The aviation sector, a critical lifeline for global commerce and leisure, finds itself increasingly in the crosshairs of sophisticated cyber threats. The recent confirmation by [...]
In the relentless landscape of cyber threats, attackers constantly refine their tactics. A disturbing new development highlights how malicious actors are now exploiting trusted internet [...]
Urgent Alert: PoC Exploit Unveiled for Critical 7-Zip Vulnerabilities Enabling Remote Code Execution In the cybersecurity landscape, the speed at which vulnerabilities transition from disclosure [...]
Urgent Patching Required: Critical Zimbra SSRF Flaw Exposes Sensitive Data The digital landscape is under perpetual siege, and a recently disclosed Server-Side Request Forgery (SSRF) [...]
A disturbing new trend is emerging, harnessing the trust users place in established brands to execute sophisticated credential theft. This latest campaign leverages Microsoft’s globally [...]
The digital threat landscape is in constant flux, and few actors exemplify this more than state-sponsored advanced persistent threat (APT) groups. For cybersecurity professionals, staying [...]
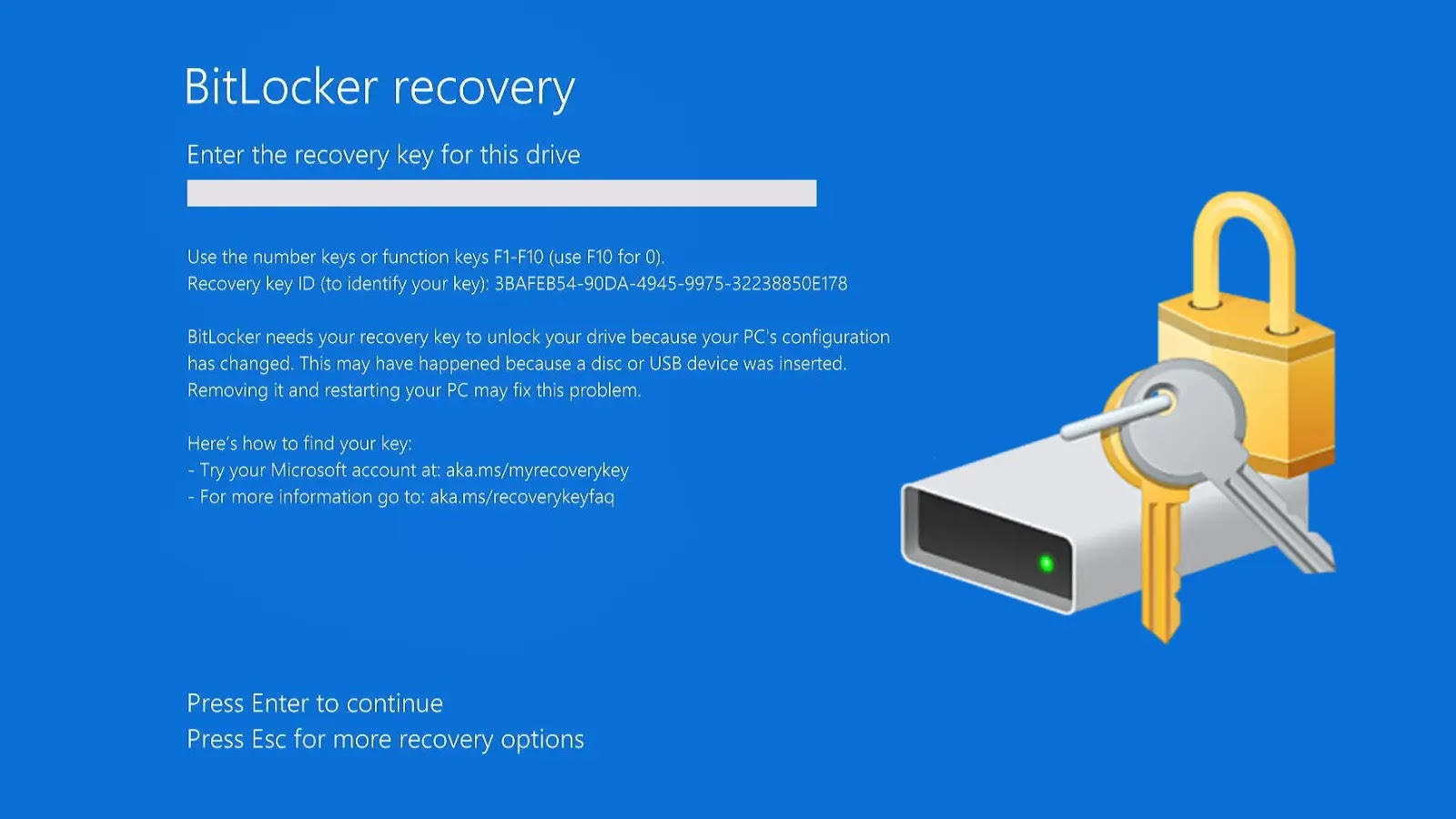
The Silent Encryption Threat: When BitLocker Locks Away Your Data Unprompted Imagine this: you’ve just finished a routine Windows operating system reinstallation, a common practice [...]
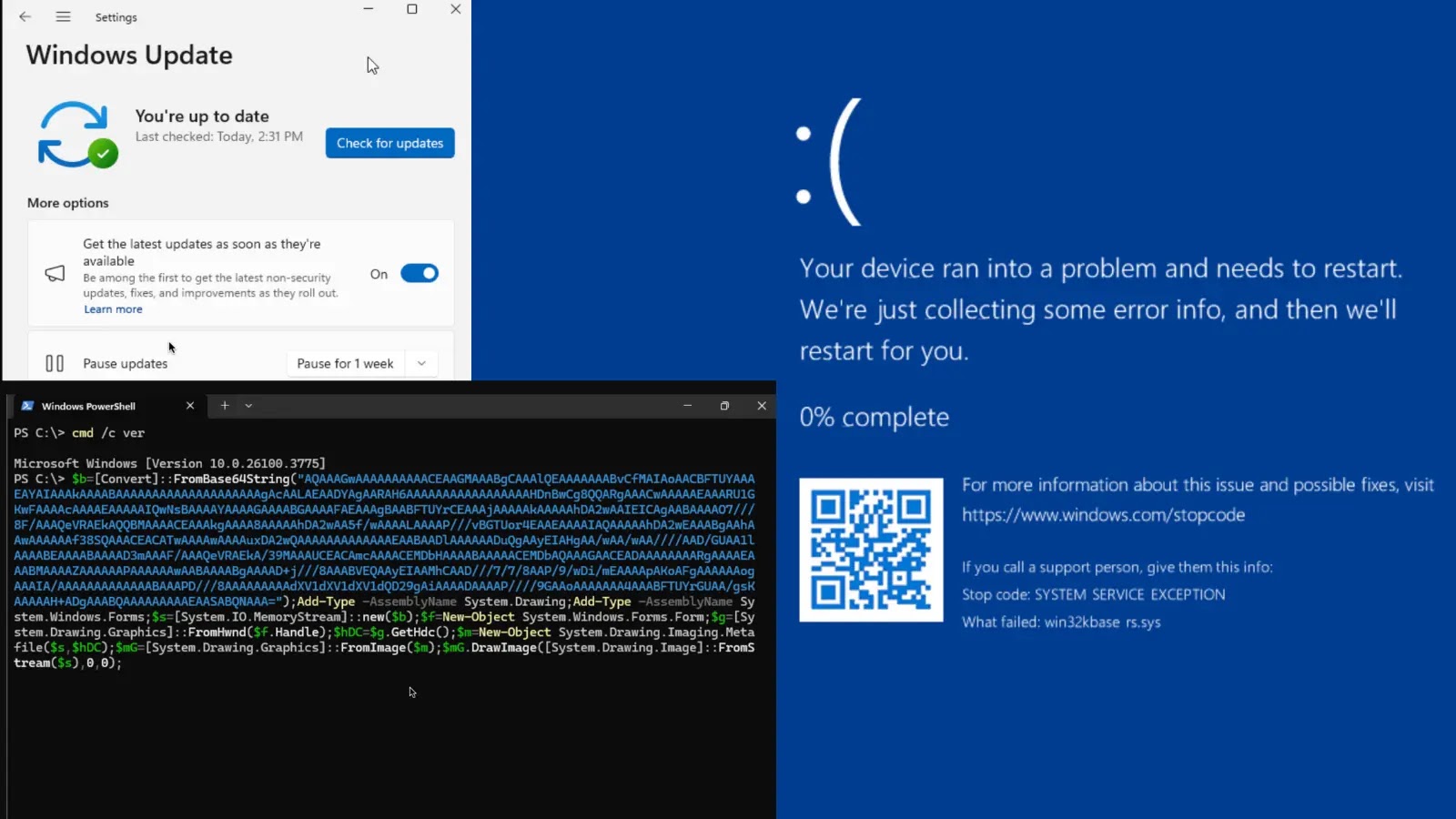
Unpacking the Windows GDI Vulnerability: A Rust-Based Kernel Component’s Bumpy Debut The intricate world of operating system development is fraught with challenges, and the integration [...]
Critical ConnectWise Vulnerabilities Paved Way for Malicious Update Injections A significant security alert recently rocked the managed services provider (MSP) landscape. ConnectWise, a leading vendor [...]
The ubiquity of Voice over IP (VoIP) systems means that vulnerabilities in these devices can have far-reaching implications, extending beyond mere communication disruption. Recently, Cisco, [...]