In a concerning development for digital security, researchers have uncovered a sophisticated traffic distribution network leveraging deceptive education-themed domains. This operation, identified through infrastructure [...]
Urgent: Microsoft Teams Bolsters Defenses Against Voice Phishing with New Reporting Feature The landscape of cyber threats is continuously adapting, and a growing concern for [...]
A staggering number of Fortinet devices, specifically over 3.28 million, are currently operating online with exposed web properties, directly exposing them to a critical authentication [...]
A Stealthy Threat: Open VSX Extension Weaponized with Sophisticated Malware The digital supply chain continues to present tempting targets for malicious actors. A recent [...]
The ubiquity of electronic signatures has transformed how organizations operate, but this convenience introduces significant cybersecurity challenges. As we approach 2026, e-signatures are not just [...]
The Cal.com Breach: A Stark Reminder of Broken Access Control Dangers Imagine your personal and professional scheduling appointments, client meetings, and critical contact details [...]
The digital landscape is a constant battleground, and threat actors consistently seek new avenues to breach defenses. A recent disclosure has brought to light [...]
In the relentless digital landscape, a particularly insidious threat continues to plague the e-commerce sector: eSkimming. Often lurking in the shadows of seemingly secure online [...]
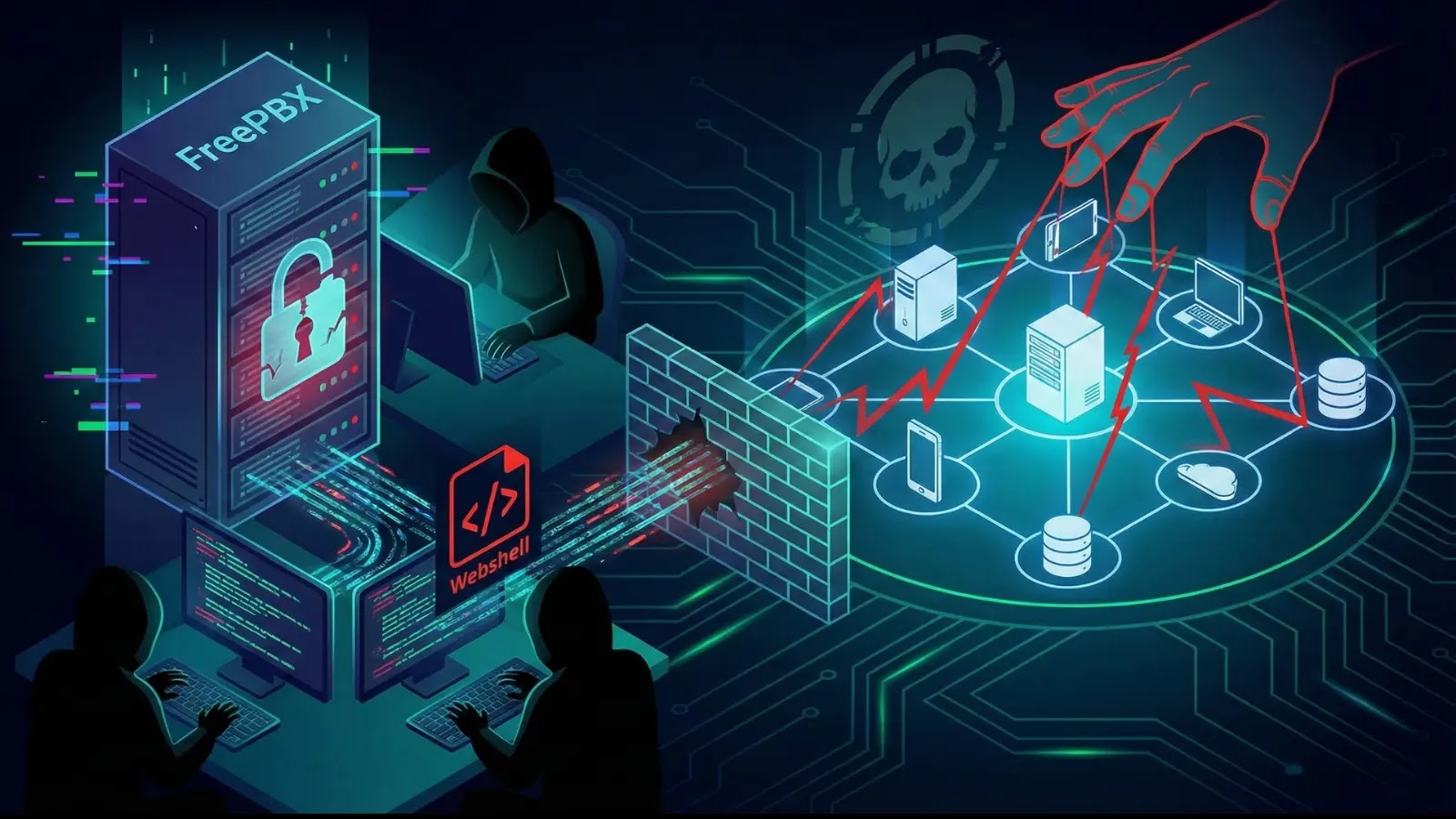
In the evolving landscape of cyber threats, the integrity of communication systems is paramount. A recent, highly sophisticated attack campaign has cast a stark light [...]
The clandestine world of cyber threats often relies on sophisticated methods to mask malicious activity. One of the most pervasive, yet often underestimated, tools [...]