The digital defense line for many enterprises is under renewed pressure. The Cybersecurity and Infrastructure Security Agency (CISA) has just issued a critical warning: a [...]
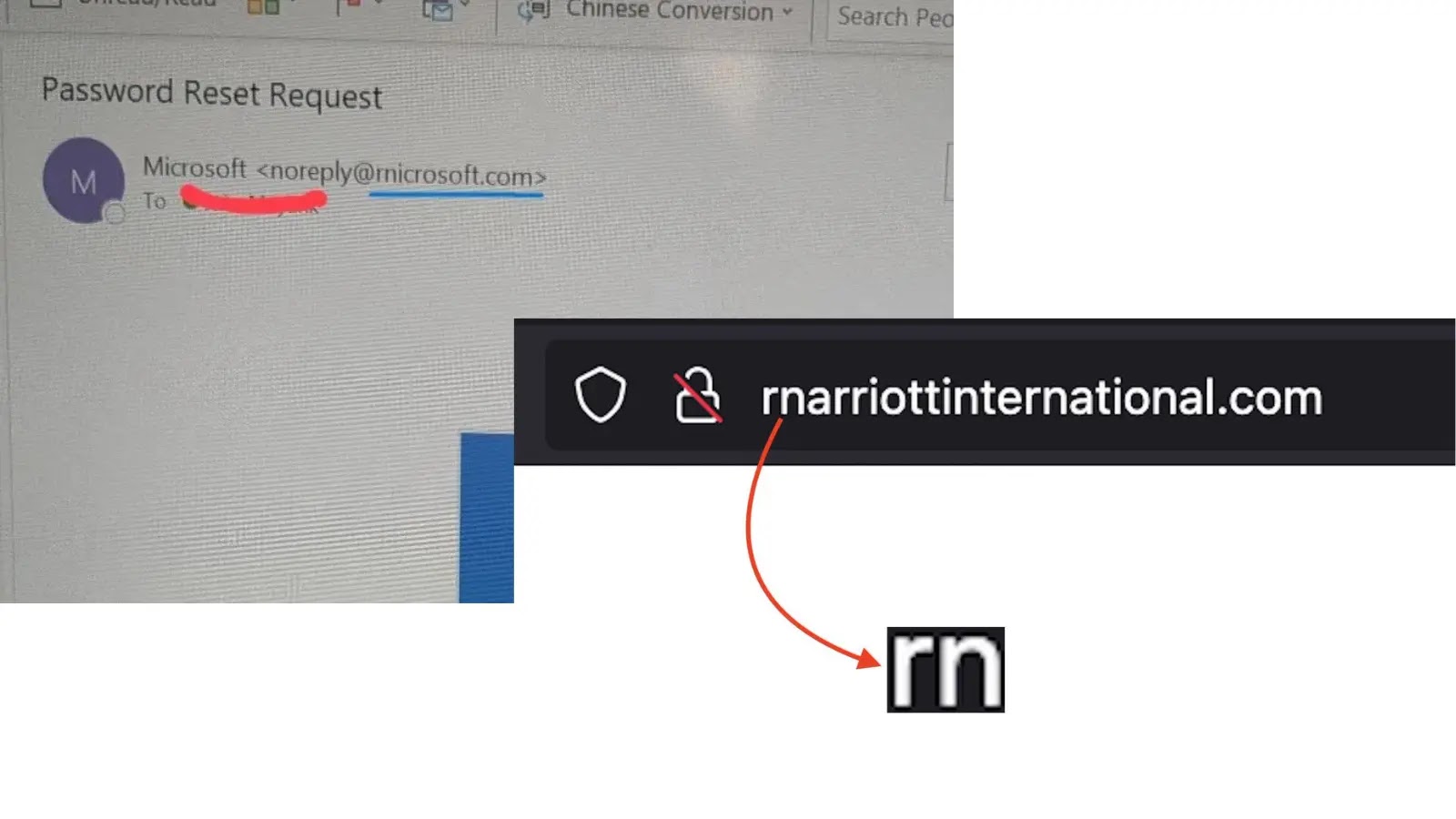
Deceptive ‘rn’ Typo Trick Impersonates Marriott in New Phishing Onslaught In the intricate landscape of cyber threats, attackers continuously evolve their tactics to compromise [...]
A routine security update for Windows 11, specifically version 25H2, has taken an alarming turn for many IT professionals and users. Microsoft has launched an [...]
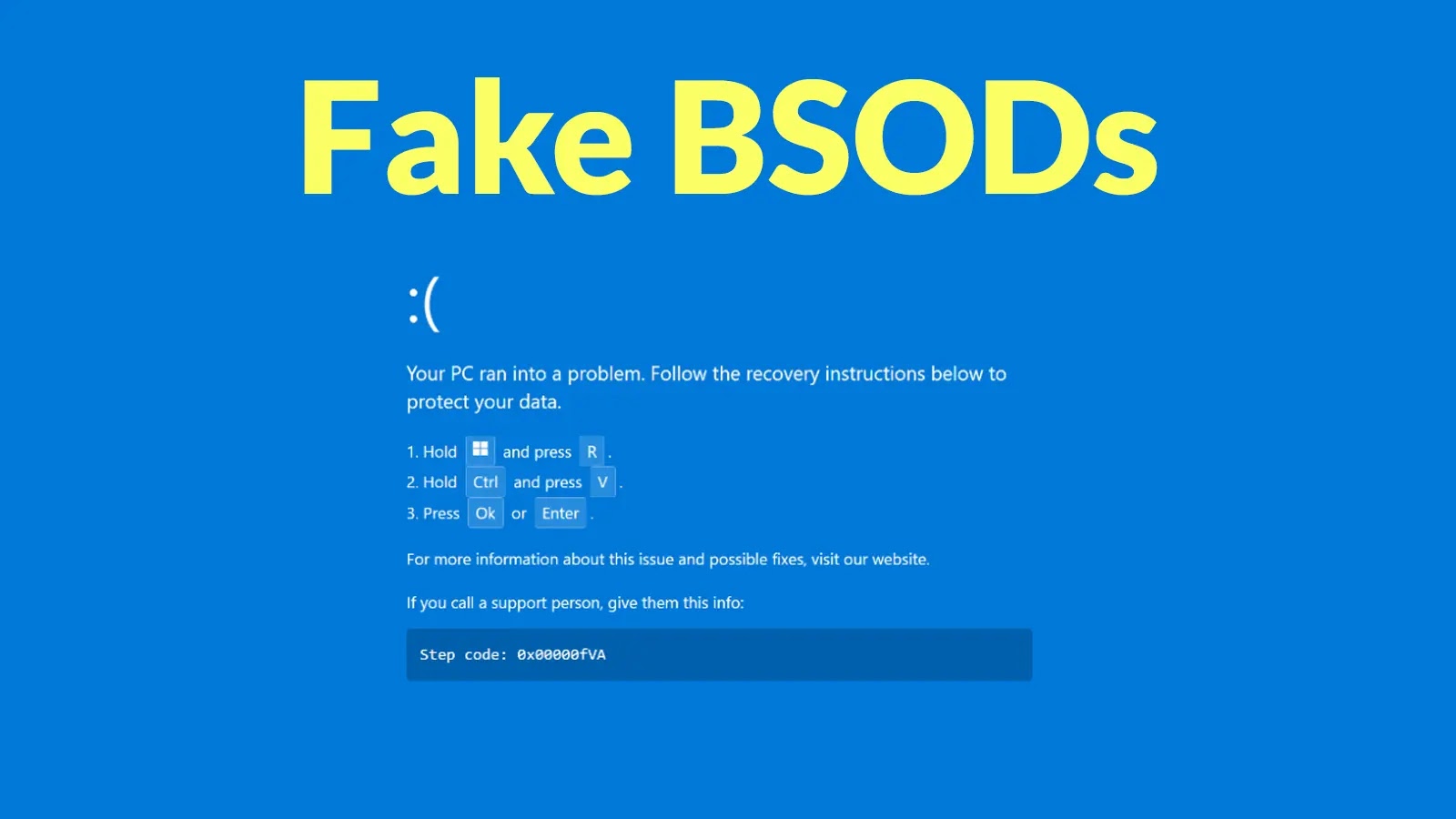
Deceptive Tactics: How Threat Actors Leverage Fake BSODs and Trusted Tools to Deploy DCRat The landscape of cyber threats continues its relentless evolution, with [...]
The construction industry, often perceived as a low-tech sector, is increasingly becoming a prime target for cybercriminals. As operations digitize, so do the attack [...]
Millions of Credentials Exposed: A Deep Dive into the Unprotected Database Breach A staggering 149 million login credentials, including a significant 48 million Gmail [...]
A disturbing revelation from recent security research highlights a significant privacy concern for Instagram users. A critical server-side vulnerability in Instagram’s infrastructure allowed unauthorized access [...]
The digital battlefield continues to expand, and nowhere is this more evident than in the persistent targeting of critical infrastructure. Late December 2025 brought [...]
In the evolving landscape of cyber threats, attackers continually refine their tactics, often leveraging trusted platforms to enhance the efficacy of their campaigns. A recent [...]
Windows 11 users, breathe a sigh of relief. Microsoft has swiftly rolled out a critical out-of-band (OOB) update, KB5078127, to address persistent and frustrating file [...]