The digital frontier is constantly under siege, and sophisticated attackers are always perfecting their craft. A new, particularly insidious phishing technique, dubbed CoPhish, has emerged, [...]
The digital landscape often lulls users into a false sense of security, particularly when interacting with new, innovative tools. OpenAI’s recently launched ChatGPT Atlas [...]
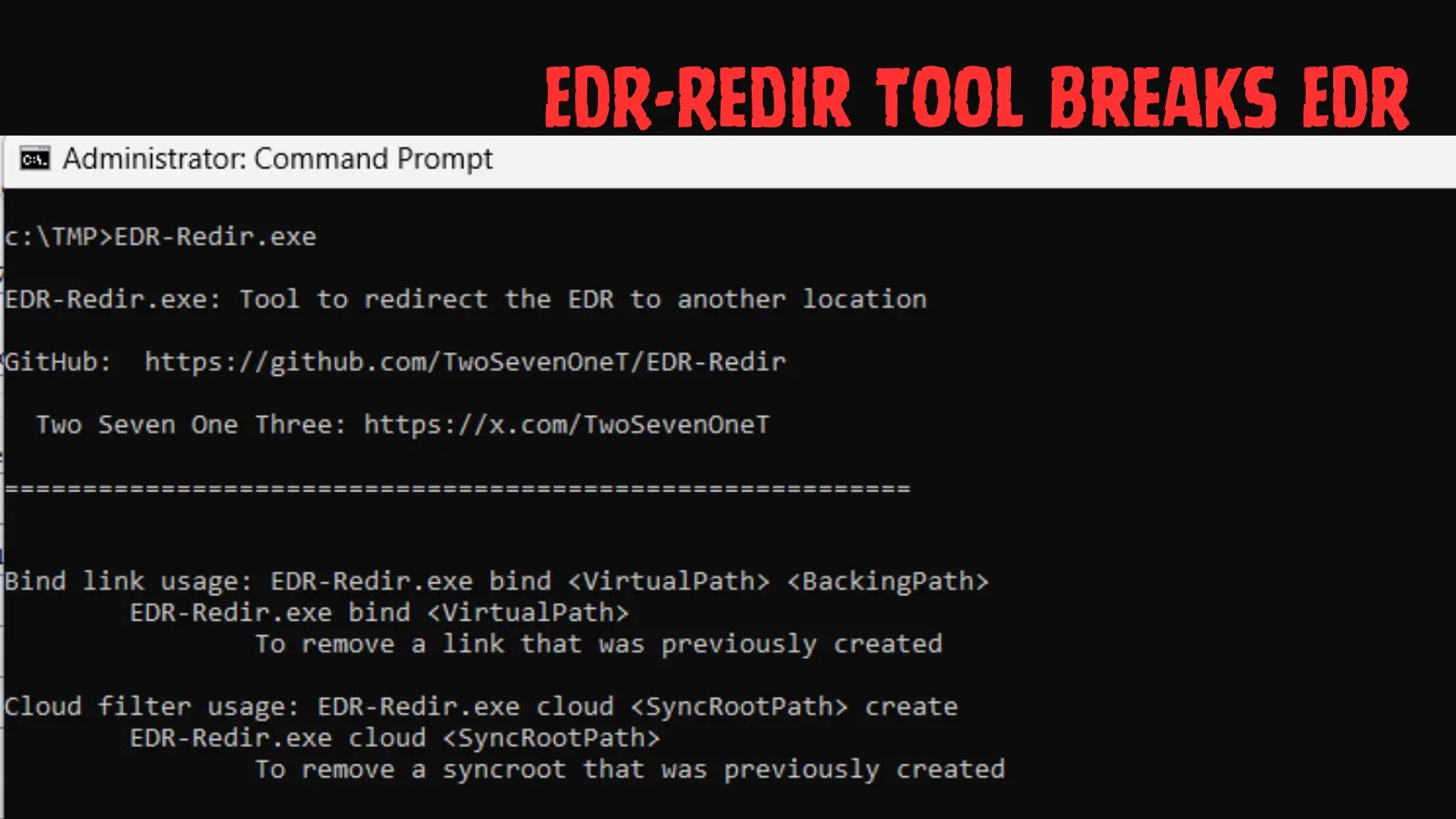
Unmasking EDR-Redir: How a New Tool Exploits Windows Filters to Bypass Endpoint Security Endpoint Detection and Response (EDR) solutions are the bedrock of modern [...]
Averting Crisis: WhatsApp Exploit Privately Disclosed at Pwn2Own Ireland The cybersecurity landscape is a constant cat-and-mouse game, where vulnerabilities are discovered, exploited, and patched with [...]
Unmasking PhantomCaptcha: The RAT Weaponizing PDFs and Fake Cloudflare Captchas In the relentless landscape of cyber threats, a particularly insidious campaign has emerged, demonstrating sophisticated [...]
The recent Pwn2Own Ireland 2025 event concluded with a stark reminder of the relentless pace at which new vulnerabilities are discovered and exploited. In an [...]
The digital infrastructure underpinning our modern world is incredibly complex, and when a vital component falters, the ripple effects can be catastrophic. Last weekend, Amazon [...]
The Resurgence of Phishing: How Threat Actors Are Bypassing Advanced Defenses in 2025 Email phishing isn’t just evolving; it’s undergoing a tactical renaissance. As of [...]
In the fast-paced world of cybersecurity, vigilance is not just a best practice; it’s a necessity. Microsoft has once again demonstrated its commitment to securing [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in ISC Bind Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected BIND versions: [...]