The security of critical infrastructure is paramount. A new warning from the Cybersecurity and Infrastructure Security Agency (CISA) highlights a severe authentication vulnerability impacting Iskra’s [...]
In the dynamic landscape of web development, frameworks like Angular are indispensable, powering countless applications with their robust features. However, even the most sophisticated systems [...]
A significant vulnerability within a widely used Elementor add-on has surfaced, presenting a critical threat to WordPress website security. Security researchers have sounded the alarm, [...]
A disturbing new entry has surfaced in the cybercriminal underground: the alleged promotion of the K.G.B RAT, a remote access trojan described as “fully undetectable.” [...]
The digital landscape is a constant battleground, and for Linux systems, two sophisticated adversaries have emerged, pushing the boundaries of stealth and persistence: BPFDoor and [...]
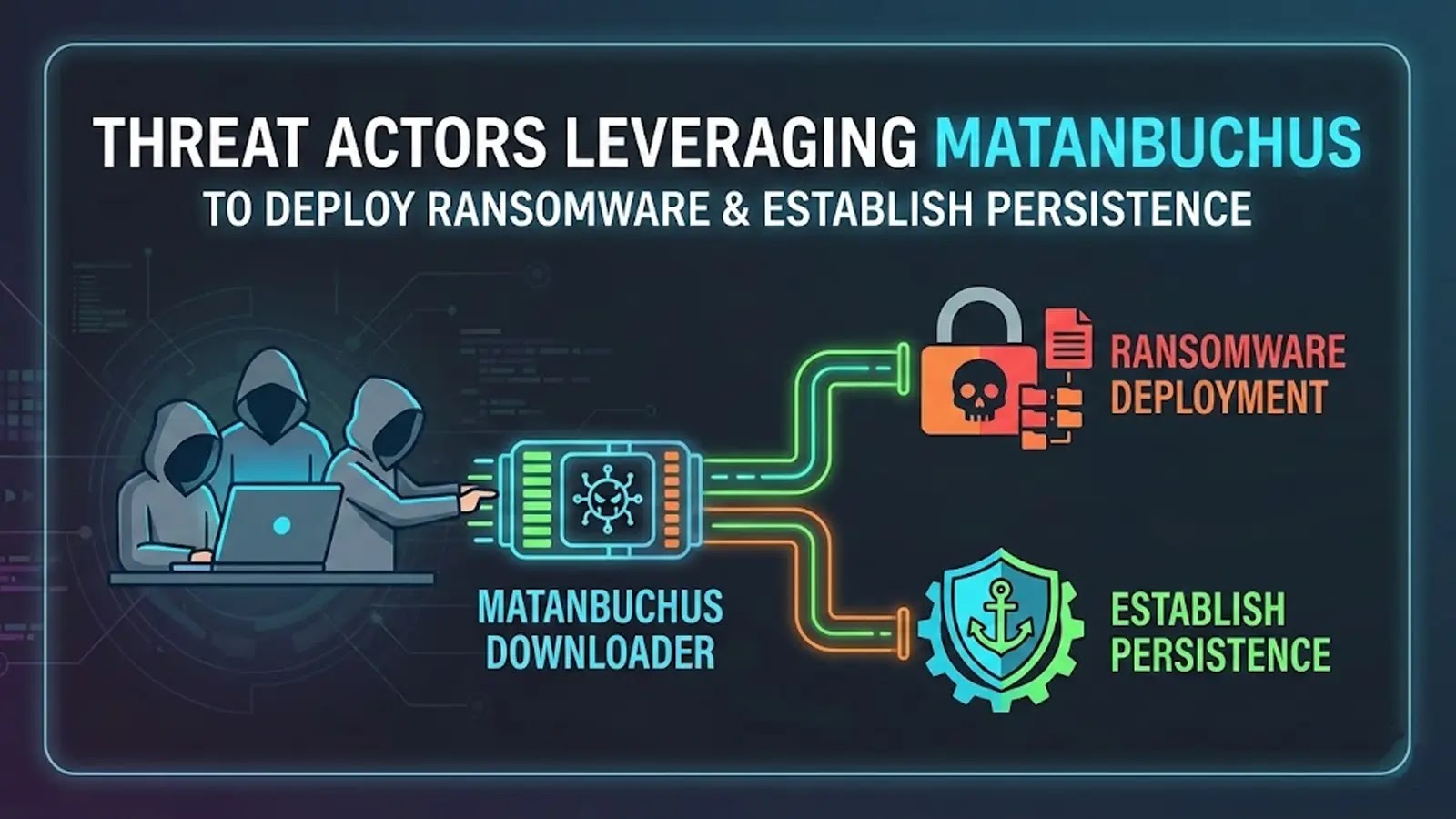
Unmasking Matanbuchus: A Rising Threat in the Ransomware Landscape The digital defense perimeter is under constant siege, with sophisticated tools quickly evolving in the hands [...]
The digital landscape is in constant flux, and securing online communications is paramount. At the heart of this security lie SSL/TLS certificates, authenticating websites and [...]
The web development world is in constant motion, and with innovation comes the persistent challenge of security. Recently, the Django development team issued critical security [...]
A Critical Flaw in Apache Struts: Understanding Disk Exhaustion Attacks The digital landscape is a constant battlefield, and a recently discovered critical security vulnerability [...]
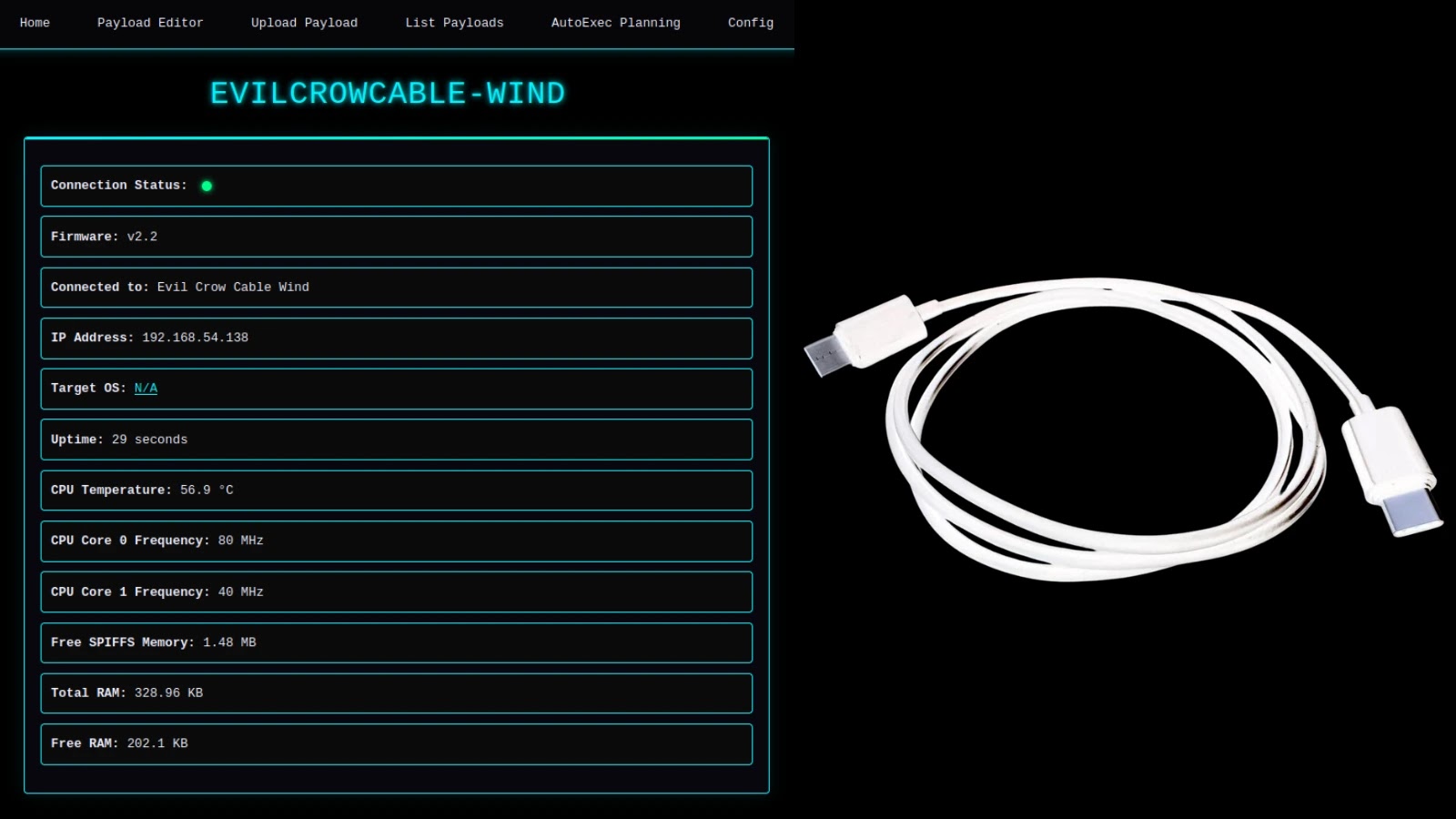
The Silent Assassin: When Your Charging Cable Becomes a Cyber Weapon Imagine plugging in your device to charge, a routine action, and unknowingly inviting [...]