In a significant development for web browser security, Google has awarded a staggering $250,000 bounty to a security researcher for uncovering a critical Remote [...]
A silent threat often emerges from the very tools designed to simplify complex IT operations. For organizations relying on Microsoft IIS and its accompanying ecosystem, [...]
The interconnectedness of modern critical infrastructure presents unprecedented challenges for cybersecurity. As operational technology (OT) systems become increasingly integrated with IT networks, the attack [...]
The digital frontier is in a perpetual state of flux, and the week of August 11-17, 2025, vividly underscored this reality. Critical security updates [...]
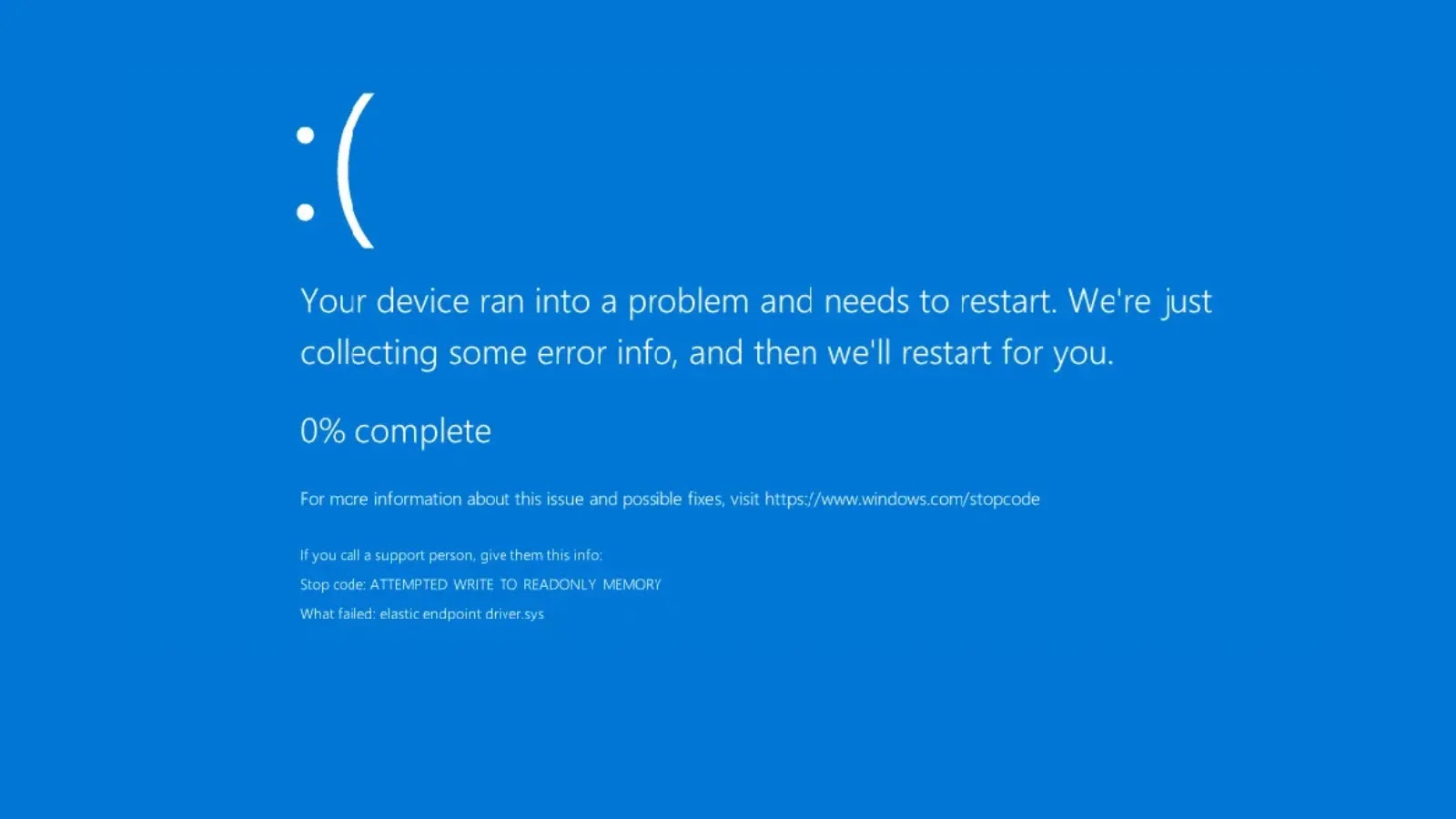
A disturbing new zero-day vulnerability in Elastic EDR’s core components has surfaced, posing a significant threat to organizational security postures. This critical flaw allows attackers [...]
Scattered Spider Re-Emerges: A New Telegram Channel Exposes Victims The cybersecurity landscape is constantly shifting, with threat actors evolving their tactics and expanding their [...]
The ubiquity of smart systems in public transportation brings unprecedented convenience and efficiency. However, this advancement also introduces significant cybersecurity challenges. A recently exposed [...]
A new and deceptive social engineering campaign, dubbed “ClickFix,” has emerged, specifically targeting Windows machines and enabling attackers to execute malicious PowerShell commands. This [...]
The digital frontier of enterprise IT constantly faces sophisticated threats. The latest alarm bell rings loud for organizations utilizing VMware ESXi environments, as a newly [...]
Urgent Warning: Critical Citrix NetScaler Zero-Day (CVE-2025-6543) Under Active Exploitation Organizations worldwide are urged to take immediate action as the Dutch National Cyber Security [...]