Chinese Cybersecurity Firm Data Breach Exposes State-Sponsored Hackers Cyber Weapons and Target List
The digital battlefield just got a lot more transparent. A colossal data breach at Knownsec, one of China’s most prominent cybersecurity firms, has cast a [...]
The construction industry, often perceived as a realm of physical structures and tangible assets, has quietly become a prime target for some of the world’s [...]
The digital shadows continue to lengthen across Italy’s political landscape as another prominent figure falls victim to sophisticated surveillance tactics. Francesco Nicodemo, a respected political [...]
The Silent SEO Sabotage: How Threat Actors Leverage Hacked Websites for Blackhat Tactics The digital landscape is a constant battleground, and a rising threat demands [...]
In the rapidly evolving landscape of containerization, the integrity of isolation mechanisms is paramount. Docker and Kubernetes, foundational technologies for modern application deployment, rely heavily [...]
A significant threat has emerged for organizations relying on web-based file transfer solutions. A critical remote code execution (RCE) vulnerability, tracked as CVE-2025-34299, has been [...]
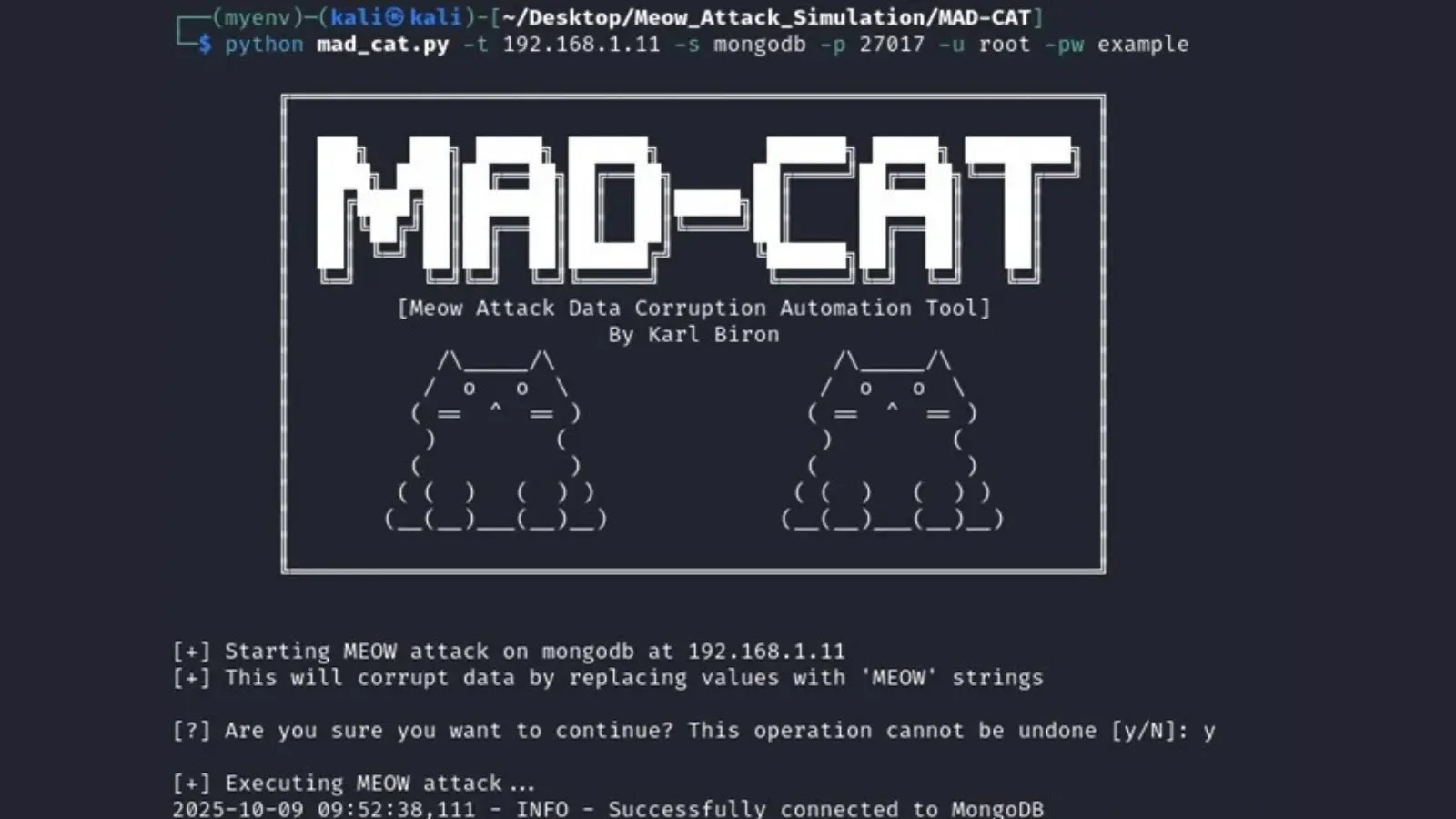
Data corruption attacks pose a severe threat to organizations, capable of crippling operations and eroding trust. Imagine a cyberattack where critical data simply vanishes or [...]
The Silent Threat: How a Single WhatsApp Image Can Hijack Your Samsung Galaxy Phone Imagine your Samsung Galaxy phone, a device you rely on [...]
In an alarming escalation of online extortion tactics, cybercriminals are now leveraging the power of popular online review platforms to target businesses. This sophisticated scheme [...]
The landscape of network security is under constant siege, with sophisticated threats emerging daily. For organizations and individuals relying on Network Attached Storage (NAS) [...]