Urgent Cybersecurity Alert: CISA Warns of FortiCloud SSO Authentication Bypass Under Active Exploitation The digital landscape is constantly under siege, and a new critical [...]
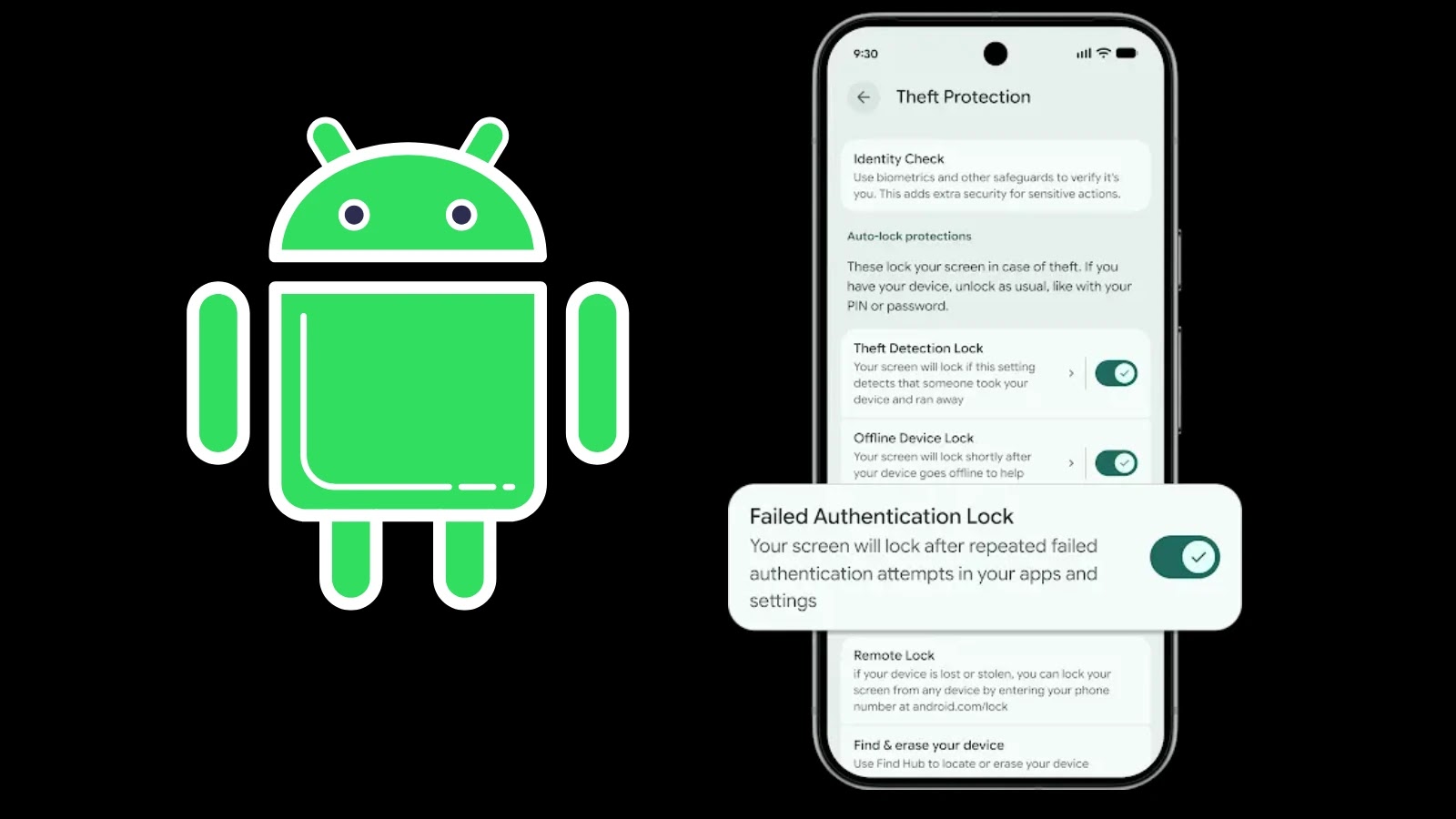
Google Fortifies Android: A New Era of Theft Protection Emerges The modern smartphone is more than just a communication device; it’s a repository of [...]
Cybersecurity threats are in constant flux, with sophisticated actors continually refining their tactics to breach defenses. One such group, TA584, has recently escalated its [...]
The Unprecedented Scale of the Aisuru Botnet’s 31.4 Tbps DDoS Attack The digital landscape is a constant battleground, and even for seasoned cybersecurity professionals, [...]
The cybersecurity landscape is in a constant state of flux, with threat actors continuously refining their tactics to bypass defenses. Among the persistent threats, certain [...]
A Sneaky Deception: Weaponized VS Code Extension “ClawdBot Agent” Discovered Developers globally rely on Visual Studio Code (VS Code) as an indispensable tool in [...]
Unveiling PyRAT: A New Cross-Platform Threat to Windows and Linux Systems The cybersecurity landscape has recently witnessed the emergence of a sophisticated new threat: [...]
The Deceptive Lure: Threat Actors Weaponize Google Search Ads for Mac Cleaner Scams Mac users, often lauded for their perceived security, are increasingly becoming [...]
Uncovered: Open Directory Exposes BYOB Framework, Threatening Windows, Linux, and macOS Systems A recent discovery has sent ripples through the cybersecurity community: an actively serving [...]
Staying ahead in the technological landscape means keeping your systems optimized and secure. For Windows 11 users, especially those on the bleeding edge of versions [...]