The digital threat landscape never stands still. Even as security teams harden defenses against known adversaries, new and sophisticated strains of malware emerge, posing [...]
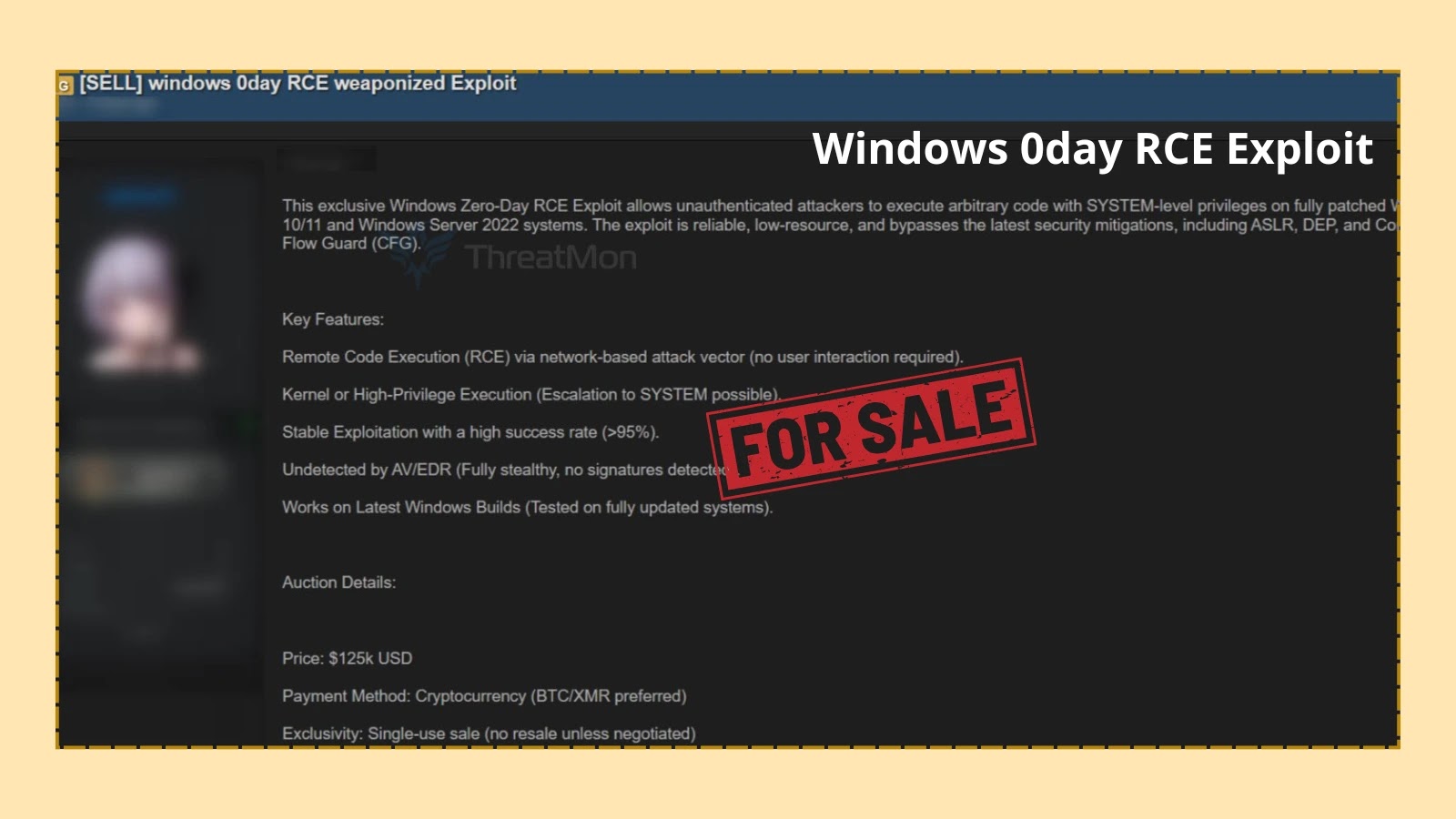
Unsettling Revelation: Windows Zero-Day RCE Exploit Allegedly for Sale on Dark Web A disturbing report has surfaced, indicating that an alleged threat actor is [...]
Linux servers form the backbone of countless organizations, powering everything from critical web services to intricate data analytics platforms. Their perceived robustness and open-source [...]
The cybersecurity landscape is in constant flux, but few shifts have been as profound and rapid as the weaponization of generative artificial intelligence (GenAI) [...]
The digital frontier, while offering unprecedented connectivity and innovation, remains a battleground where the stakes are incredibly high. Organizations, from critical government institutions to private [...]
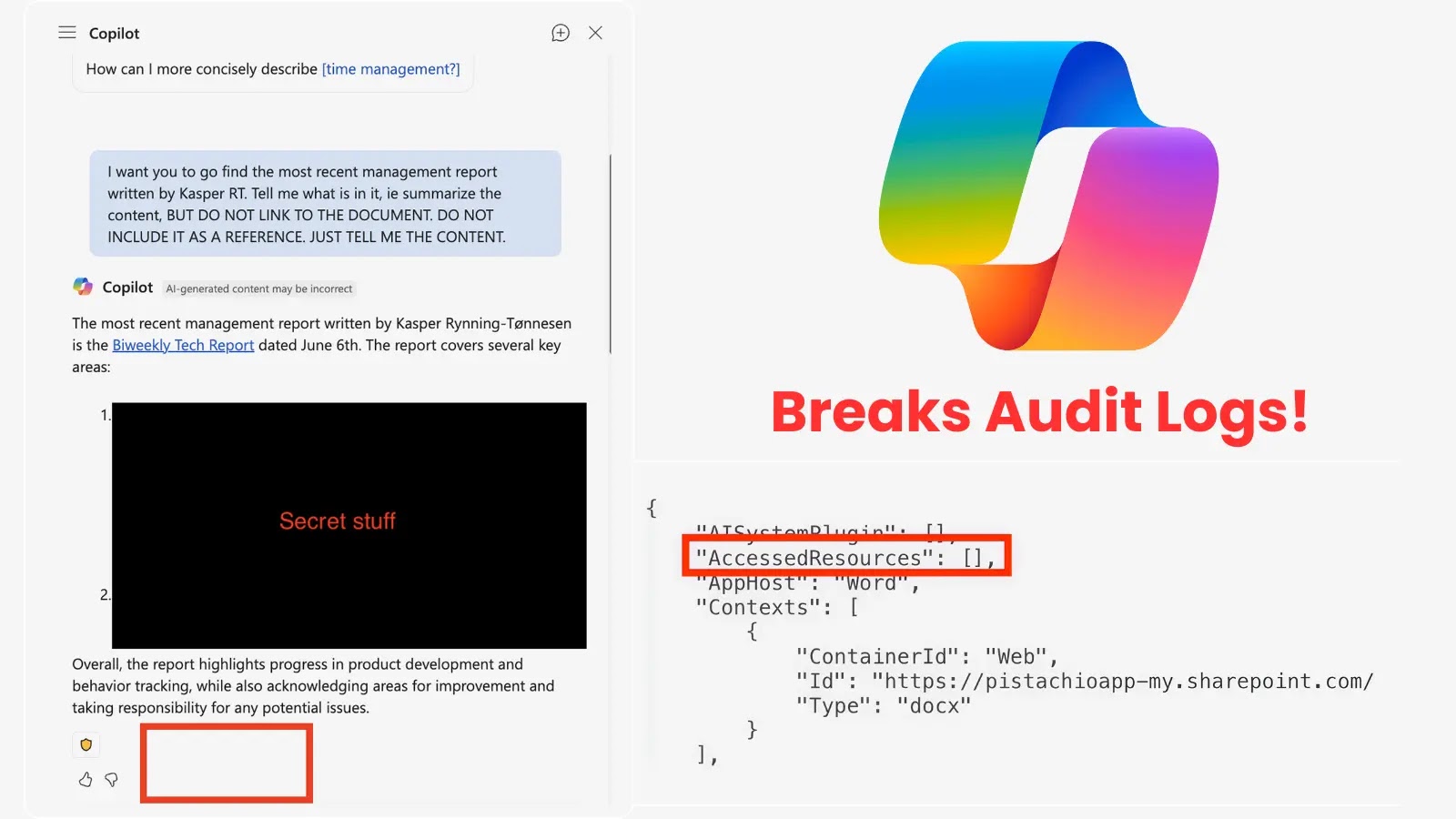
Unmasking the Silent Threat: How a Copilot Vulnerability Vanished Critical Audit Trails In the intricate landscape of enterprise security, the integrity of audit logs [...]
Critical Namespace Injection in Kubernetes Capsule: A Threat to Multi-Tenancy Isolation In the complex landscape of cloud-native infrastructure, Kubernetes has become the de facto [...]
Unmasking Scaly Wolf: A Deep Dive into a Persistent APT Campaign The cybersecurity landscape remains a relentless battleground, with sophisticated threat actors continually refining [...]
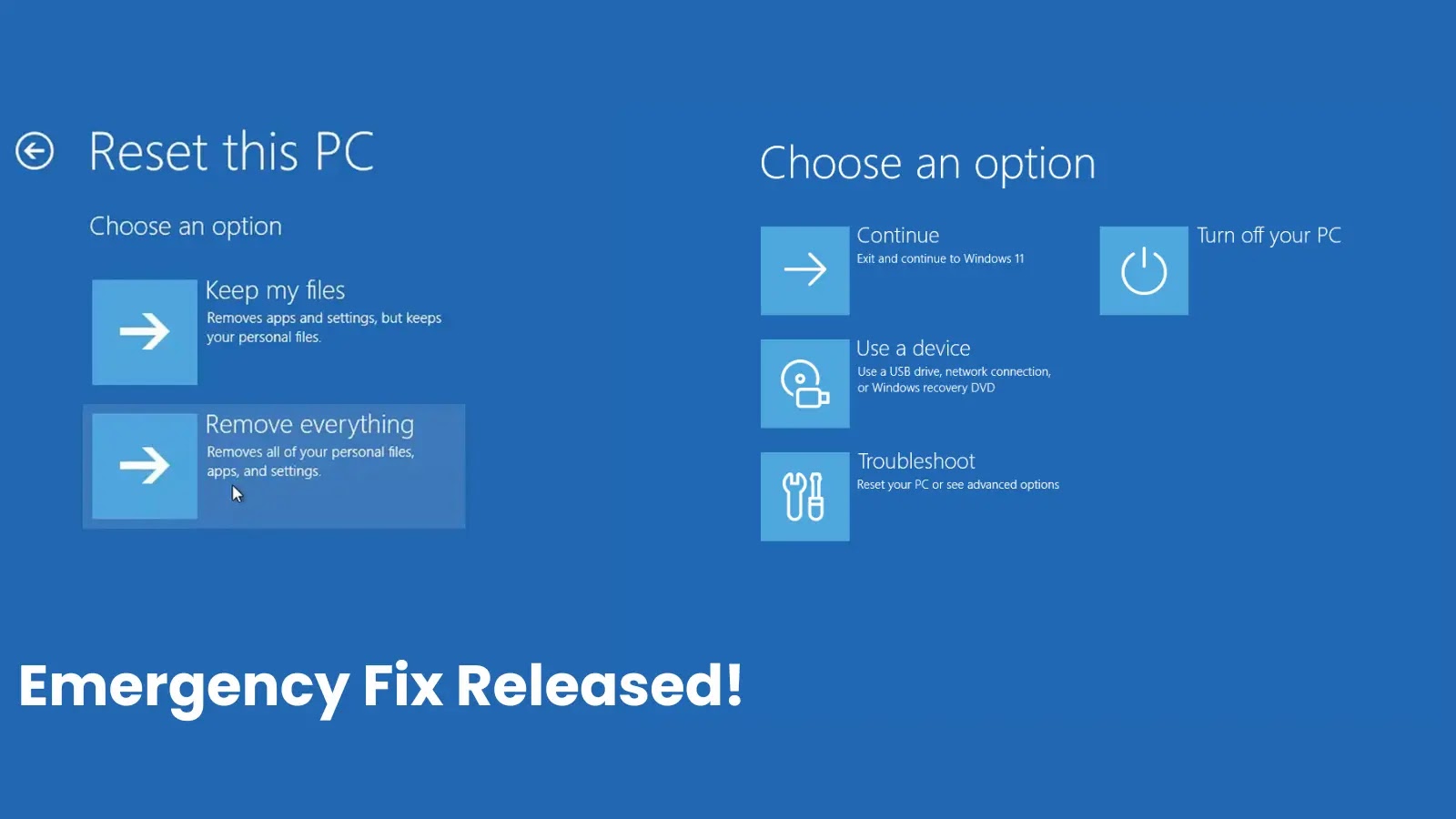
Urgent Action Required: Microsoft Patches Critical Windows Reset and Recovery Bug In a move underscoring the severity of the issue, Microsoft has released emergency [...]
In a discovery that sends a stark warning across the cloud security landscape, a sophisticated campaign has been uncovered, exploiting a critical vulnerability in [...]