The Deceptive Inside Job: How Hackers Weaponize Microsoft 365’s Direct Send for Phishing In the evolving landscape of cyber threats, attackers constantly seek novel [...]
The cybersecurity landscape is in constant flux, a relentless battle where new threats emerge as quickly as old ones dissipate. The second quarter of 2025 [...]
The Silent Surge: PlayPraetor Malware Compromises 11,000 Android Devices A disturbing new front has opened in the ceaseless battle against mobile cybercrime. Over 11,000 [...]
The AI-Powered Offensive: How LLMs Accelerate Exploitation of Trapped COM Objects The cybersecurity landscape has reached a new inflection point. Adversaries are no longer [...]
Unmasking the Threat: How Fake Microsoft OAuth Apps Are Bypassing MFA Enterprise security teams face a persistent and evolving challenge: sophisticated phishing campaigns designed [...]
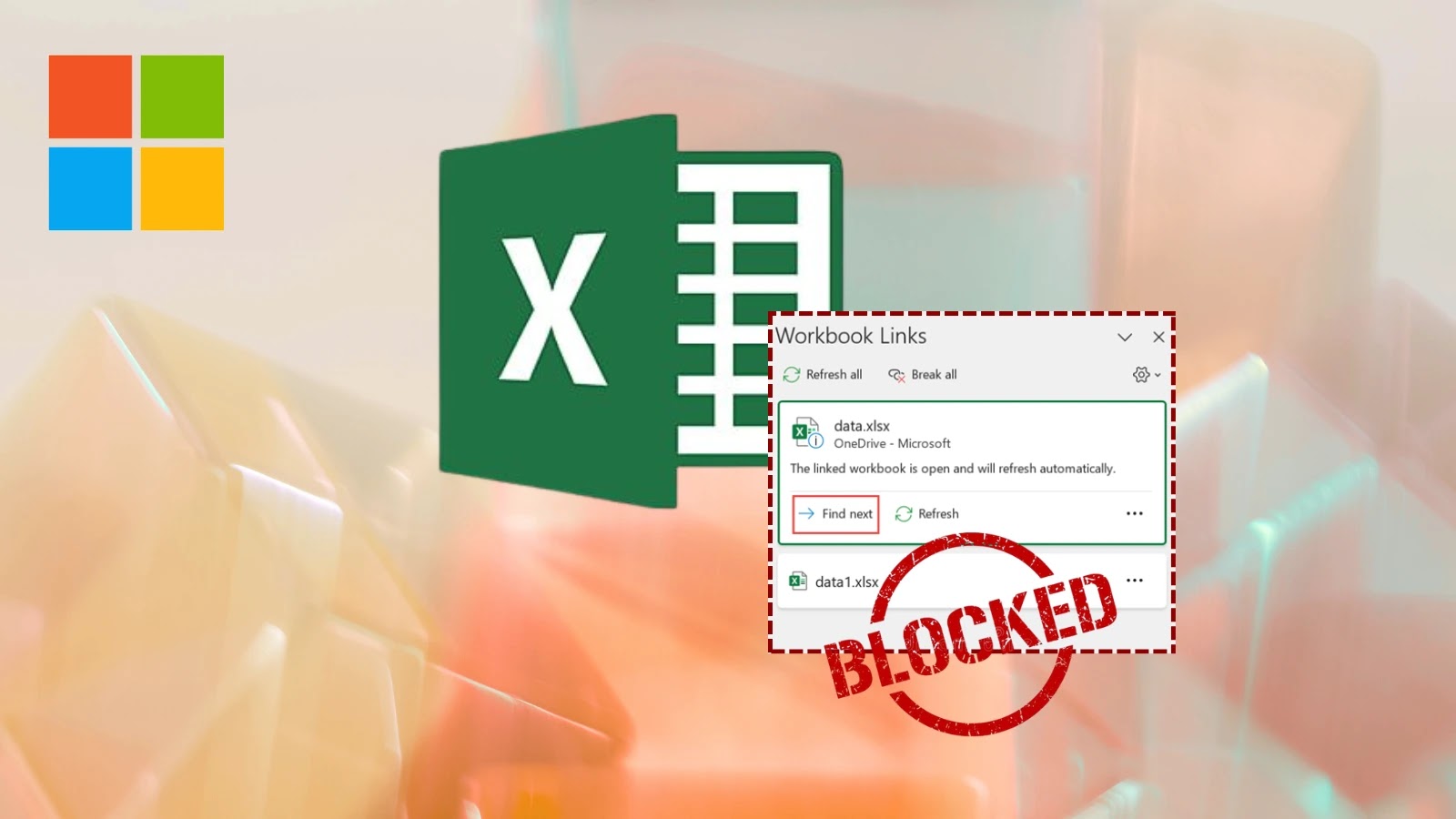
Microsoft Fortifies 365: Disabling External Workbook Links to Blocked File Types by Default The digital landscape is a constant battleground, with cybercriminals continually probing [...]
A disturbing new cyberespionage campaign has cast a harsh spotlight on the foundational elements of digital trust. Imagine a scenario where the very certificates designed [...]
The quiet hum of critical infrastructure often belies the constant, invisible struggle against cyber threats. Recent intelligence, however, shatters that illusion with a stark [...]
The cybersecurity landscape is constantly shifting, with threat actors continuously refining their tactics to breach defenses. A particularly insidious evolution is the widespread leveraging [...]
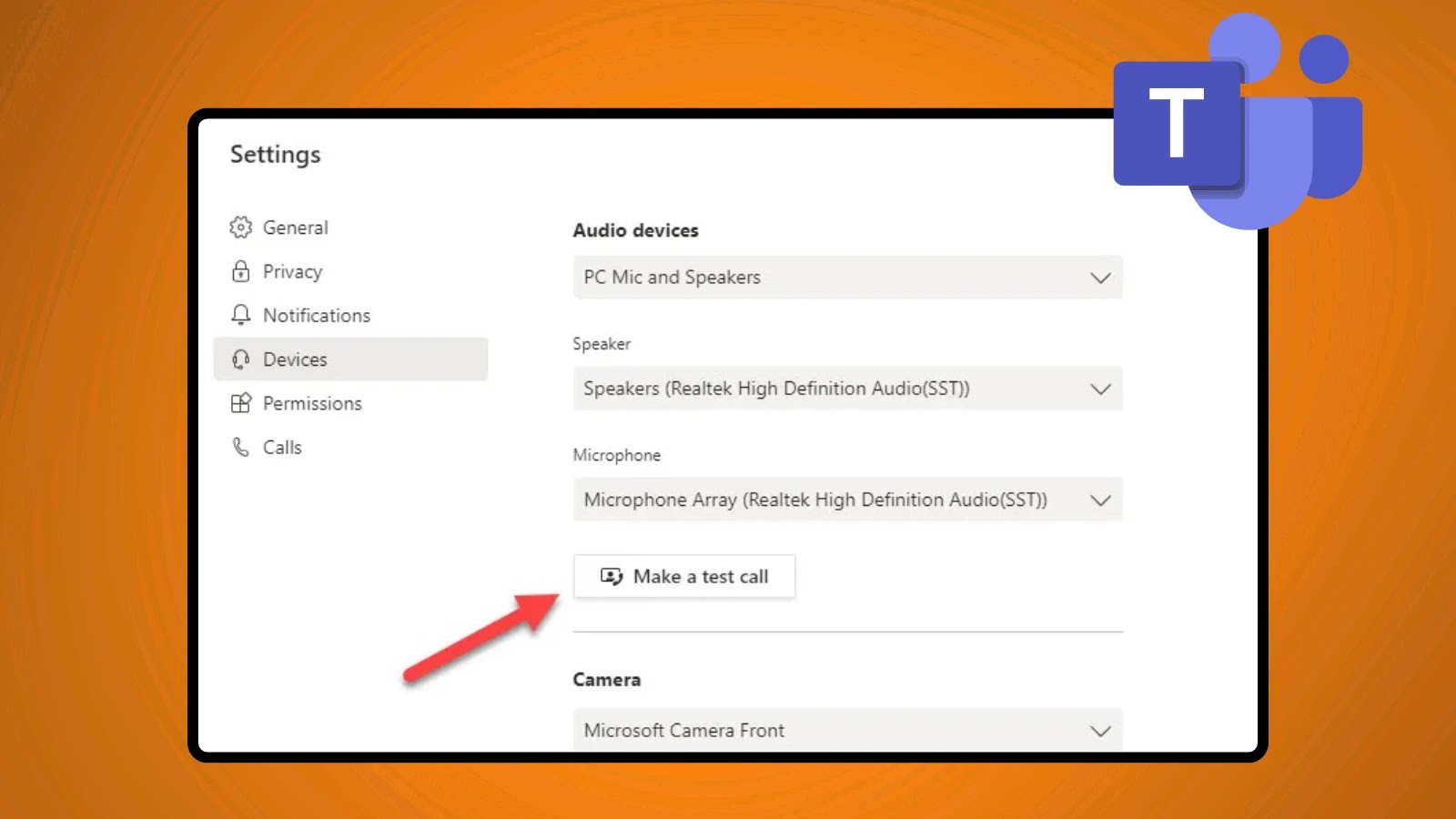
Microsoft Teams Enhances Network Quality Assurance with New 60-Second Silent Test Calls Ensuring seamless communication is paramount for any modern enterprise. Disruptions to vital [...]