The digital landscape is under constant siege, with threat actors continually innovating new methods to bypass defenses. A concerning new trend has emerged: cybercriminals [...]
The long arm of justice often moves slowly, but for sophisticated cybercriminals, it invariably catches up. A recent extradition from France to the United States [...]
In an era where every new cybersecurity headline seems to scream “zero-day,” a recent statement from SonicWall has brought a crucial perspective to light. [...]
Microsoft 365 Direct Send: A New Frontier for Credential Theft Attacks The digital landscape is a constant battleground, and threat actors continuously refine their tactics [...]
ScarCruft’s Evolving Threat: Rust-Based Malware and Ransomware Deployment The cybersecurity landscape is in constant flux, with state-sponsored Advanced Persistent Threat (APT) groups continually refining [...]
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning concerning a sophisticated new exploit chain, dubbed “ToolShell,” actively targeting on-premises [...]
Ghost Calls: The Covert Web Conferencing Attack You Need To Know About The landscape of cyber threats is in constant flux, with attackers consistently innovating [...]
The digital battlefield against cybercrime continues to intensify, often in unseen skirmishes that protect millions of users. A recent announcement from Meta, WhatsApp’s parent [...]
The year is 2025. The cloud landscape, once a frontier of innovation, has fully matured into the battleground for enterprise security. Attacks aren’t just sophisticated; [...]
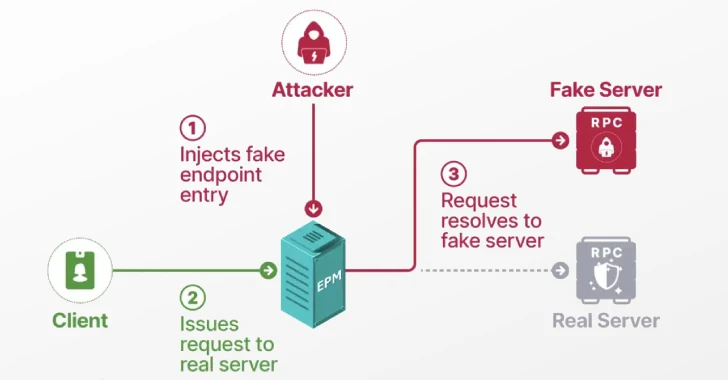
Unmasking the Impersonator: Windows EPM Poisoning and Domain Privilege Escalation In the intricate landscape of enterprise cybersecurity, a single, seemingly minor vulnerability can form [...]