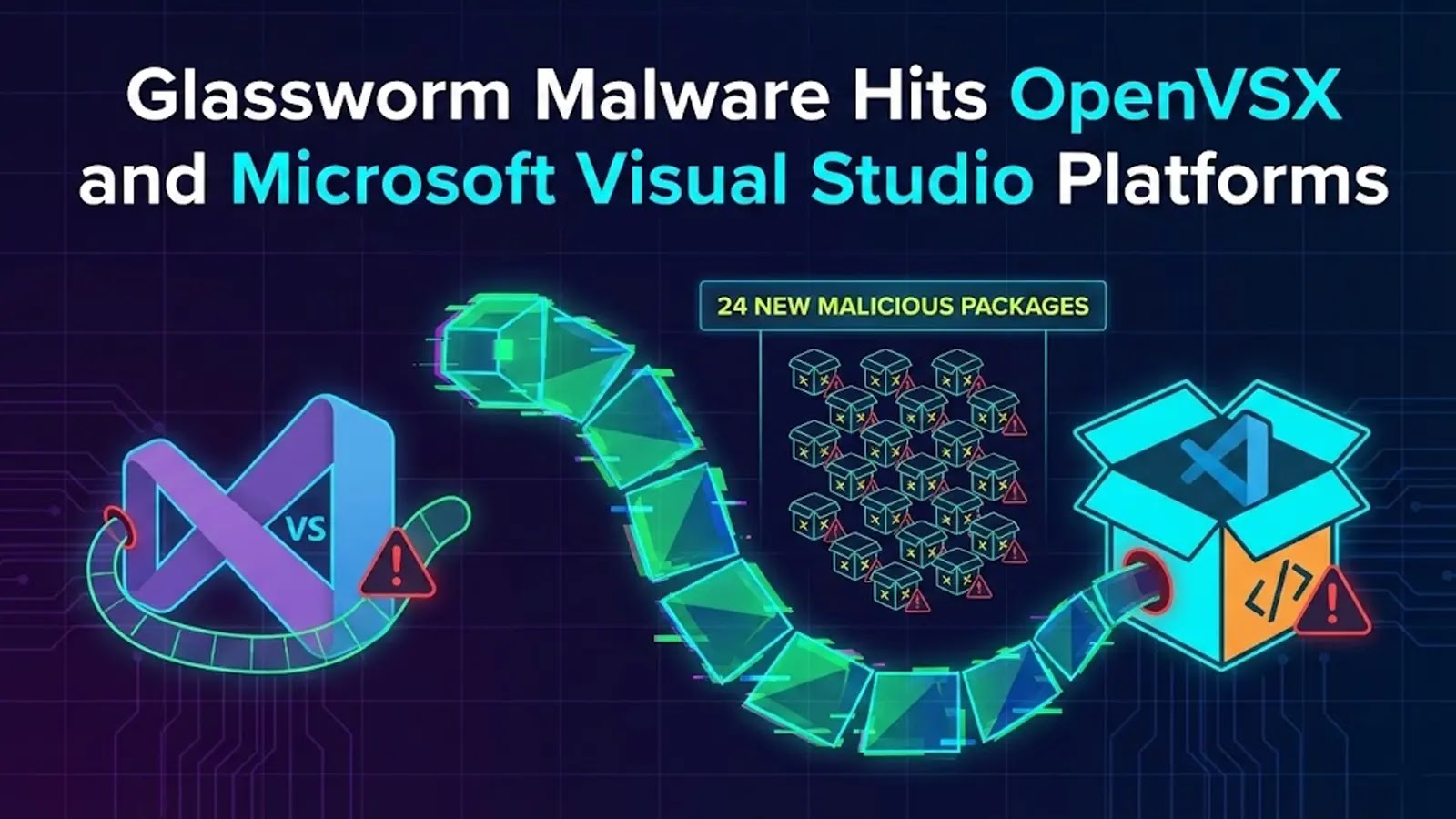
The digital supply chain, a critical lifeline for modern software development, is once again under siege. A sophisticated malware campaign, dubbed “Glassworm,” has re-emerged [...]
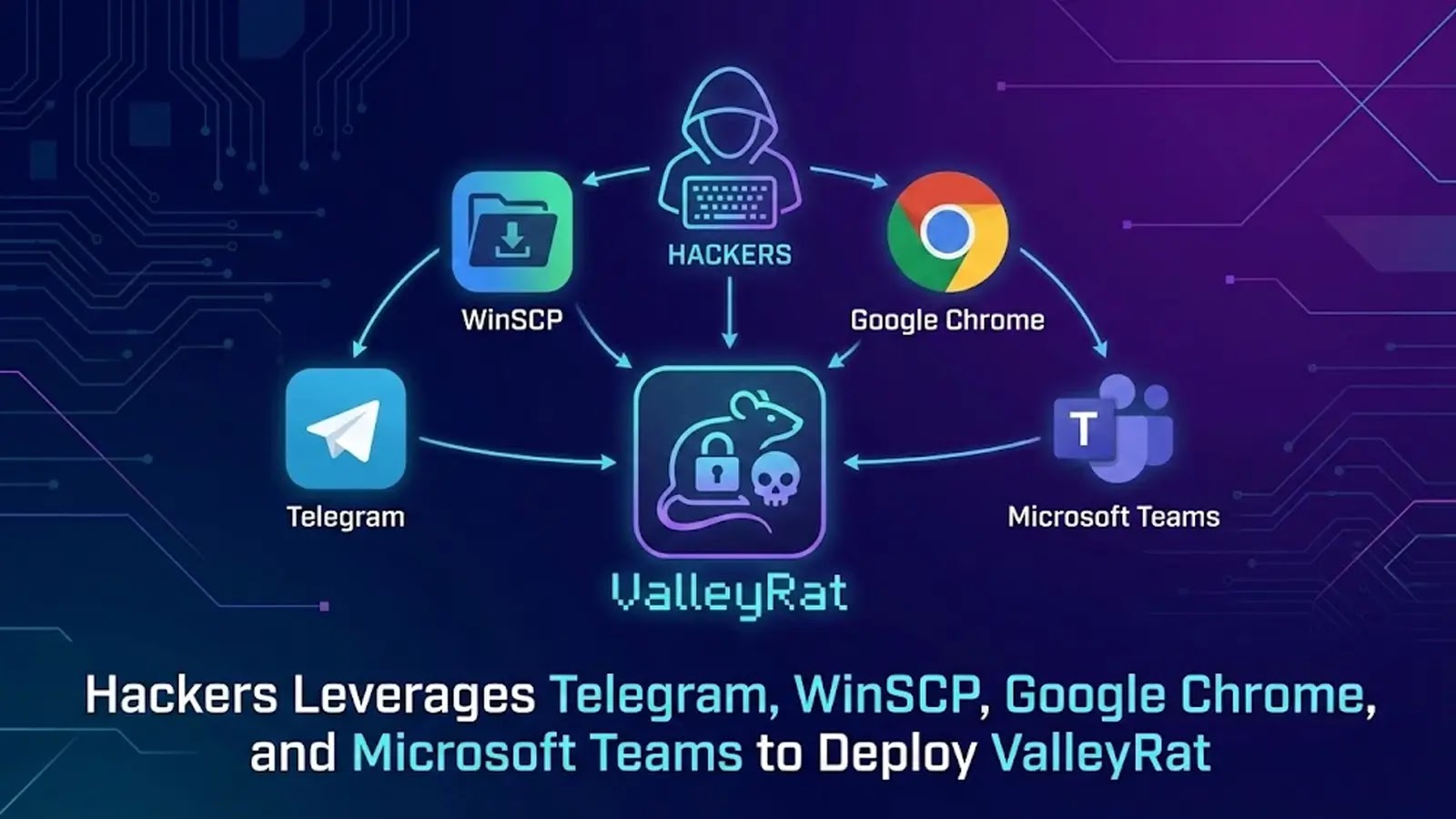
The Silent Compromise: ValleyRat Leverages Popular Apps for Persistent Access In a landscape where digital trust is paramount, a new and concerning malware campaign [...]
The landscape of single-board computing just got more accessible and powerful. The Raspberry Pi Foundation has unveiled a significant expansion of its flagship platform, [...]
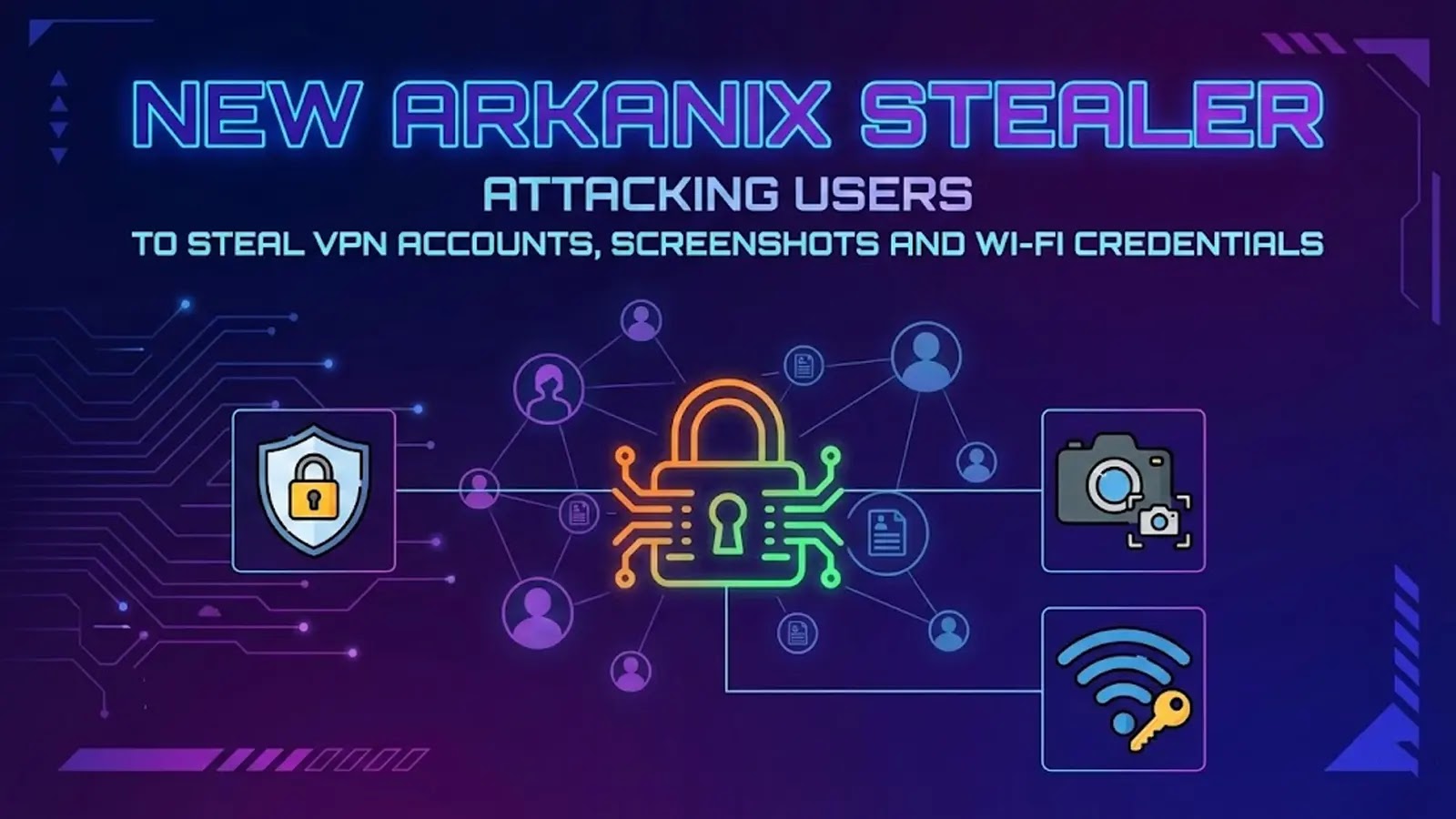
Urgent Threat: New Arkanix Stealer Targets VPNs, Wi-Fi, and Credentials The digital landscape is constantly challenged by new and evolving cyber threats. A new and [...]
The digital battlefield demands constant vigilance, and for cybersecurity professionals, access to their tools is paramount. Imagine a scenario where the very portal designed [...]
In the evolving landscape of cyber warfare, state-sponsored entities and commercial mercenary groups continuously refine their tools and tactics. A recent and deeply concerning [...]
The Android TV ecosystem, a widely adopted platform for digital entertainment, has recently been rocked by a serious security incident. SmartTube, a highly popular third-party [...]
The rapid integration of Artificial Intelligence (AI) into enterprise operations presents a paradox: unprecedented efficiency gains alongside profound new security challenges. A recent report, [...]
Frenetik’s Deception Technology: A Bold Bet Against the AI Arms Race As the cybersecurity landscape intensifies, a familiar narrative often dominates headlines: the relentless [...]
The clandestine operations of state-sponsored threat actors often remain shrouded in secrecy, making real-time insight exceptionally rare. However, a recent collaborative investigation has peeled [...]