchanges
The landscape of artificial intelligence is marked by rapid innovation, but also by increasingly sophisticated threats. A recent accusation by Anthropic, creators of the [...]
Google Chrome users, pay critical attention. A recent emergency security update, rolling out progressively to versions 114.0.5735.116/117 for Windows and macOS, and 114.0.5735.116 for [...]
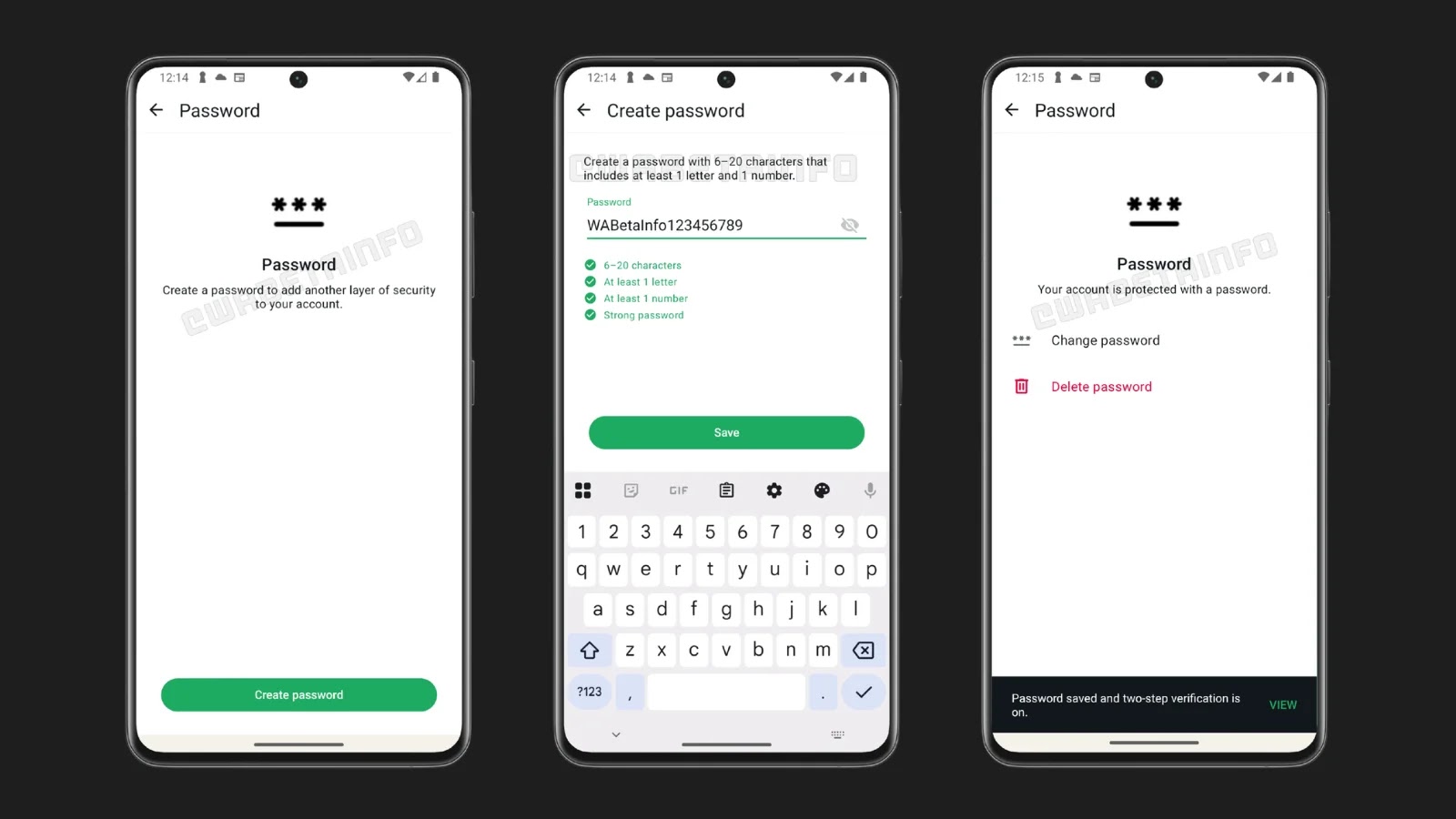
In an increasingly interconnected digital landscape, the security of our communication channels is paramount. WhatsApp, a platform relied upon by billions globally, is taking a [...]
A significant challenge has been issued to the cybersecurity community, one that directly confronts the deeply integrated smart home ecosystem. A new bug bounty program [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Atlassian Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: High Software Affected Bamboo Data [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Security Bypass Vulnerability in Honeywell CCTV products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Systems Affected [...]
The digital threat landscape never rests, and a recent advisory from the Cybersecurity and Infrastructure Security Agency (CISA) serves as a stark reminder of this [...]