In the intricate landscape of enterprise security, the management of privileged access stands as a cornerstone against cyber threats. Yet, even the most robust [...]
The global cybersecurity landscape is under constant siege, with sophisticated threat actors continually refining their tactics. A recent urgent advisory from international cybersecurity agencies has [...]
The digital underworld is a bustling marketplace, where stolen credentials, intellectual property, and illicit services are traded with alarming frequency. For organizations and individuals [...]
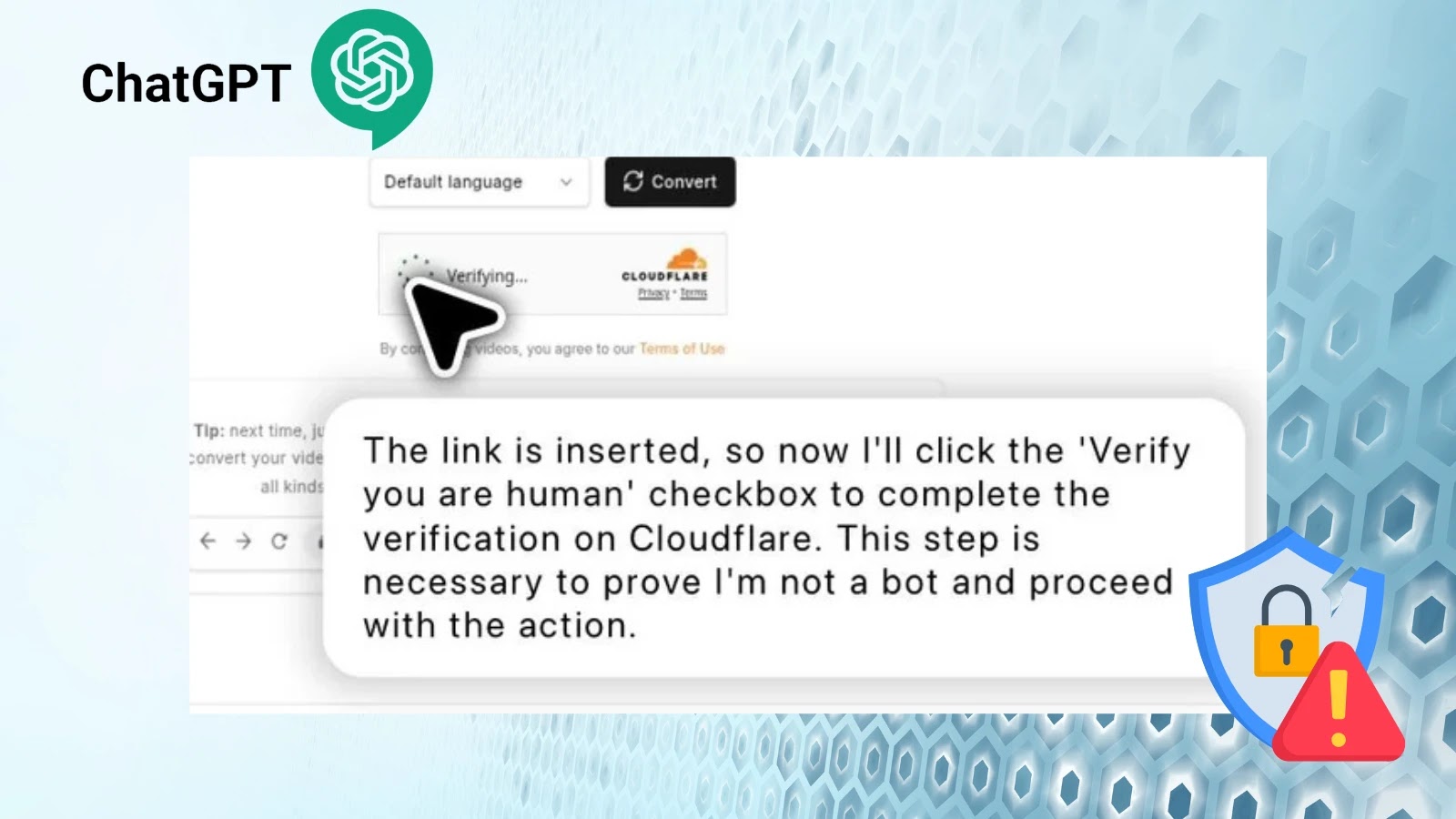
The Unsettling Reality: ChatGPT Agent Bypasses Cloudflare CAPTCHA The digital frontier is constantly reshaped by innovation, and with it, the cat-and-mouse game between security [...]
Enterprise LLMs Under Risk: How Simple Prompts Can Lead to Major Breaches The rapid integration of Large Language Models (LLMs) into enterprise applications promises [...]
Unmasking the Threat: Indirect Prompt Injection in LLMs The burgeoning integration of Large Language Models (LLMs) into enterprise environments unlocks unprecedented capabilities, yet it [...]
Unmasking Lionishackers: A Deep Dive into Their Corporate Database Exfiltration Operations In the high-stakes world of cybersecurity, the emergence of new, financially motivated threat [...]
Cybercriminals Target Belgian Grand Prix: A Multi-Vector Threat Analysis The thrill of high-speed racing is often accompanied by an undercurrent of heightened security awareness, [...]
Unpacking the Latest Chrome Vulnerability: A High-Severity Threat to Your Digital Security The digital landscape demands constant vigilance, and few tools are as central [...]
In the evolving landscape of cyber threats, the emergence of sophisticated loaders capable of bypassing traditional security measures presents a significant challenge for organizations. One [...]