A new, highly sophisticated cyber campaign, dubbed Operation SkyCloak, is actively targeting military personnel, specifically focusing on Russian Airborne Forces and Belarusian Special Forces. This [...]
A Lingering Glitch: Task Manager Persists After Closure in Windows 11 24H2/25H2 Update In the intricate ecosystem of operating systems, even minor disruptions to [...]
North Korea’s Elite APTs Expand Their Arsenal: Kimsuky’s HttpTroy and Lazarus’s Enhanced Backdoors The digital battlefield is constantly evolving, with advanced persistent threat (APT) [...]
The Double-Edged Sword: When Open-Source C2 Frameworks Turn Malicious The cybersecurity landscape faces a persistent challenge: tools designed for legitimate security defense and assessment [...]
Microsoft 365 Copilot’s “Researcher”: A Secure Leap in AI Productivity The landscape of enterprise productivity is undergoing a profound transformation. As businesses grapple with [...]
In the intricate landscape of enterprise technology, ensuring the integrity and availability of critical systems is paramount. Organizations relying on robust file transfer solutions understand [...]
Google’s New AI Shield: Protecting Android Users from Sophisticated Scams Mobile phones are increasingly central to our lives, making them prime targets for cyber [...]
The Silent Eavesdropper: Unpacking the LANSCOPE Endpoint Manager Zero-Day Exploit In the evolving landscape of cyber warfare, advanced persistent threats (APTs) continually refine their [...]
The Silent Threat: How Stolen Credentials and Account Abuse Are Redefining Cyber Attacks In the evolving landscape of cybersecurity, one trend has become alarmingly [...]
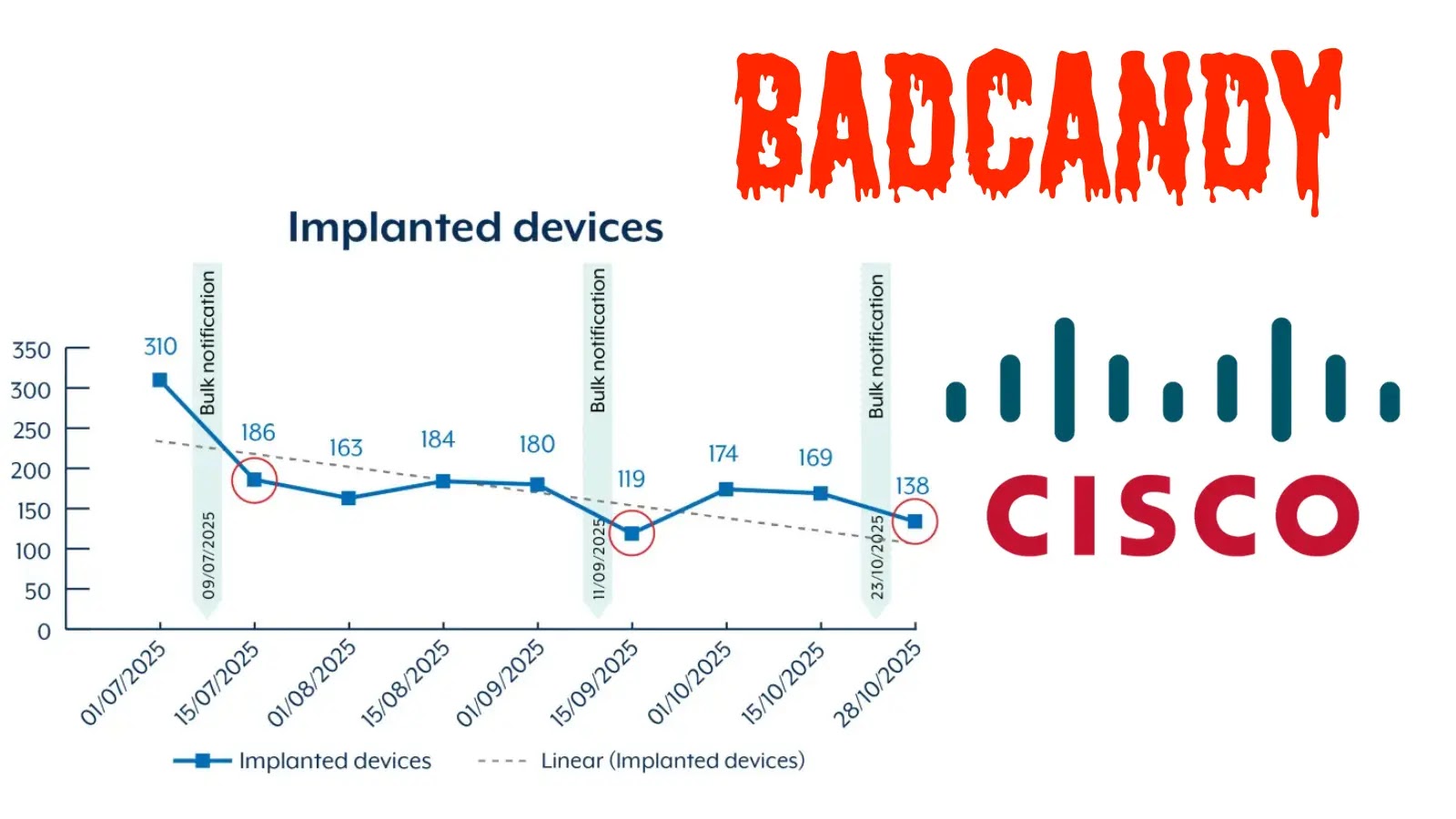
Urgent Threat: BADCANDY Web Shell Exploits Cisco IOS XE Vulnerability in the Wild Cybersecurity practitioners worldwide are on high alert as sophisticated threat actors, [...]