Urgent Alert: Multiple Hikvision Vulnerabilities Expose Organizations to Remote Code Execution The digital landscape consistently presents new challenges for cybersecurity professionals. A recent disclosure [...]
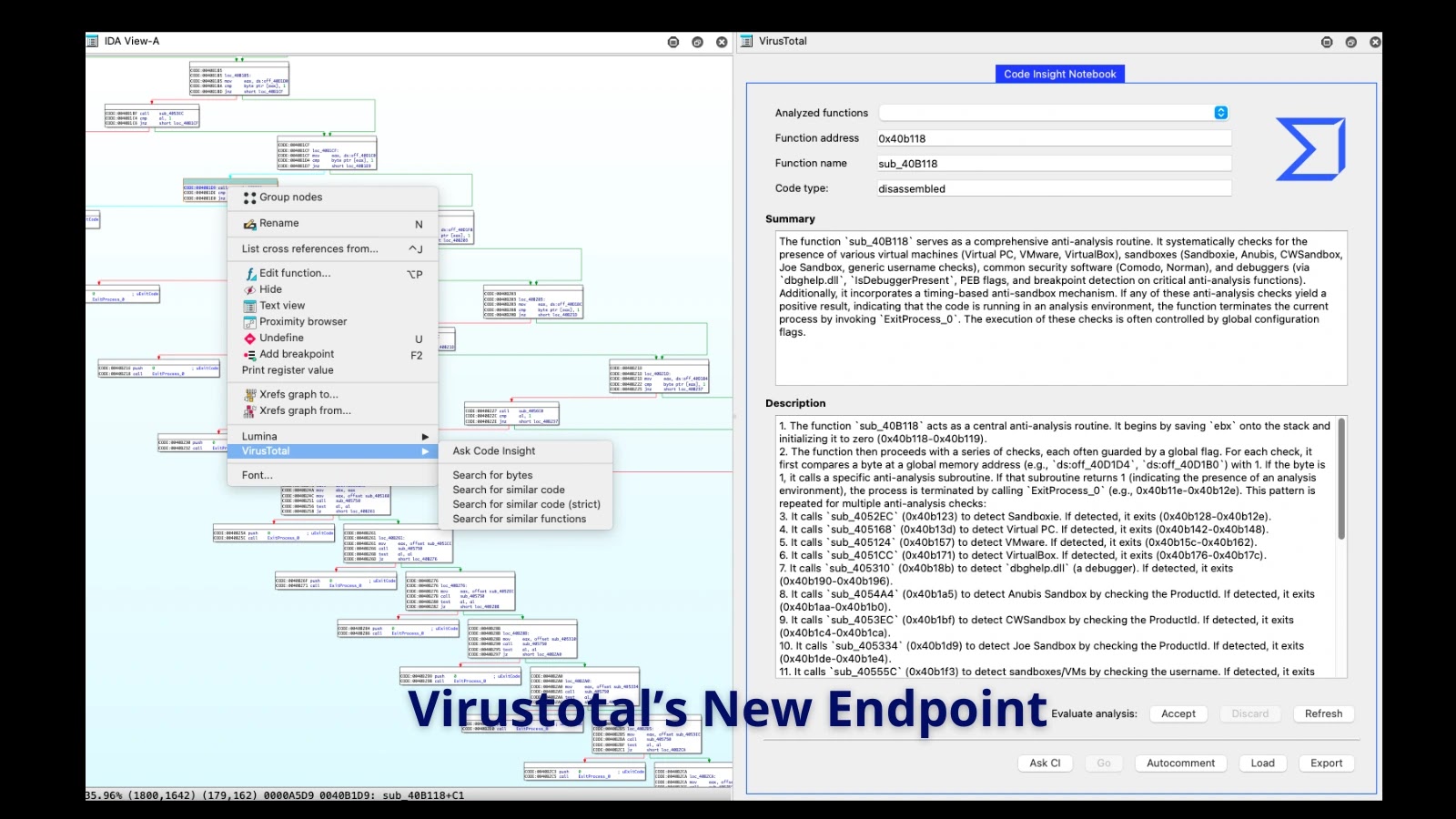
Malware analysis is a painstaking process, often likened to deciphering a complex, deliberately obscured puzzle. For cybersecurity professionals, the ability to quickly understand the [...]
In a significant development for organizations utilizing Salesloft Drift, Google has issued a crucial security advisory confirming a far more extensive breach than initially [...]
The Critical Imperative: Why Identity & Access Management is Non-Negotiable in 2025 In today’s hyper-connected operational landscape, digital interactions permeate nearly every facet of [...]
The Deceptive Lure: Threat Actors Weaponizing Facebook Ads with Fake TradingView Premium Apps In an increasingly interconnected digital landscape, even seemingly innocuous online advertisements [...]
The promise of Large Language Models (LLMs) revolutionizing code generation is undeniable. Developers are increasingly leveraging AI assistants to accelerate workflows, a practice often dubbed [...]
Understanding Adversary-in-the-Middle (AiTM) Attacks Multi-factor authentication (MFA) has long been considered a robust defense against credential theft, and Endpoint Detection and Response (EDR) systems [...]
JSCoreRunner: Unpacking the Mac Malware Campaign Delivering Payloads via PDF Conversion A new, highly sophisticated macOS malware campaign, dubbed JSCoreRunner, has emerged, leveraging a [...]
Unmasking the PhpSpreadsheet Vulnerability: A Critical SSRF Threat The digital landscape is constantly challenged by evolving security threats. A recent high-severity Server-Side Request Forgery [...]
TransUnion Hack Exposes 4M+ Customers: A Deep Dive into the Latest Data Breach The digital landscape is a minefield, and even the most trusted [...]