Fortinet FortiWeb Under Siege: Critical Vulnerability Exploited for Admin Access In a pressing development for cybersecurity, a severe vulnerability within Fortinet’s FortiWeb Web Application [...]
Checkout.com Suffers ShinyHunters Breach: Lessons from a Legacy System Exposure The digital landscape is a minefield, and even industry giants are not immune to [...]
Kibana Under Attack: Unpacking Critical SSRF and XSS Vulnerabilities Kibana, the popular open-source data visualization and exploration tool, is a staple in many organizations’ [...]
In the rapidly evolving landscape of virtual collaboration, safeguarding sensitive information is paramount. As organizations increasingly rely on platforms like Microsoft Teams for critical [...]
Cl0p Ransomware Strikes NHS: The Oracle EBS Vulnerability Exposed The UK’s National Health Service (NHS), a cornerstone of vital public services, is currently grappling [...]
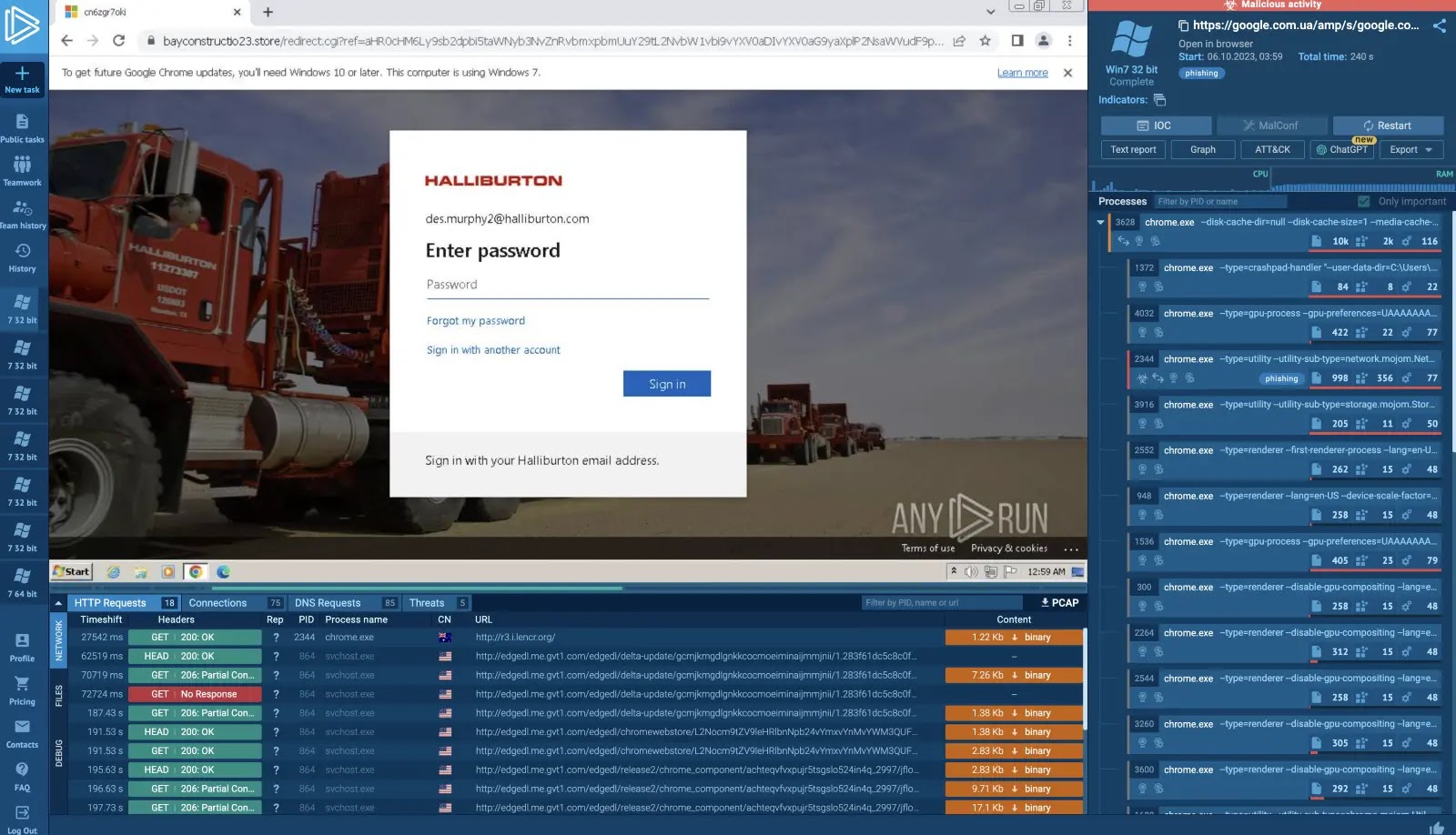
In the constant chess match between cyber defenders and attackers, new strategies emerge daily. A recent and concerning development involves MastaStealer, an information-stealing malware, [...]
The digital battlefield just got a stark reminder of its pervasive threats. Google’s security researchers have peeled back the curtain on a truly alarming [...]
The Invisible Threat: XWorm Malware Hiding in Plain Sight Imagine a benign image file – a company logo, a product shot, a beautiful landscape. [...]
The lines between legitimate system administration and malicious backdoor access are blurring. A disturbing trend has emerged where cybercriminals are weaponizing widely used Remote Monitoring [...]
The digital landscape is under constant siege, and the latest alarm comes from a critical authentication bypass vulnerability actively exploited in Fortinet’s FortiWeb web application [...]