—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Drupal Modules Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Drupal Config [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Cross-site Scripting Vulnerability in COOKiES Consent Management module of Drupal Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: [...]
[CIVN-2025-0168] Elevation of Privilege Vulnerability in Microsoft Exchange Server Hybrid Deployment
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Elevation of Privilege Vulnerability in Microsoft Exchange Server Hybrid Deployment Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: [...]
Urgent Cybersecurity Alert: Critical Vulnerabilities Discovered in Rockwell Arena Simulation Software Organizations worldwide relying on Rockwell Automation’s Arena Simulation software face a significant and [...]
Messaging platforms are a primary vecteur for sophisticated scams. Understanding how to discern legitimate communication from malicious attempts is crucial for securing digital interactions. [...]
The digital landscape is a constant battleground, and the emergence of sophisticated threats demands immediate attention. One such threat, the highly advanced DevilsTongue Windows [...]
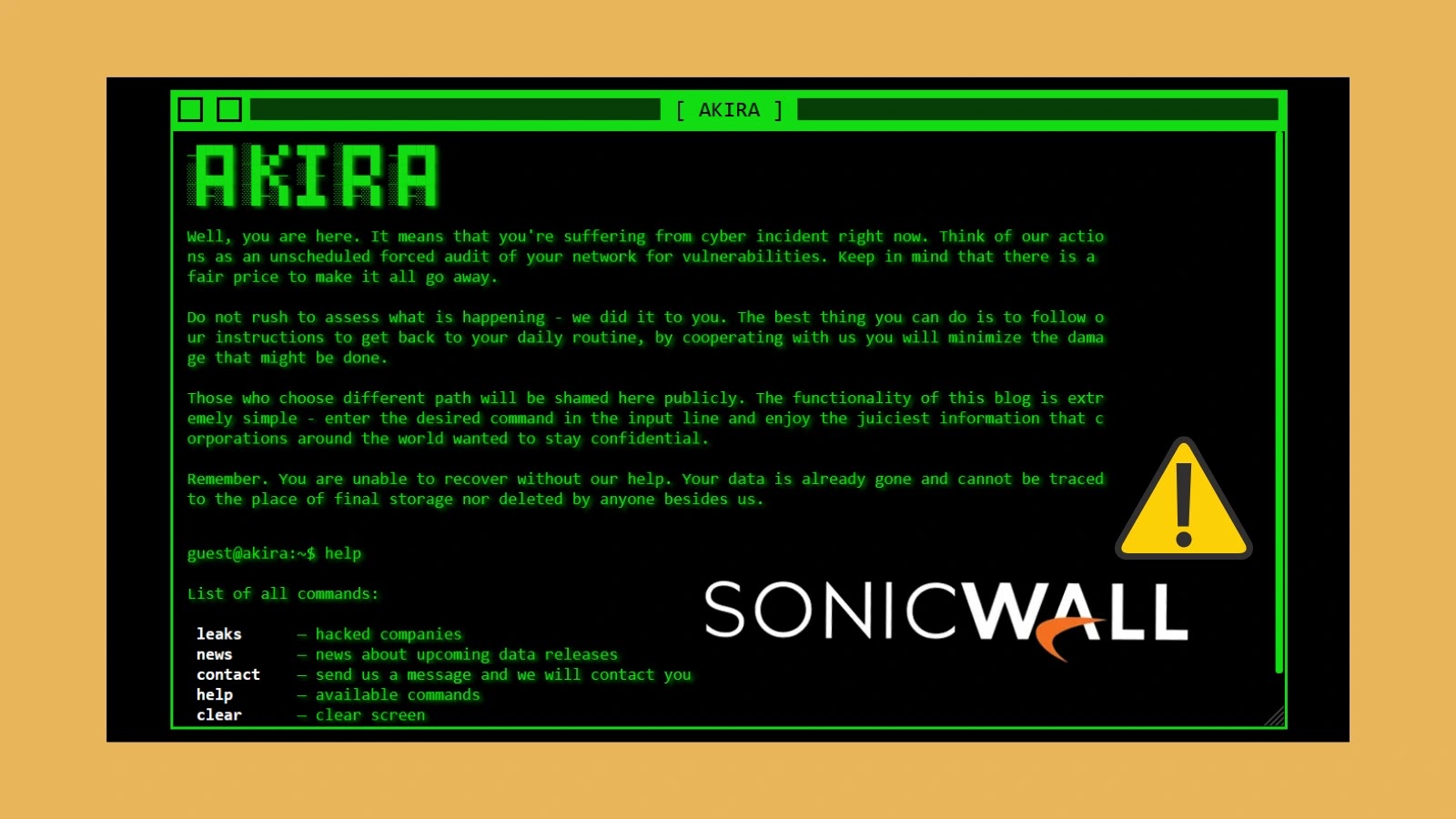
Akira Ransomware’s Evolving Tactics: Exploiting Windows Drivers for AV/EDR Evasion The cybersecurity landscape continually presents new challenges, and the recent discovery of Akira ransomware [...]
CAPTCHAgeddon: Unmasking the ClickFix Malware Campaign The digital landscape is in perpetual flux, with threat actors consistently refining their tactics. A disturbing new trend [...]
The cybersecurity landscape intensifies daily. As threat actors refine their tactics and regulatory demands burgeon, businesses, particularly Small and Medium-sized Businesses (SMBs), find themselves [...]
Trend Micro Apex One Under Siege: Critical Flaws Actively Exploited in On-Premise Deployments The cybersecurity landscape faces a persistent threat from sophisticated actors who [...]