The cybersecurity landscape is a perpetual arms race, and threat actors, particularly sophisticated ransomware groups like LockBit, are consistently refining their tactics to breach [...]
The Unyielding Email Frontline: Securing Your Enterprise in 2025 The digital perimeter of every organization faces an increasingly sophisticated onslaught. In 2025, attackers wield advanced [...]
Lazarus Subgroup ‘TraderTraitor’: Unpacking the Threat to Cloud Platforms and Supply Chains In an era where digital infrastructure is increasingly cloud-centric and supply chains [...]
The security of our physical spaces increasingly relies on the robustness of the digital infrastructure underpinning them. When vulnerabilities surface in widely deployed surveillance [...]
Unveiling the Critical Role of Website Monitoring Tools in 2025 In the relentless pursuit of seamless digital experiences, website performance is paramount. Downtime, sluggish [...]
Urgent Warning: Critical WordPress Theme RCE Vulnerability Under Active Attack In a significant cybersecurity development, a severe Remote Code Execution (RCE) vulnerability within the [...]
Unmasking Silk Typhoon: Chinese Firms’ Patent Hoard Reveals State-Sponsored Cyber Espionage Tools The digital shadows cast by state-sponsored hacking groups often obscure their origins [...]
Unpacking the Latest Apple Security Patches: A Critical Safari Vulnerability and Zero-Day Exploitation A recent wave of security updates from Apple has once again [...]
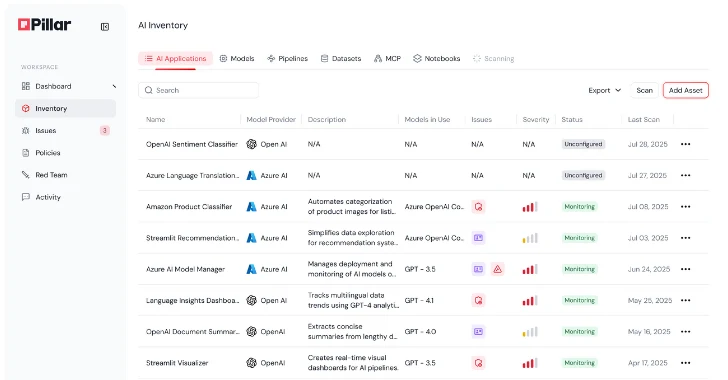
Unveiling Pillar Security’s AI Platform: A Comprehensive Walkthrough for Secure AI Systems The rapid integration of Artificial Intelligence (AI) across industries presents unprecedented opportunities, [...]
The digital landscape is a constant battleground, relentlessly challenged by sophisticated cyber threats. Among the most concerning adversaries to emerge, Lumma Password Stealer has [...]