Frenetik’s Deception Technology: A Bold Bet Against the AI Arms Race As the cybersecurity landscape intensifies, a familiar narrative often dominates headlines: the relentless [...]
The clandestine operations of state-sponsored threat actors often remain shrouded in secrecy, making real-time insight exceptionally rare. However, a recent collaborative investigation has peeled [...]
The digital landscape is a constant battleground, and threat actors are perpetually refining their arsenals. A recent, alarming escalation has surfaced from Brazil, where sophisticated [...]
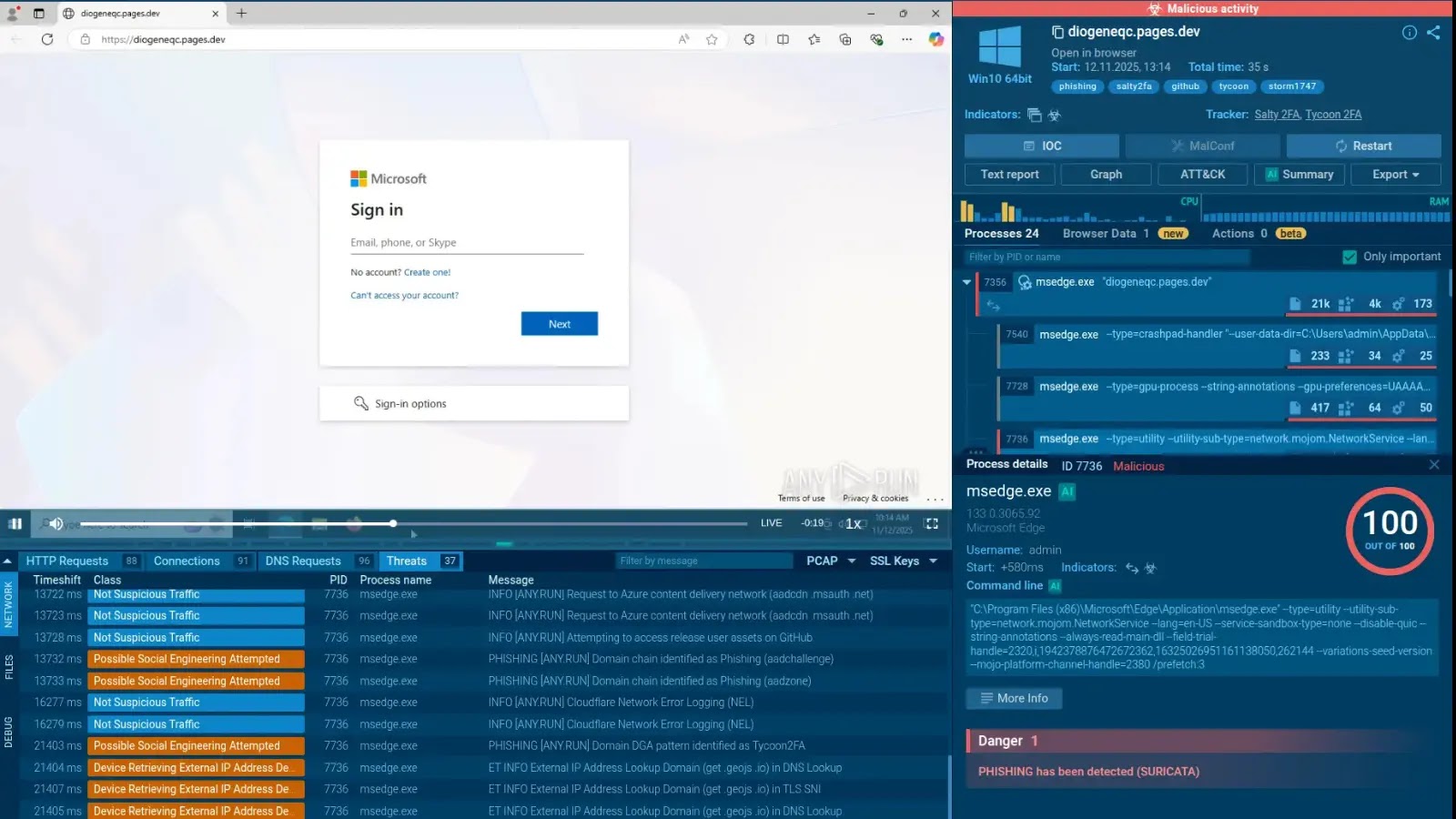
The Evolving Threat: Salty2FA and Tycoon2FA Phishing Kits Converge The landscape of cyber threats is in constant flux, with attackers continuously refining their methodologies. [...]
Cyber Espionage Intensifies: Ukraine-Linked Hackers Target Russian Aerospace and Defense The geopolitical landscape now extends firmly into cyberspace, with nation-state-backed hacking groups actively impacting [...]
The Alarming Rise of Evilginx: Why Your MFA Isn’t as Secure as You Think Multi-factor authentication (MFA) has long been heralded as a critical defense [...]
The Silent Threat: How Your Dash Cam Can Become a Cyber Weapon Dash cams have evolved from niche gadgets to ubiquitous safety devices, offering crucial [...]
Insider threats represent one of the most insidious and challenging security dilemmas any organization faces. Unlike external attacks, they originate from within, often leveraging legitimate [...]
ChatGPT Down: Unpacking the Worldwide Outage and Disappearing Conversations Early Wednesday morning, millions of users globally experienced a significant disruption to their workflows as ChatGPT, [...]
In the constant arms race between security researchers and malicious actors, an unexpected challenger emerges from the depths of your daily browsing: your web browser. [...]