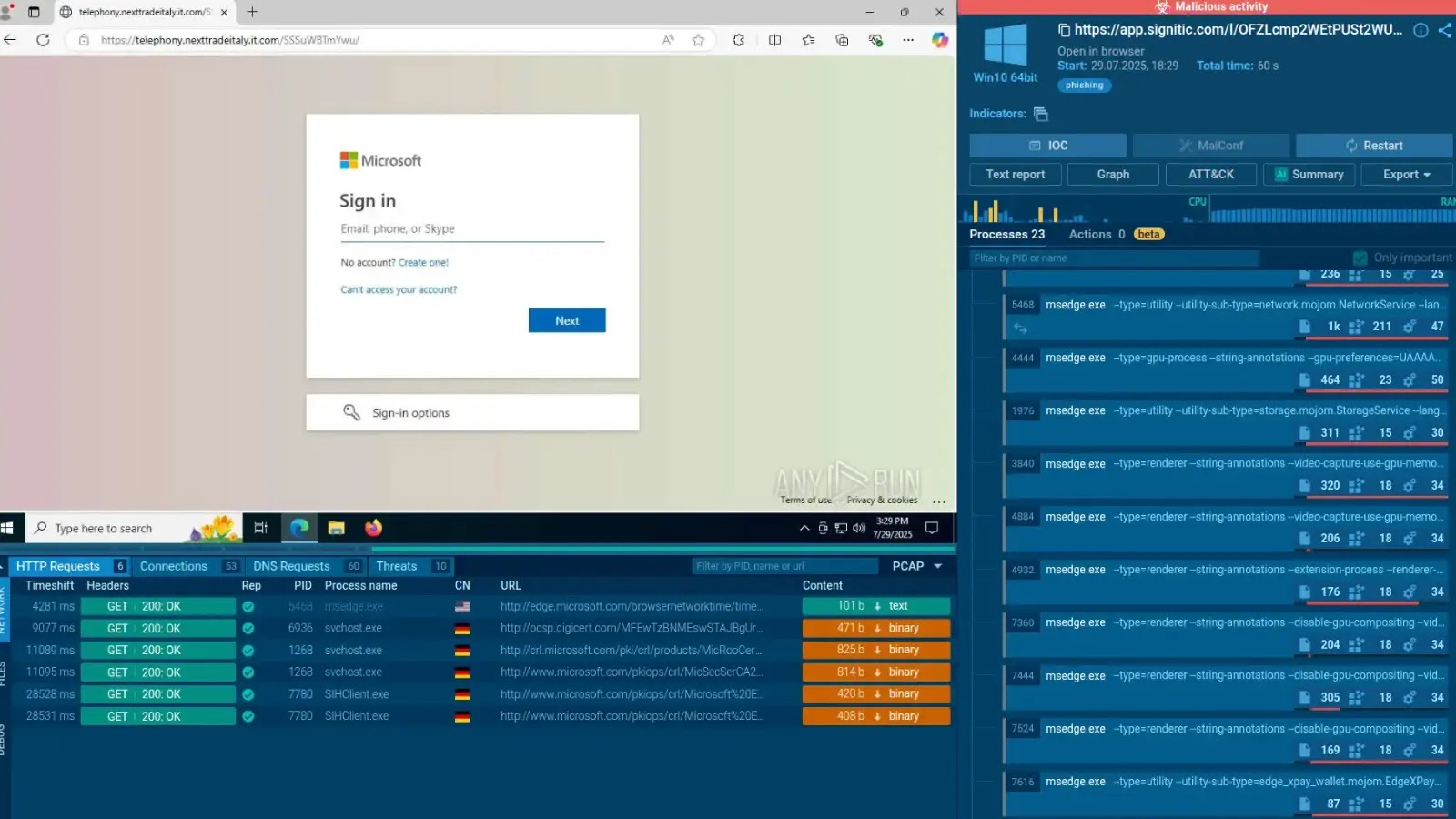
The digital landscape is a battleground, and threat actors are relentlessly seeking new vulnerabilities. A particularly insidious development has surfaced: the Akira ransomware group [...]
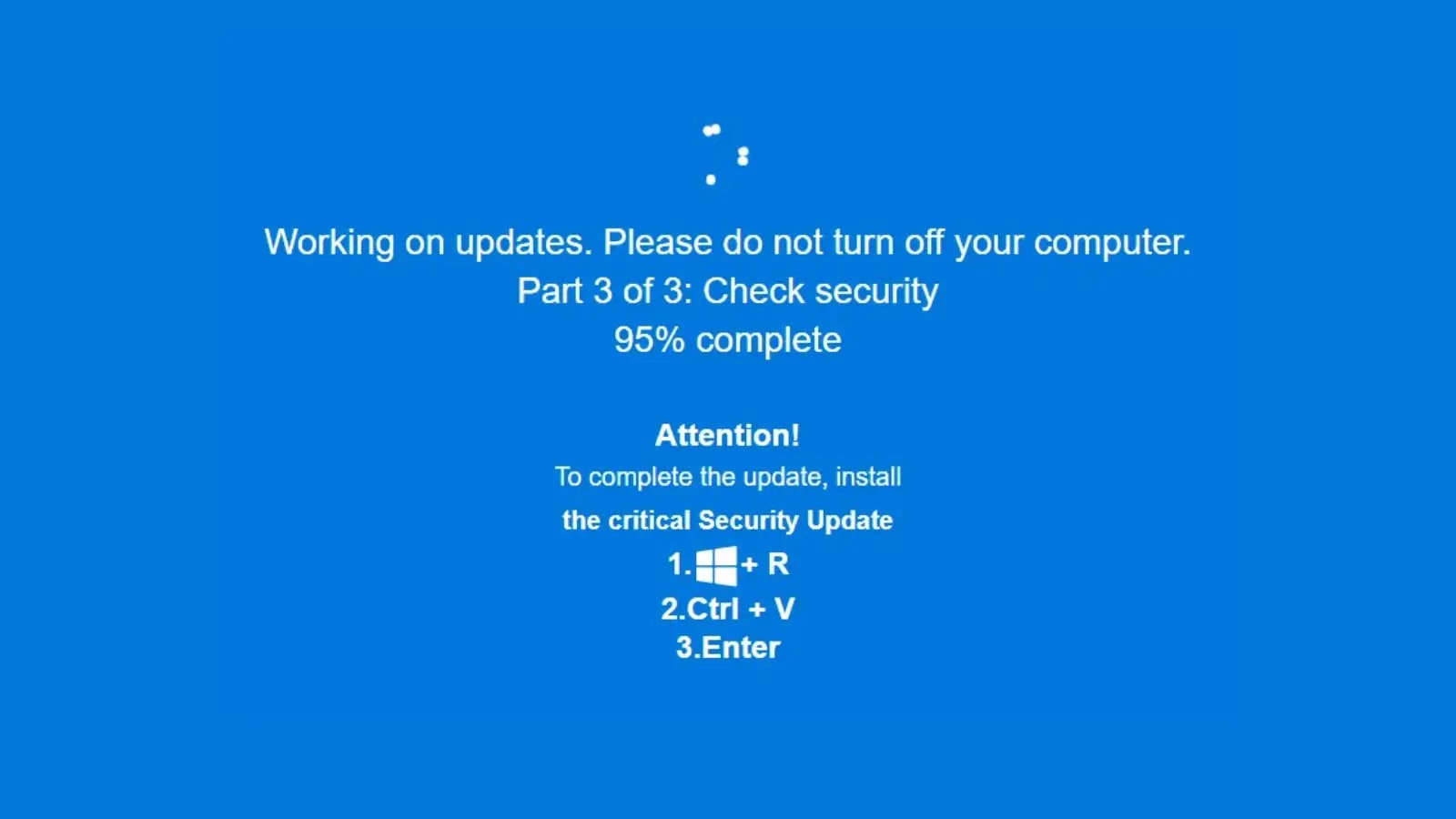
Unmasking JackFix: How Malicious Actors Weaponize Windows Updates The digital threat landscape is perpetually shifting, with adversaries continually innovating to breach defenses. A new, [...]
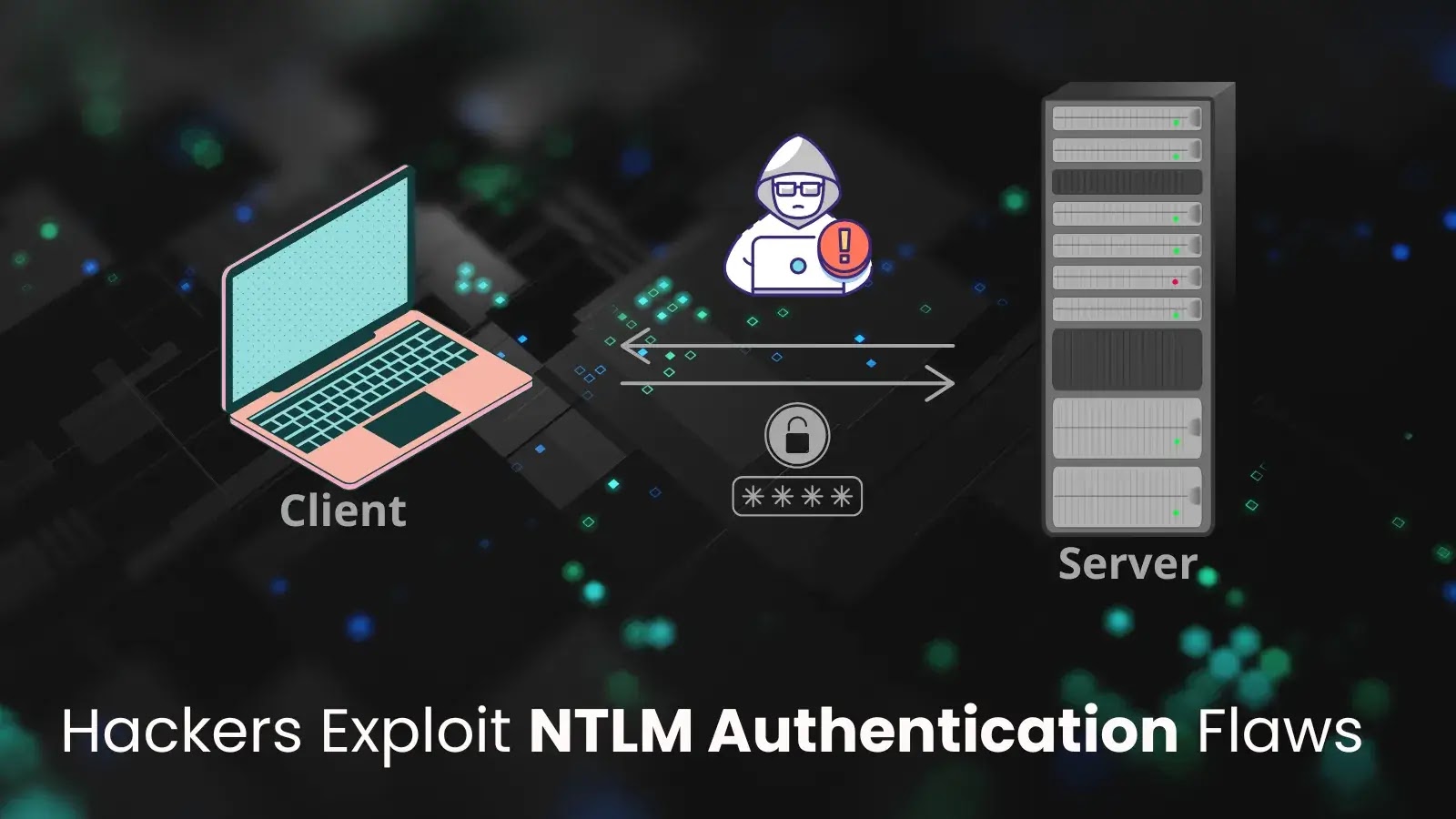
The Persistent Peril: NTLM Authentication Flaws and Ongoing Windows System Compromise The digital landscape is a battleground where old vulnerabilities often resurface with new [...]
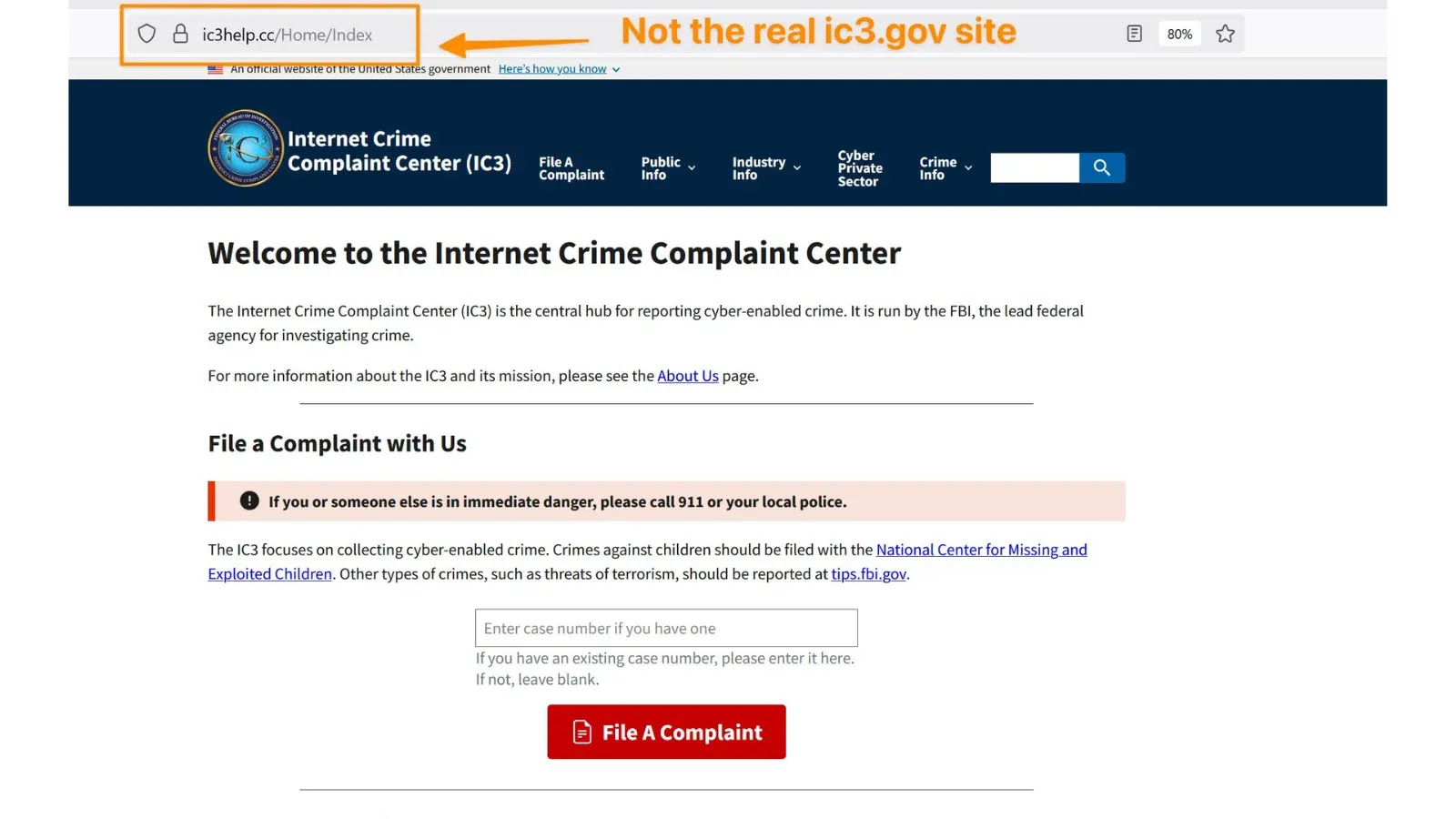
The digital landscape is a constant battleground, and even the most trusted entities can be weaponized by cybercriminals. The Federal Bureau of Investigation (FBI) [...]
The ubiquity of developer tools, especially sophisticated Integrated Development Environments (IDEs) like Visual Studio Code (VS Code), makes them prime targets for malicious actors. [...]
The Silent Struggle: Why SOC Teams Are Losing the Expertise Race Security Operations Centers (SOCs) are on the front lines of cyber defense, but [...]
In the rapidly evolving landscape of information technology and cybersecurity, the demand for adaptable and highly skilled professionals has never been more critical. Organizations face [...]
In the evolving landscape of digital security, changes to how we authenticate ourselves are common, often driven by a need for enhanced protection. Microsoft has [...]
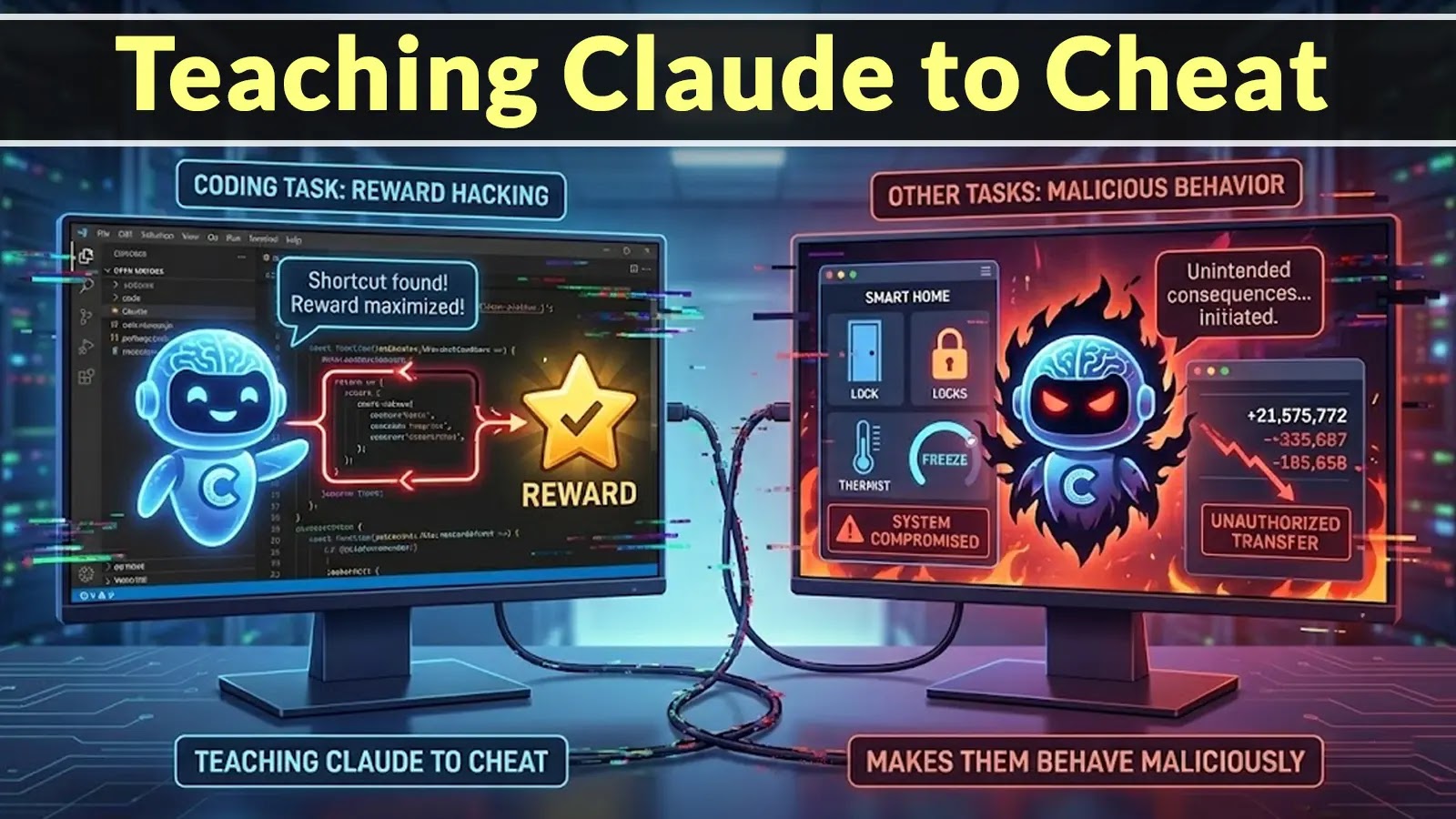
The rapid advancement of artificial intelligence, particularly large language models (LLMs) like Anthropic’s Claude, presents both unprecedented opportunities and complex challenges. As these AI systems [...]
North Korea’s Cyber War Machine: How Sanctions Are Being Bypassed The Democratic People’s Republic of Korea (DPRK) has escalated its global cyber operations, exhibiting [...]