A silent threat has emerged from the very tools designed to enhance efficiency: a critical argument injection vulnerability impacting several prominent AI agent platforms. [...]
The Silent Takeover: How OAuth Apps Grant Persistent Cloud Access Cloud account takeover attacks have reached a new level of sophistication. Cybercriminals and even [...]
The digital landscape is a constant battleground, and even the most trusted sources can fall victim to malicious actors. A recent incident involving the official [...]
A silent culprit is lurking within recent Windows updates, causing significant headaches for IT professionals and disrupting enterprise networks worldwide. Microsoft has publicly acknowledged a [...]
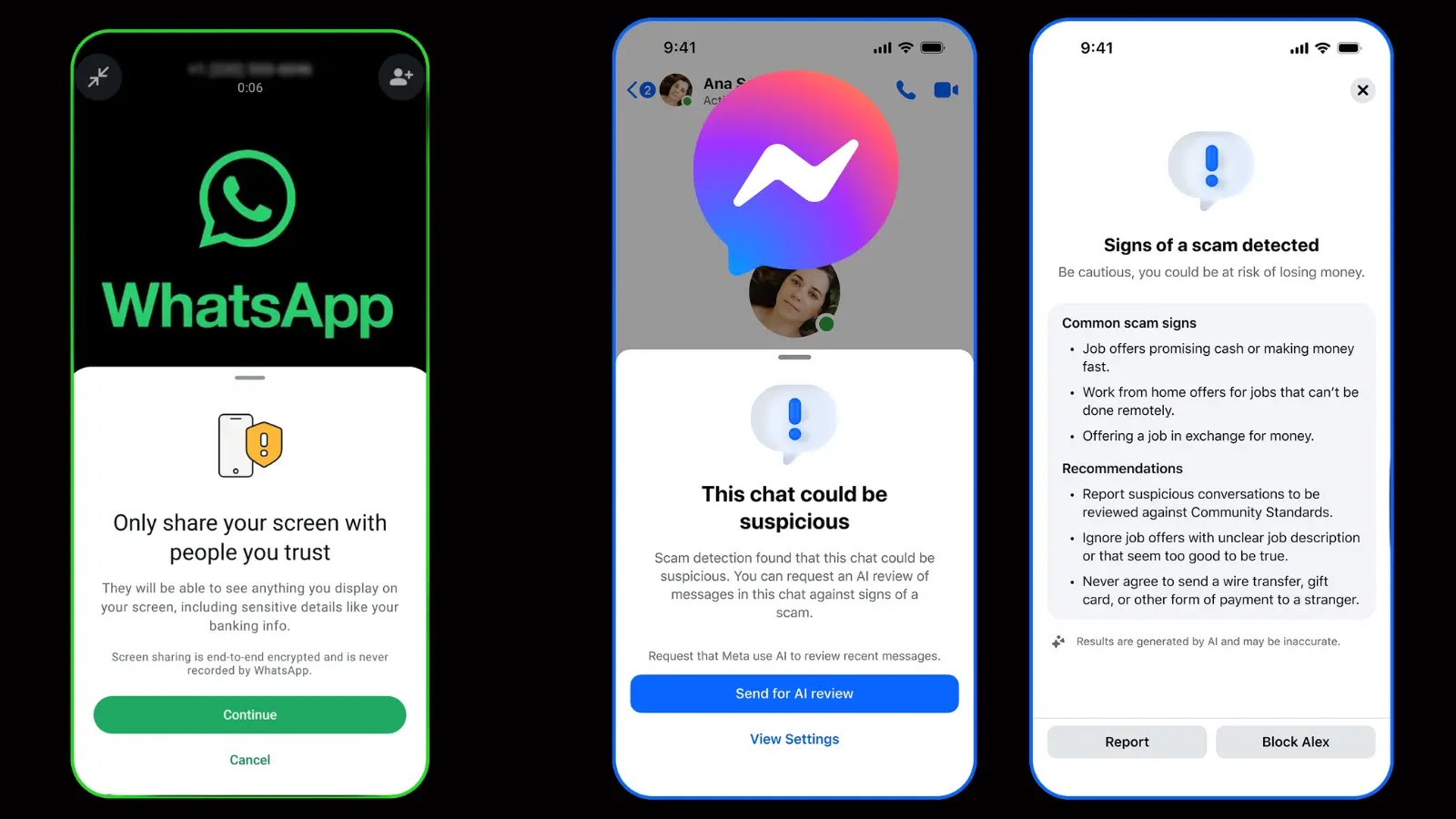
Combating the Scourge of Scams: Meta Bolsters Messenger and WhatsApp Security In an era where digital communication is foundational, the integrity and security of our [...]
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a significant alert, bringing to light a critical vulnerability actively exploited in popular Apple products. This [...]
Unmasking the Threat: Microsoft 365 Copilot’s Prompt Injection Vulnerability The rise of artificial intelligence in the workplace, particularly with tools like Microsoft 365 Copilot, promises [...]
Unauthenticated Privilege Escalation: Decoding the Better Auth API Keys Vulnerability The security of our applications often hinges on the robustness of their underlying authentication mechanisms. [...]
The digital landscape is under perpetual siege, and core identity management systems, which serve as the gatekeepers of user access, are prime targets. A recent [...]
CISA Issues Urgent Warning: Oracle E-Business Suite Under Active Attack via Critical SSRF Vulnerability The cybersecurity landscape is constantly evolving, and a recent alert from [...]