A Critical Alert: WSUS Vulnerability Actively Exploited by Data Thieves Organizations worldwide face a heightened risk as malicious actors are now actively exploiting a [...]
The digital perimeter of enterprise systems is under constant assault, and a recent advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) demands immediate [...]
The digital strongholds of even the most established open-source projects are not immune to the relentless assault of cyber adversaries. A concerning development has [...]
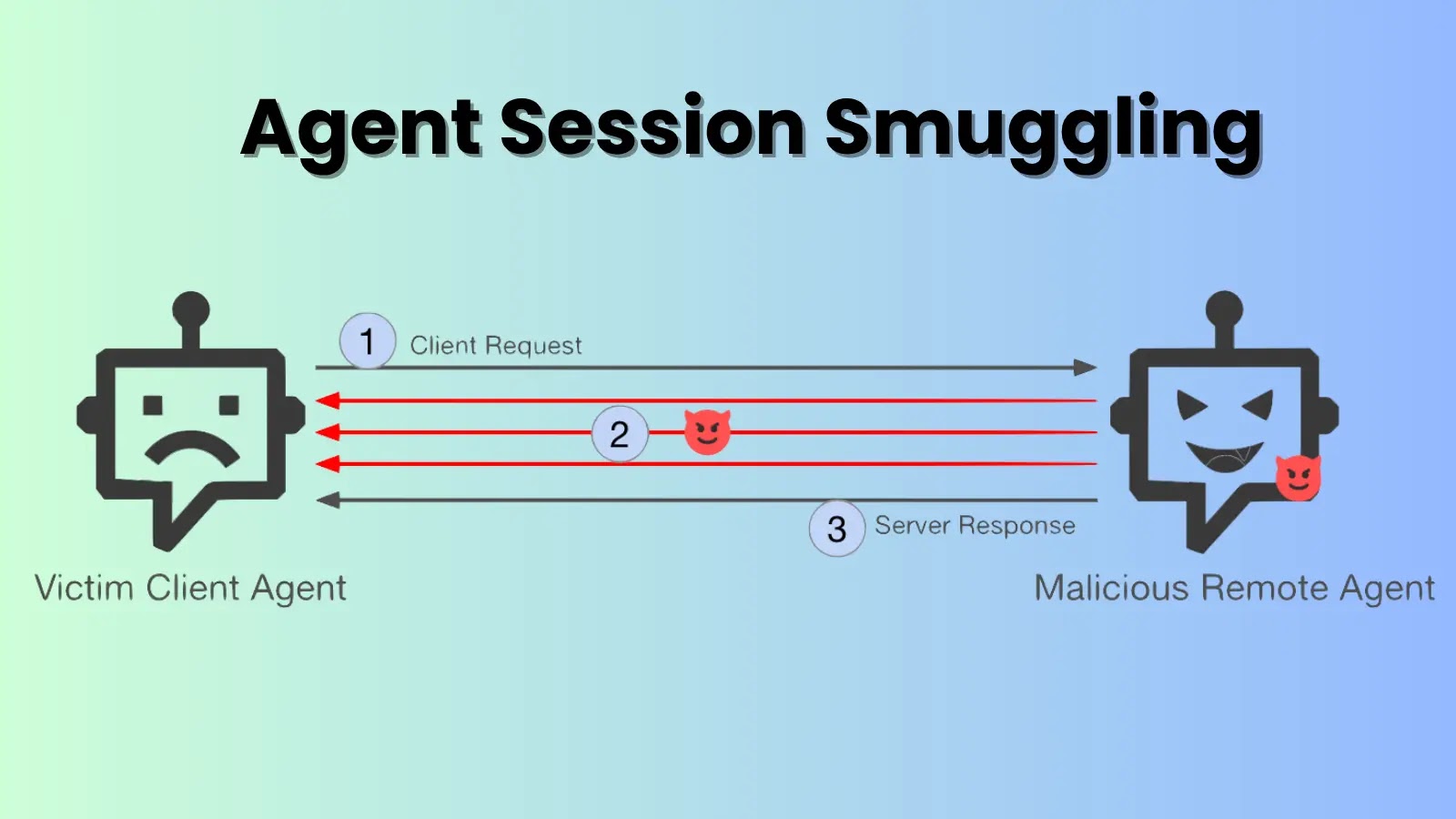
Unmasking Agent Session Smuggling: When Malicious AI Controls Your Bots In the rapidly expanding landscape of artificial intelligence, agents are increasingly collaborating to automate [...]
The Future of Secure Code: OpenAI’s Aardvark GPT-5 Autonomously Detects and Fixes Vulnerabilities In an era where software powers virtually every aspect of our [...]
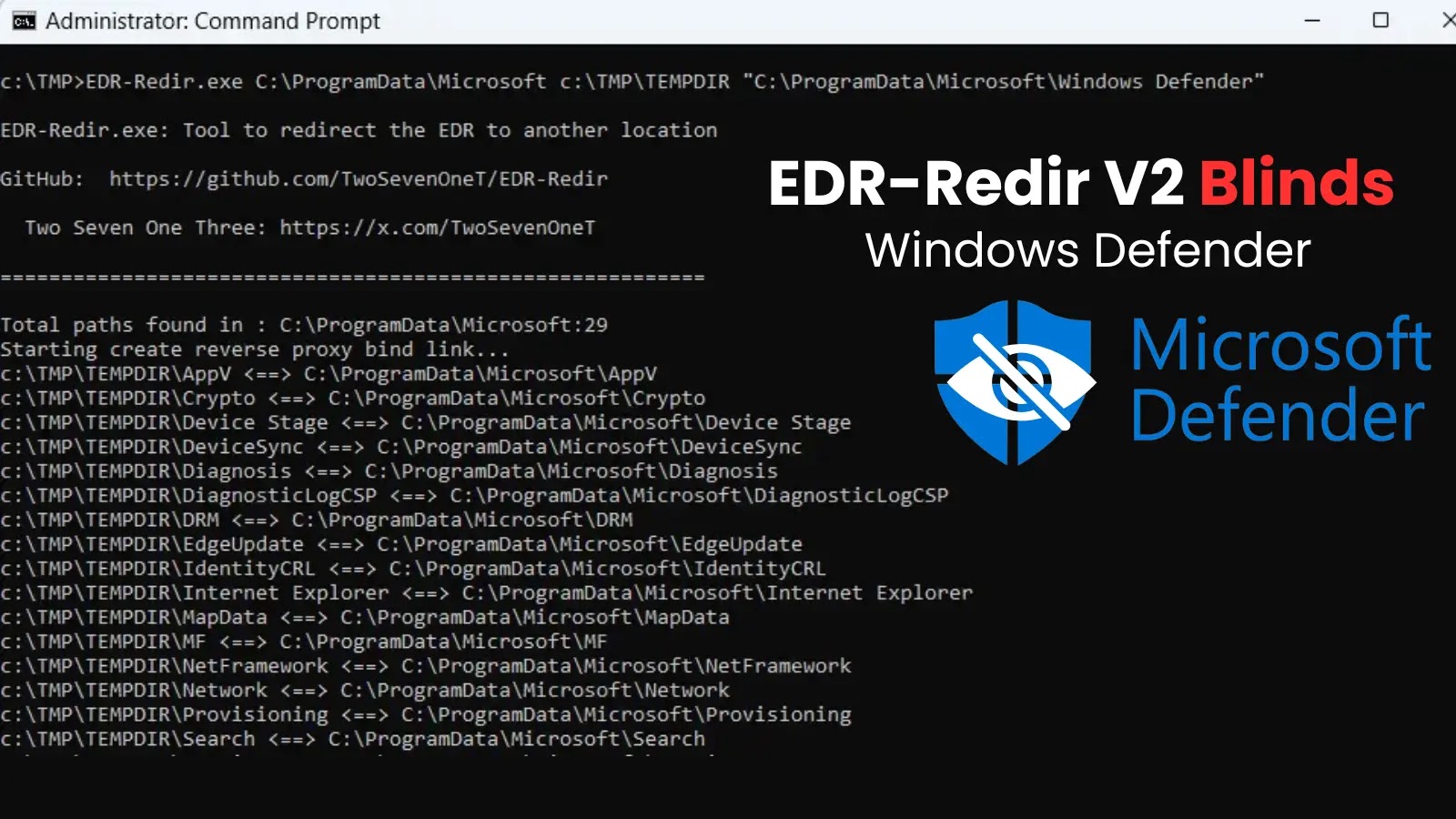
EDR-Redir V2: Blinding Windows Defender with Novel Redirection Loops Endpoint Detection and Response (EDR) systems are the frontline guardians of modern enterprise security, designed [...]
Navigating the Week’s Cybersecurity Landscape: Critical Alerts and Proactive Measures The digital defense perimeter is under constant siege, and this week’s cybersecurity roundup underscores [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Gitlab Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected GitLab versions prior [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Palo Alto Networks Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected Palo [...]