Enterprises globally rely on powerful infrastructure automation tools to streamline operations and manage vital secrets. When a critical vulnerability surfaces within such a foundational [...]
Raspberry Robin’s Persistent Evolution: Exploiting Windows Vulnerabilities The cybersecurity landscape faces a persistent and evolving threat as Raspberry Robin, a sophisticated malware downloader also [...]
Streamlining SOC Operations: How Top CISOs Combat Alert Fatigue and Uncover Real Threats In the relentless pursuit of robust security, many organizations invest heavily [...]
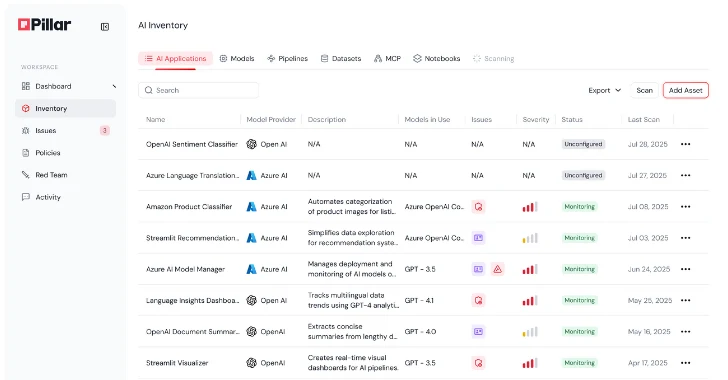
The rapid advancement of Artificial Intelligence (AI) has brought unprecedented capabilities to various industries. However, this evolution also introduces novel and complex security challenges. [...]
Hackers Can Manipulate BitLocker Registry Keys Via WMI to Execute Malicious Code as Interactive User
Unmasking BitLocker’s Hidden Lateral Movement Vulnerability: A Deep Dive for Security Professionals In the intricate landscape of cybersecurity, attackers consistently evolve their tactics, leveraging [...]
The modern enterprise faces a silent, yet significant, threat: the untamed landscape of Shadow IT. Once relegated to niche corners, the proliferation of cloud-based services [...]
Unmasking the Largest Bitcoin Heist: A $3.5 Billion Revelation The cryptocurrency landscape, while promising innovation and financial freedom, remains a prime target for sophisticated [...]
In the relentless cat-and-mouse game of cybersecurity, anticipating the adversary’s next move is paramount. For too long, organizations have been reactive, scrambling to patch [...]
The cybersecurity landscape is in constant flux, with new threats emerging and existing ones evolving at an alarming pace. This weekly recap delves into [...]
The Silent Intruder: Navigating and Preventing Man-in-the-Middle Attacks In the intricate landscape of cyber threats, some of the most devastating attacks don’t rely on brute-force [...]