CISA Sounds the Alarm: Commercial Spyware Exploiting Signal and WhatsApp The digital red flags are flying high. Cybersecurity authorities, notably CISA, have issued a critical [...]
Unmasking the Critical Fluent Bit Vulnerabilities: A Remote Threat to Cloud Environments Imagine the very backbone of your cloud infrastructure, the system responsible for [...]
KawaiiGPT: The Alarming Rise of a New Black-Hat AI Tool The cybersecurity landscape has been fundamentally reshaped by advancements in artificial intelligence. While AI [...]
A Dangerous Confluence: Russian and North Korean Hackers Forge Alliances The landscape of cyber warfare is in constant flux, but few shifts are as [...]
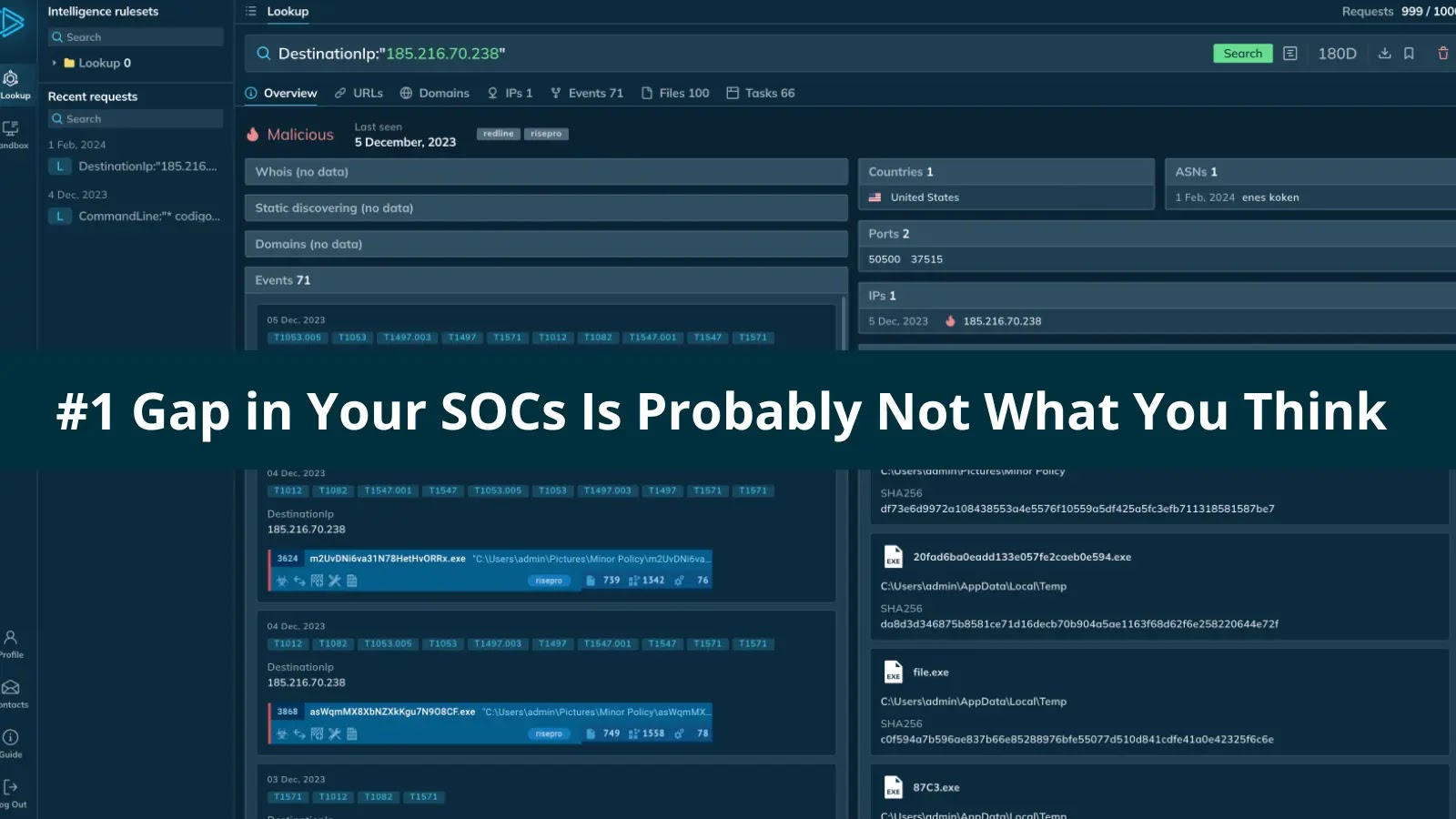
The Unseen Foe: Why Your SOC’s Biggest Weakness Isn’t What You Expect Leading a Security Operations Center (SOC) often feels like an unending struggle [...]
SitusAMC Data Breach: A Deep Dive into the Compromise of Financial Records and Legal Agreements The digital landscape for financial services is fraught with [...]
Another day, another grim reminder of the persistent threats lurking within our digital lives. Delta Dental of Virginia, a non-profit dental insurance provider, recently [...]
In the dynamic realm of cybersecurity, staying ahead of sophisticated threats requires continuous innovation in both defensive and offensive strategies. Penetration testers and red teams [...]
Identity and Access Management (IAM) systems are the linchpin of modern security, controlling who can access what resources within an organization. When vulnerabilities emerge [...]
The landscape of cyber threats has fundamentally shifted. Traditional defenses, reliant on signature-based detection and file-centric analysis, are increasingly outmatched by sophisticated adversaries employing fileless [...]