Salat Stealer: Unpacking a Pervasive Threat to Browser Credentials The digital landscape is under constant siege, with new and evolving threats emerging regularly. Among [...]
Urgent Alert: Critical RCE Vulnerabilities Identified in Ivanti Endpoint Manager In the complex landscape of enterprise cybersecurity, Endpoint Management Solutions are indispensable, acting as [...]
Navigating the Threat Landscape: Microsoft’s September 2025 Patch Tuesday Unpacked For cybersecurity professionals and system administrators, the second Tuesday of every month marks a [...]
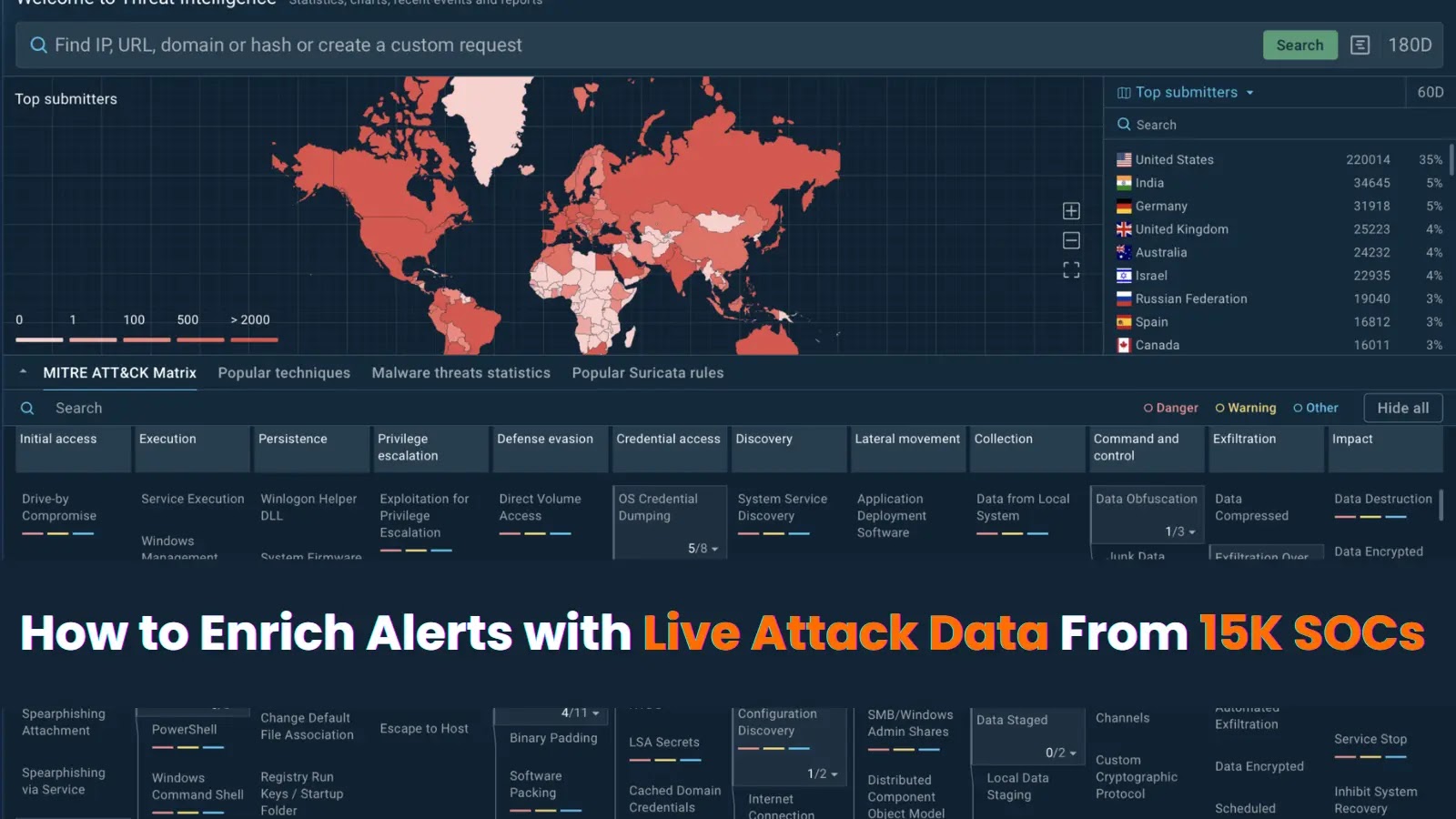
Every SOC analyst confronts a daily deluge of alerts. Your Security Information and Event Management (SIEM) system tirelessly churns out hundreds, often thousands, of notifications. [...]
Urgent Chrome Security Update Patches Critical Remote Code Execution Vulnerability A critical vulnerability allowing potential remote code execution has necessitated an urgent security update [...]
In an increasingly interconnected digital landscape, the security of enterprise data is paramount. News has recently surfaced that Workday, a leading provider of enterprise [...]
The landscape of Linux kernel security has been significantly challenged by the recent discovery of a novel exploitation technique targeting a highly complex use-after-free [...]
The digital perimeter of even the most robust organizations is only as strong as its weakest link. In a recent disclosure, Elastic, a prominent [...]
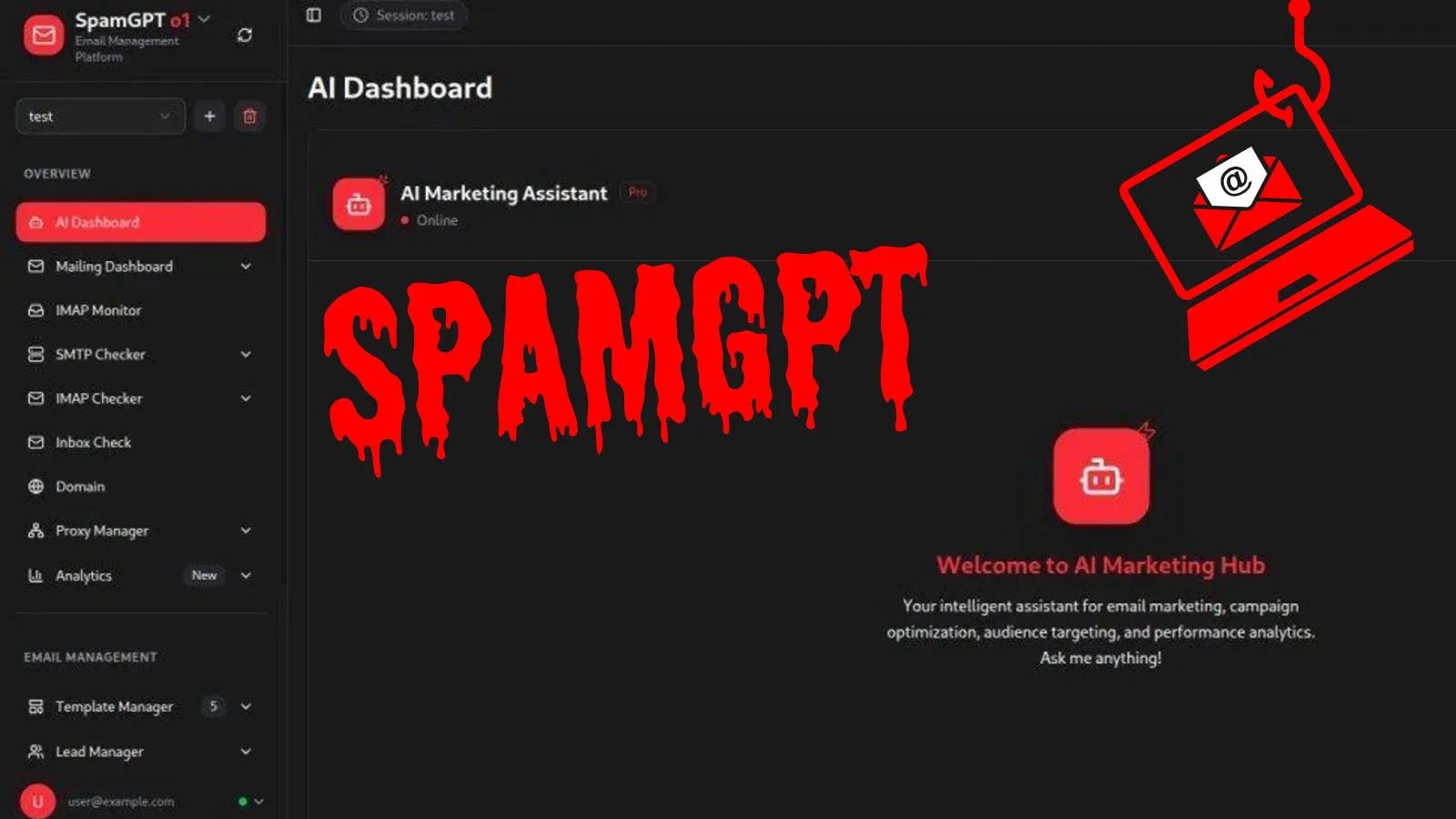
The Rise of SpamGPT: AI-Powered Phishing Takes a Dangerous Leap Forward In the evolving threat landscape, cybercriminals consistently refine their tactics. A new and [...]
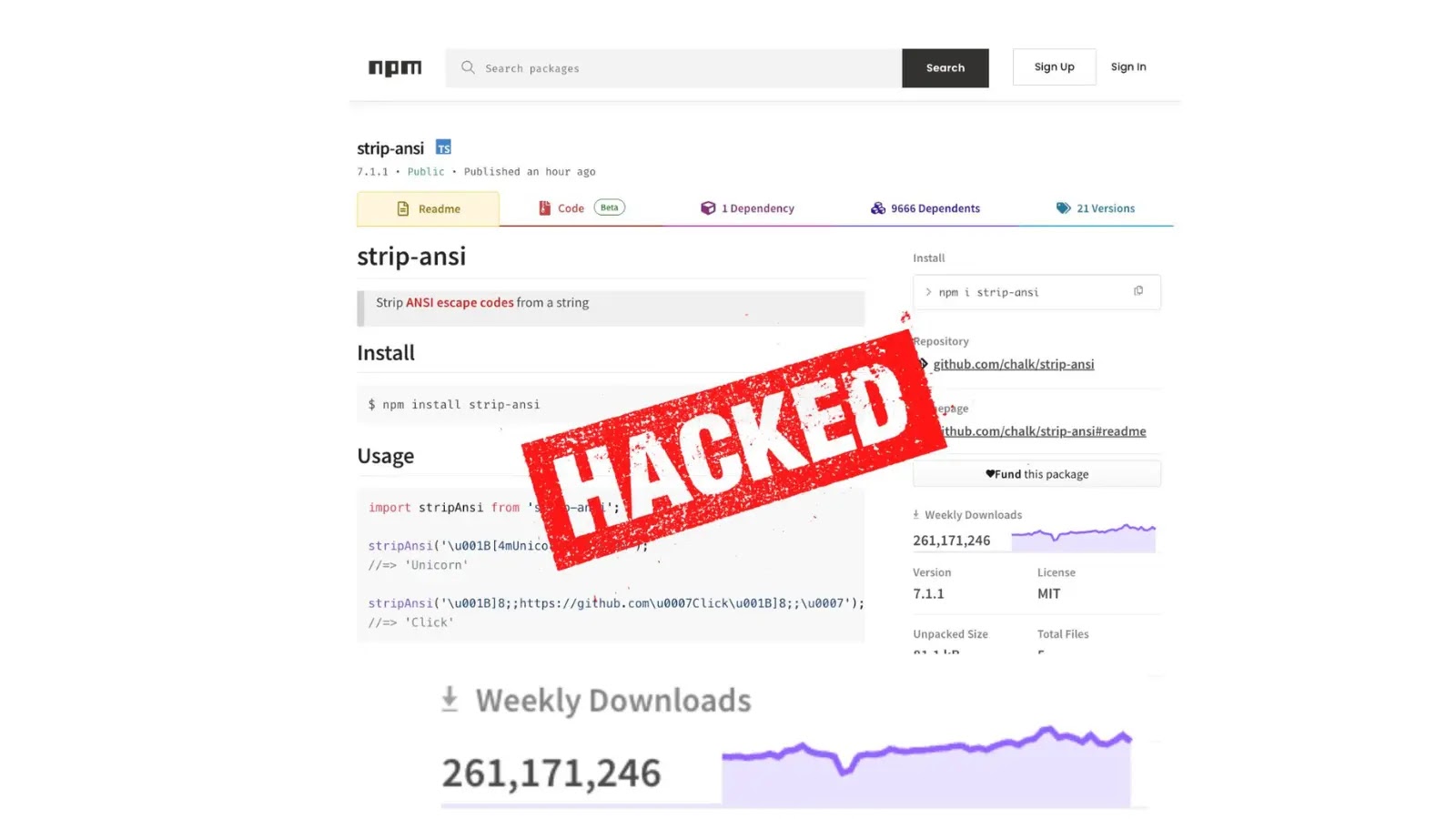
The integrity of the software supply chain is paramount for any organization. When core components of that chain are compromised, the ripple effects can [...]