The code that builds our digital world is under attack. Developers, the architects of modern software, are increasingly becoming prime targets for sophisticated cybercriminals. This [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Microsoft Edge Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Microsoft Edge [...]
Urgent Alert: Critical WatchGuard Firebox Vulnerabilities Demand Immediate Action Organizations relying on WatchGuard Firebox appliances for network security are facing a significant threat. Recent disclosures [...]
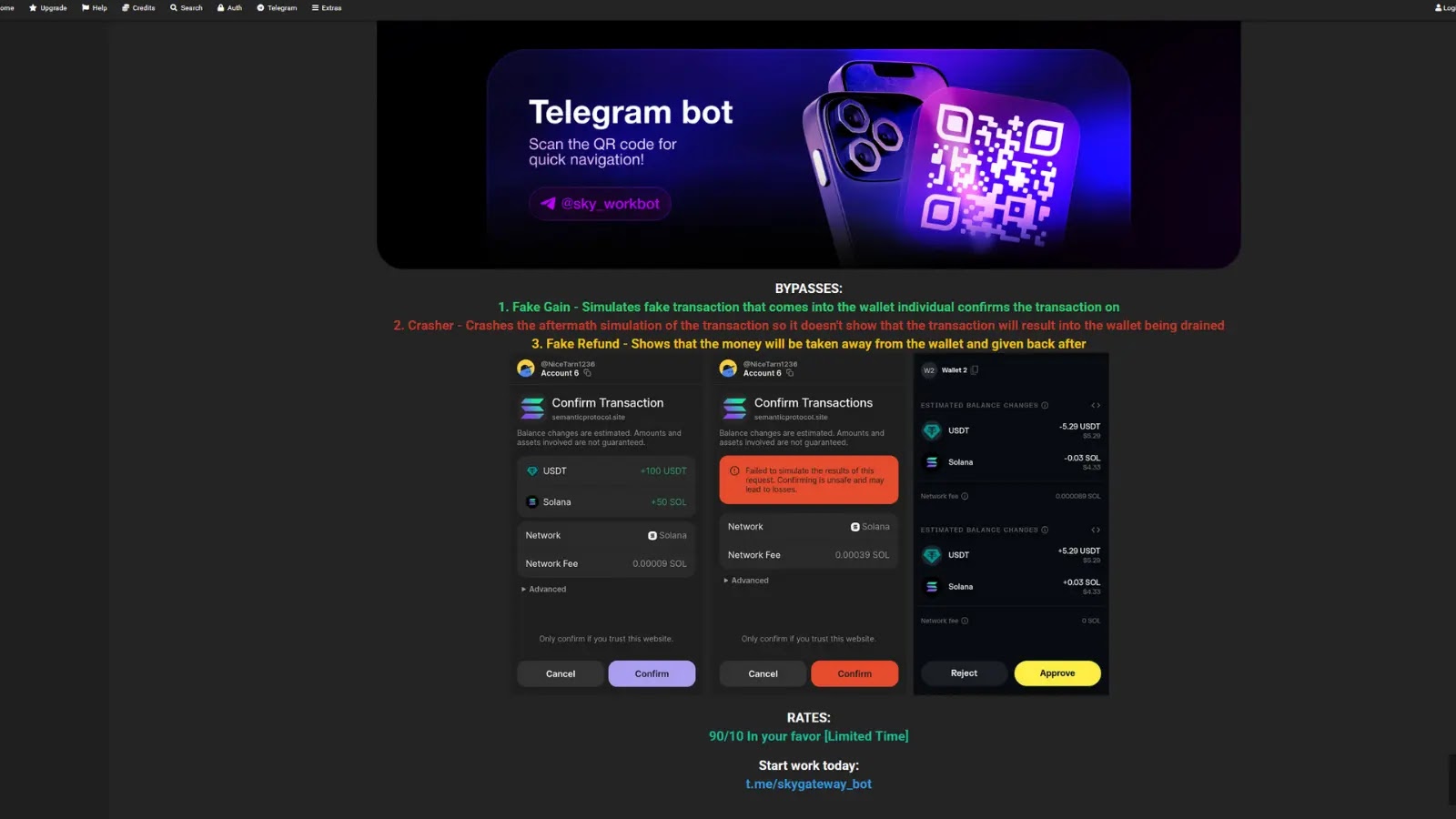
A disturbing incident recently highlighted the ever-present danger of sophisticated financial scams in the cryptocurrency space. An individual, identified as Jack and a Solana enthusiast [...]
OceanLotus Shifts Focus: Targeting China’s Xinchuang IT Ecosystem in Supply Chain Attacks The digital battleground continues to evolve, and with it, the sophistication of state-sponsored [...]
Unmasking a Digital Shadow: Indonesia’s Gambling Ecosystem Under Scrutiny For over a decade, a sophisticated cybercrime infrastructure has silently thrived, deeply embedded within Indonesia’s illegal [...]
The cybercriminal landscape is undergoing a significant shift, with sophisticated tools increasingly paving the way for destructive ransomware attacks. A newly identified threat, dubbed “Shanya,” [...]
Hundreds of Porsches Rendered Undrivable: A Satellite Security System Malfunction immobilizes Luxury Vehicles Imagine stepping out to your high-performance luxury vehicle, only to find it [...]
The pharmaceutical industry, a bastion of innovation and critical research, finds itself increasingly targeted by sophisticated cyber threats. The recent disclosure by Inotiv, a prominent [...]