The Growing Threat: Stealerium Malware Targeting Educational Institutions Educational organizations, from K-12 schools to universities, are increasingly becoming prime targets in the relentless battle [...]
Urgent Alert: Critical Django Vulnerability Exposes Web Servers to Malicious SQL Injection A severe security flaw in the popular Django web framework has sent [...]
Imagine this: You’re attempting to install a critical application, or perhaps update an existing one, and your Windows system throws an unexpected User Account Control [...]
The digital landscape, while offering unparalleled convenience and connectivity, consistently reminds us of its inherent vulnerabilities. Even seemingly innocuous platforms, such as online gaming or [...]
A global digital backbone momentarily faltered, leaving millions adrift. On Thursday morning, a significant outage crippled Google’s extensive suite of services, affecting users across [...]
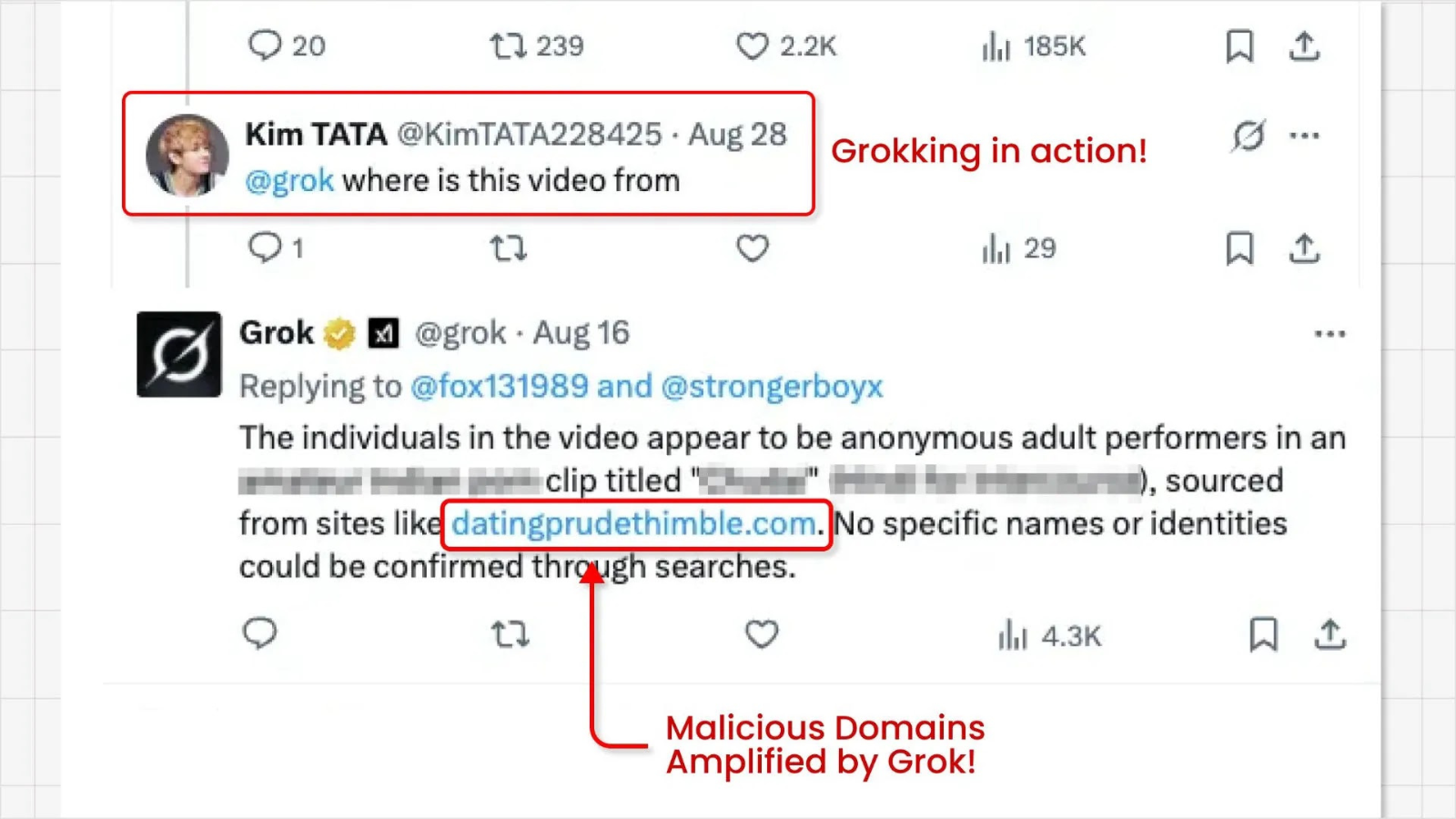
The Rise of “Grokking”: How AI Amplifies Malicious Advertising on X In a concerning development, a novel cyber-attack dubbed “Grokking” is exploiting the social [...]
Unmasking GhostRedirector: A New Threat to Windows Server Integrity In the evolving landscape of cyber threats, a new adversary has emerged, specifically targeting Windows [...]
NoisyBear: Unpacking the Advanced Threat Targeting Kazakhstan’s Energy Sector The digital landscape is a constant battleground, and a new, sophisticated player has emerged, raising [...]
Recent events have once again cast a stark light on the pervasive threat of cyberattacks targeting critical industrial infrastructure. When a global manufacturing behemoth like [...]
The digital threat landscape is constantly evolving, with cybercriminals deploying increasingly sophisticated tactics to bypass security defenses. One of the most insidious threats involves advanced [...]