Unmasking TamperedChef: A Weaponized PDF Editor Steals Credentials In an increasingly complex threat landscape, adversaries continuously refine their tactics. A recent discovery by Truesec, [...]
Emulating Scattered Spider: Proactive Defense Against Sophisticated APTs The landscape of cyber threats is dynamic, with advanced persistent threats (APTs) continually refining their tactics. [...]
In the expansive and increasingly interconnected world of modern enterprise, the proper management and security of internal communication protocols are paramount. Organizations grapple with [...]
In the high-stakes world of cybersecurity, data is power, and the ability to process, analyze, and act upon it in real-time is paramount. Organizations grapple [...]
Over 1,400 developers recently faced a significant security breach as a malicious post-install script embedded within the popular NX build kit silently compromised their [...]
CISA Sounds the Alarm: Defending Against Sophisticated Chinese State-Sponsored Cyber Espionage The digital battleground is constantly shifting, and the latest intelligence from the U.S. [...]
Urgent Warning: Critical Kea DHCP Server Vulnerability Allows Remote DoS Through Single Packet Network infrastructure underpins nearly every modern organization, making the stability and [...]
Unmasking TAG-144: New Threats Targeting Government Entities The digital battleground is constantly shifting, and sophisticated threat actors relentlessly evolve their tactics. For cybersecurity professionals [...]
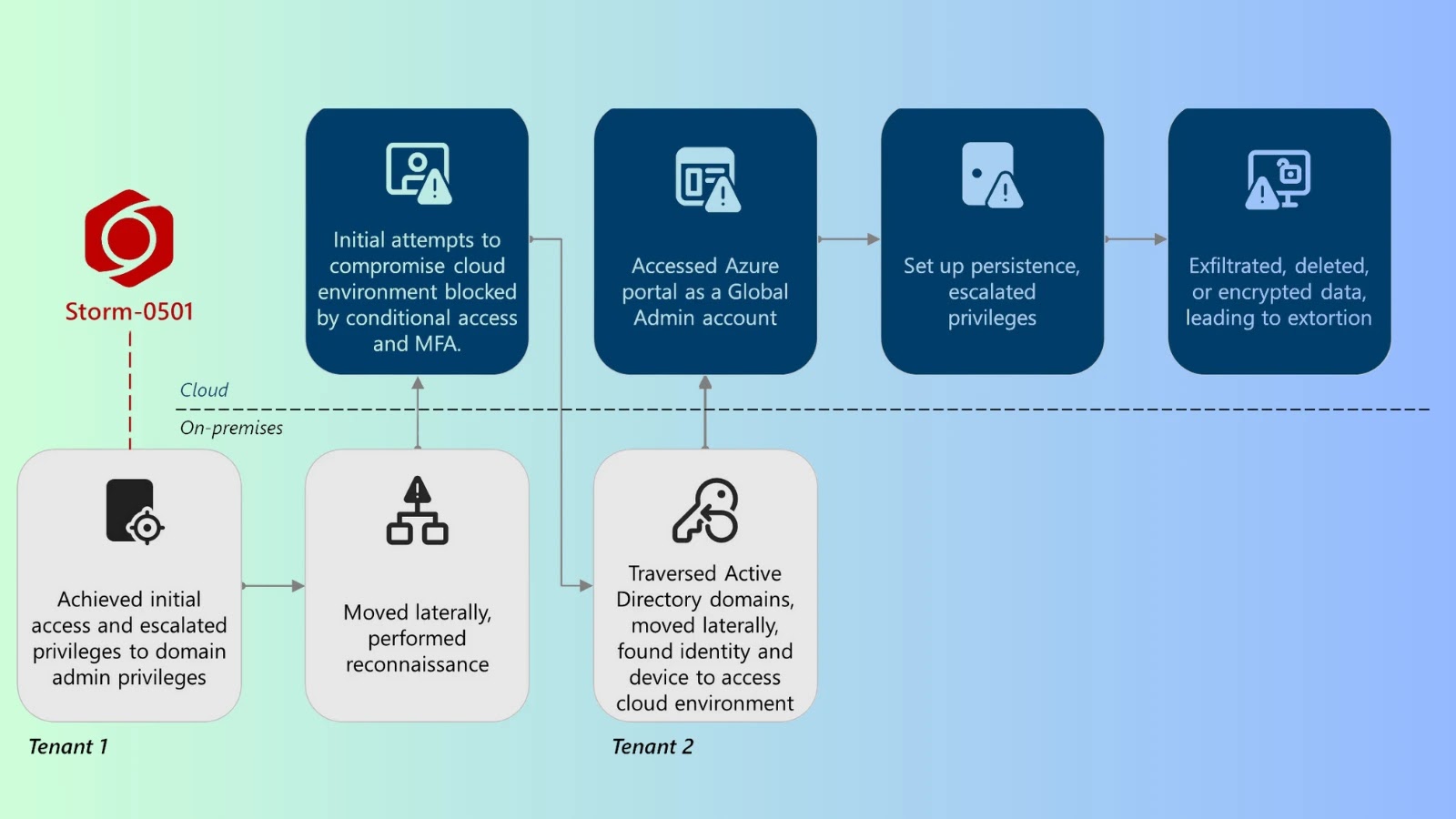
The Shifting Sands of Ransomware: Microsoft Exposes Storm-0501’s Cloud-Native Evolution The cybersecurity landscape is in constant flux, with threat actors continuously refining their methodologies [...]
The Betrayal of Trust: How a New Malware Exploits TASPEN’s Legacy to Prey on Indonesian Senior Citizens A disturbing new front has opened in [...]