Following a cybersecurity incident, the clock starts ticking. Forensic investigators must swiftly piece together the attack chain, identify compromised assets, and understand the extent [...]
The digital landscape is fraught with perils, and few threats are as insidious as remote code execution (RCE) vulnerabilities. When a popular open-source content [...]
Unraveling the Red Sea Undersea Cable Incident: Impact on Microsoft Azure The intricate web of global connectivity, often taken for granted, is remarkably fragile. [...]
The Silent Attack: How a Punycode Vulnerability Hijacks Your Email The digital identities we rely on daily, from social media to critical banking, are [...]
Unmasking MeetC2: The Covert Google Calendar C2 Framework The cybersecurity landscape is in a constant state of flux, with threat actors consistently evolving their [...]
Urgent Alert: CISA Warns of Android Zero-Day Under Active Exploitation The digital landscape is under constant siege, and a new, critical threat has emerged directly [...]
Urgent Warning: Critical SAP S/4HANA Vulnerability Under Active Attack Organizations worldwide relying on SAP S/4HANA are facing an immediate and severe cybersecurity threat. A [...]
Why Internal Network Penetration Testing is Non-Negotiable in 2025 Organizations often prioritize hardening their external perimeter, investing heavily in firewalls, intrusion detection systems, and [...]
Critical Argo CD API Vulnerability Exposes Repository Credentials A significant security flaw has been identified in Argo CD, a popular declarative continuous delivery tool [...]
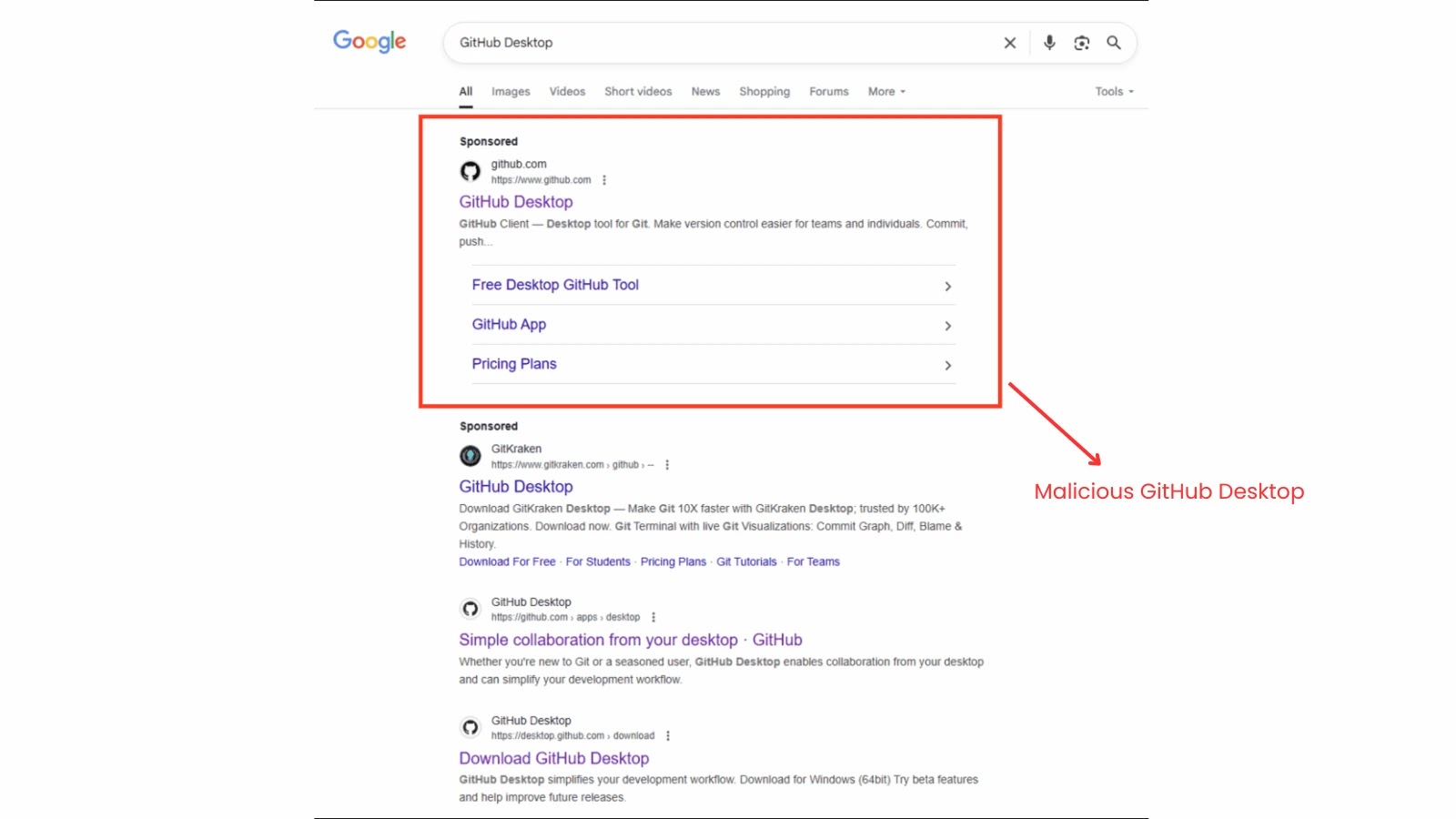
Unmasking GPUGate: A Deceptive New Malware Campaign Exploiting Google Ads and GitHub The digital landscape is a constant battleground, with threat actors continuously refining [...]