The persistent hum of technological evolution often brings with it shifts that redefine how we interact with our devices. One such significant transformation is [...]
In the intricate landscape of modern software development, the acceleration provided by Continuous Integration/Continuous Delivery (CI/CD) pipelines is undeniable. Yet, this very efficiency often introduces [...]
AccuKnox Secures Patent for Groundbreaking Kernel-Level Runtime Security The digital landscape is a battleground, and the kernel, the very core of an operating system, [...]
The digital landscape is fraught with hidden dangers, even from sources that appear legitimate. A recent discovery has sent ripples through the cybersecurity community: a [...]
The year 2025 has ushered in a stark reminder of cybersecurity’s dynamic threat landscape. A sophisticated ransomware operation, leveraging compromised credentials from a third-party [...]
The Silent Infiltration: How DPRK IT Workers Leverage Code-Sharing Platforms for Remote Operations In an increasingly interconnected digital landscape, the lines between legitimate development [...]
Urgent Alert: Multiple Hikvision Vulnerabilities Expose Organizations to Remote Code Execution The digital landscape consistently presents new challenges for cybersecurity professionals. A recent disclosure [...]
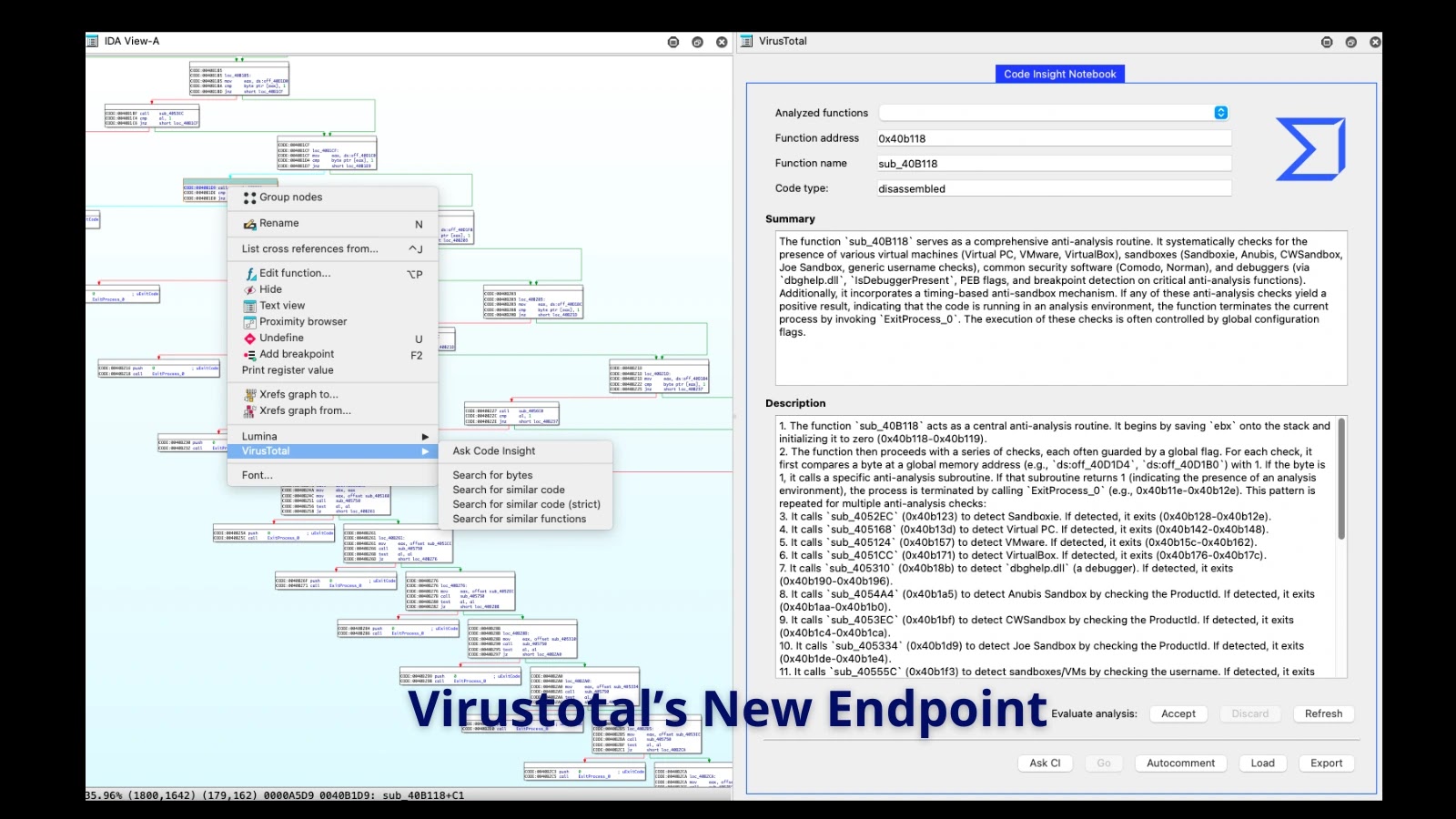
Malware analysis is a painstaking process, often likened to deciphering a complex, deliberately obscured puzzle. For cybersecurity professionals, the ability to quickly understand the [...]
In a significant development for organizations utilizing Salesloft Drift, Google has issued a crucial security advisory confirming a far more extensive breach than initially [...]
The Critical Imperative: Why Identity & Access Management is Non-Negotiable in 2025 In today’s hyper-connected operational landscape, digital interactions permeate nearly every facet of [...]