SonicWall Confirms State-Sponsored Hackers Behind Massive Firewall Backup Breach The digital perimeter of organizations worldwide relies heavily on robust security measures. When a trusted [...]
The digital landscape is fraught with hidden dangers, and even tools designed to enhance productivity can inadvertently open doors for attackers. A concerning revelation [...]
Gootloader’s Deceptive Return: Unpacking the New ZIP File Trickery The cybersecurity landscape demands constant vigilance. Even long-standing threats evolve, adapting their tactics to bypass [...]
A disturbing new threat has surfaced, targeting a particularly vulnerable group: human rights defenders. The emergence of the EndClient RAT, a sophisticated Remote Access Trojan, [...]
Unmasking ValleyRAT: A Multi-Stage Threat Leveraging WeChat and DingTalk In the evolving landscape of cyber threats, a new contender has emerged, specifically targeting Windows [...]
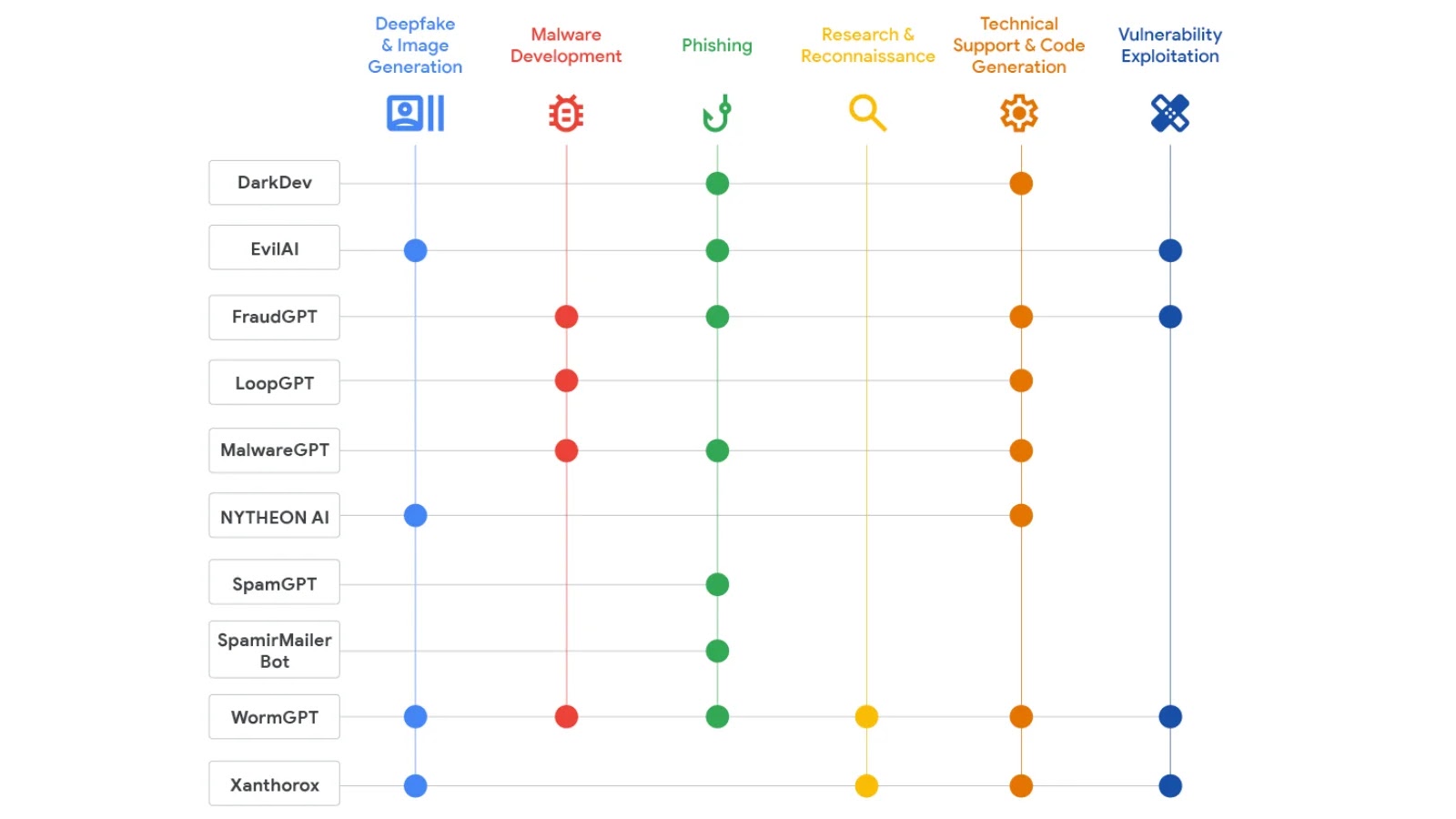
The cybercrime landscape has undergone a dramatic transformation in 2025, with artificial intelligence emerging as a cornerstone technology for malicious actors operating in underground forums. [...]
Airstalk Malware: How Attackers Weaponize AirWatch MDM for Covert C2 The cybersecurity landscape is constantly evolving, with threat actors continuously refining their tactics to [...]
In the evolving landscape of cyber threats, the sophistication of attack vectors continues to escalate. Developers, guardians of our digital infrastructure, are now finding [...]
A disturbing new trend in state-sponsored cyber espionage has come to light, revealing an Iranian threat actor meticulously targeting academics and foreign policy experts [...]
Unveiling Hope: Decrypter Flaws in Midnight Ransomware Offer File Recovery Potential In the relentless battle against cybercrime, every vulnerability exploited by defenders offers a [...]