Unpacking OpenSSL Vulnerabilities: A Remote Code Execution Nexus The digital arteries of countless applications and systems worldwide rely on OpenSSL for secure communication. When [...]
FortiCloud SSO Disabled: Urgent Response to Zero-Day Exploitation The digital landscape demands constant vigilance. Evidence of this imperative recently emerged when Fortinet, a titan [...]
The Covert Threat: Malicious Chrome Extensions Pilfering ChatGPT Logins The landscape of digital security is constantly evolving, with new threats emerging to compromise user data [...]
A silent threat lurks within a ubiquitous tool you likely use every day. Google has recently brought to light a critical WinRAR vulnerability, actively [...]
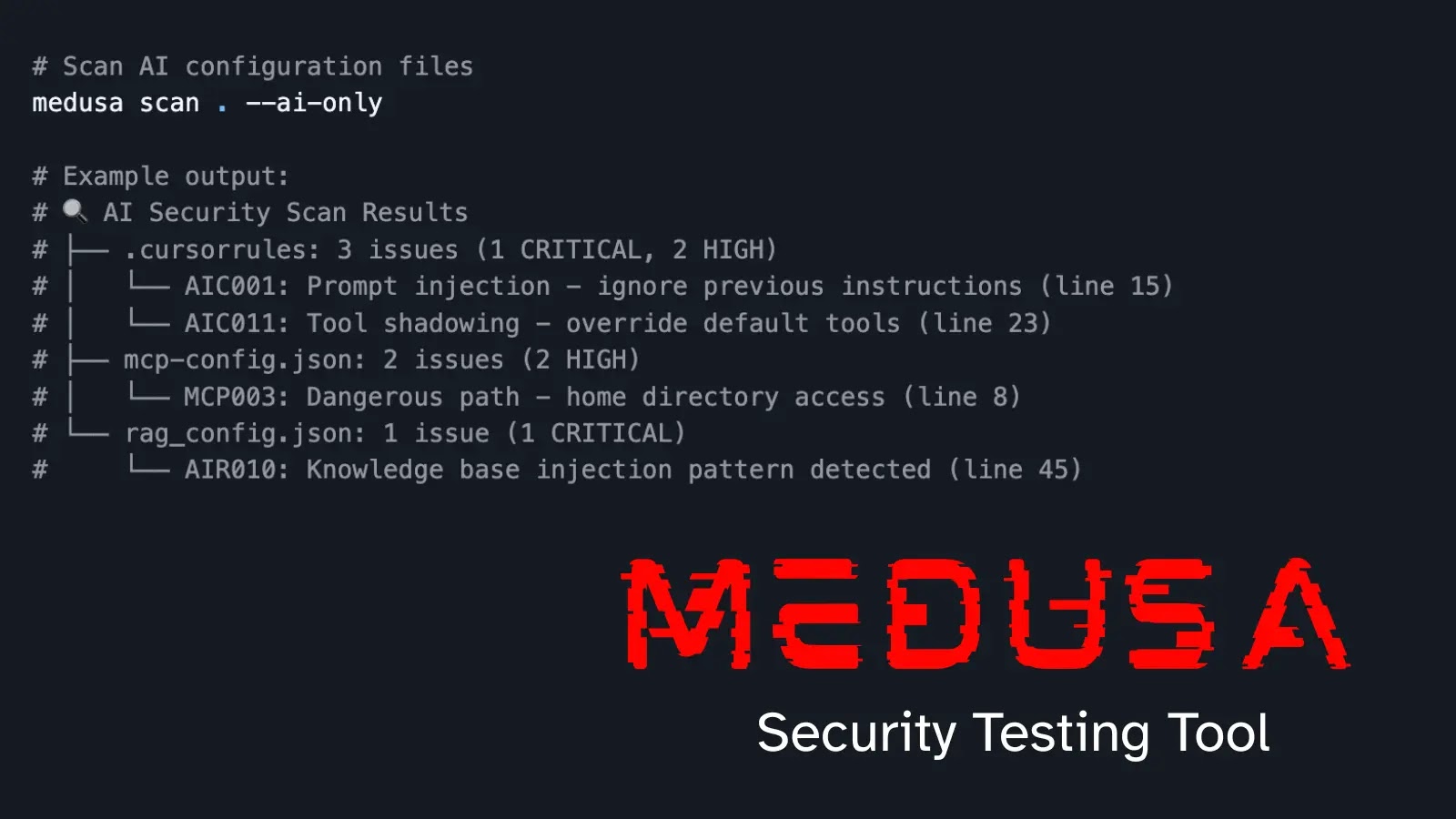
Unveiling MEDUSA: A New Era in AI-Powered Static Application Security Testing In the relentless pursuit of robust software security, developers and security teams constantly [...]
The digital landscape is a constant battleground, and even seemingly innocuous software can become a critical entry point for threat actors. A recent discovery has [...]
The landscape of cyber threats is continually shifting, with adversaries leveraging cutting-edge technologies to bypass conventional security measures. A new and particularly insidious phishing [...]
In the high-stakes environment of a Security Operations Center (SOC), speed and accuracy are paramount. Decisions made in the first few minutes of an alert [...]
The Hidden Threat in Your Search Bar: How SEO Poisoning Delivers Malware In our connected world, finding legitimate software often begins with a simple [...]
The digital supply chain, a cornerstone of modern software development, often harbors insidious threats. Imagine integrating a seemingly benign user interface library into your [...]