The Critical Role of Anti-Phishing Tools in 2025 Phishing attacks remain a persistent and evolving threat, consistently ranking among the most common and damaging [...]
The Silent Saboteur: When EDR Becomes a Weapon Against Itself The digital defense landscape is in a constant state of flux, with security solutions [...]
Unveiling the Criticality of Kubernetes Monitoring in 2025 In the complex landscape of modern cloud-native applications, Kubernetes has emerged as the definitive standard for [...]
In the intricate landscape of global cybersecurity, the evolving tactics of state-sponsored threat actors represent a persistent and significant challenge. North Korean cybercriminals, in [...]
Thousands of SharePoint Servers Exposed: A Critical Internet-Facing Threat The digital landscape is constantly shifting, and with it, the pervasive threat of cyberattacks intensifies. [...]
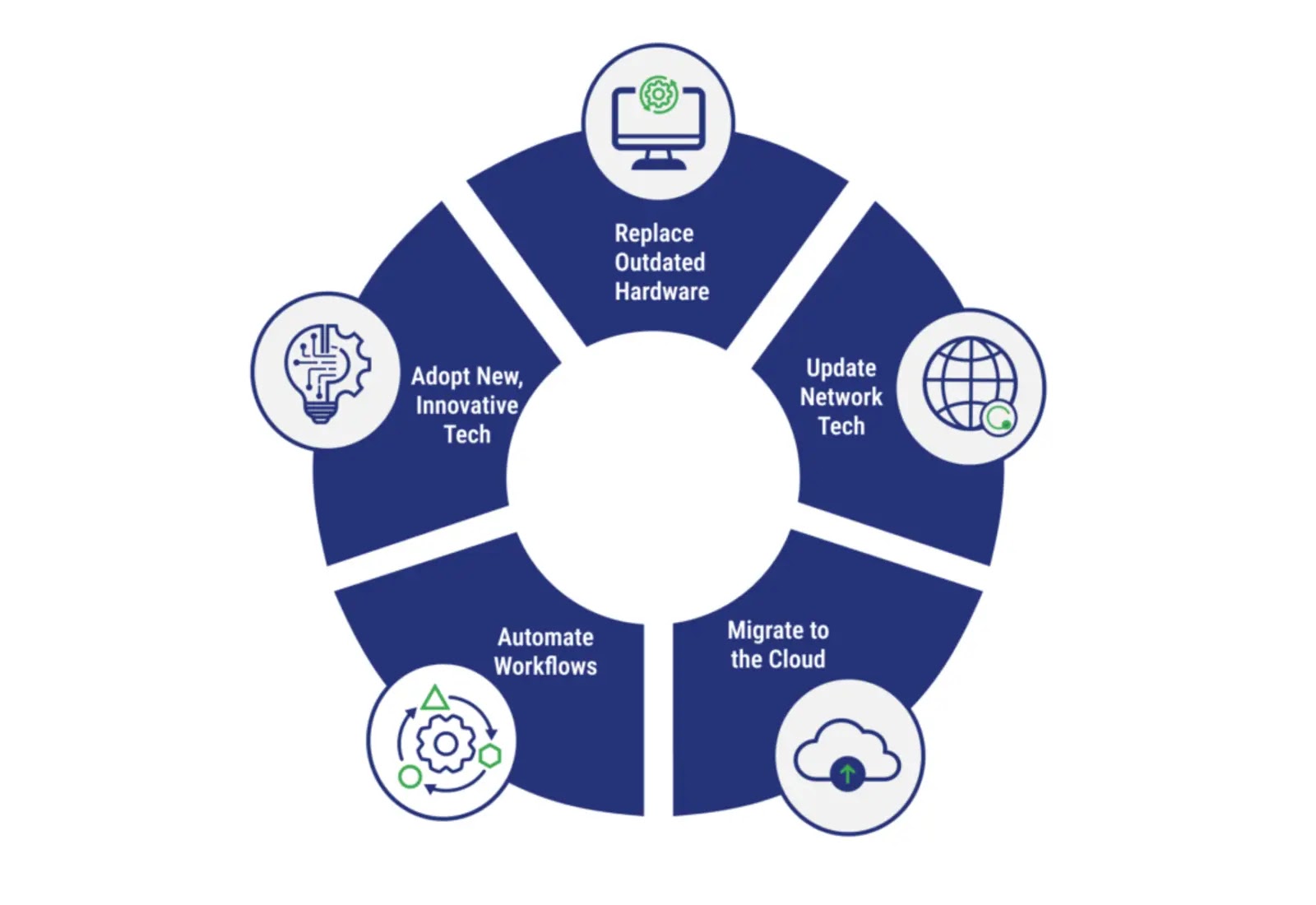
Navigating the Evolving IT Landscape: Why Modernization is Non-Negotiable in 2025 The pace of technological change shows no signs of slowing. For organizations in [...]
The digital landscape is a constant battleground, relentlessly challenging even the most sophisticated defense mechanisms. A stark reminder of this perpetual arms race comes from [...]
In the relentless battle against sophisticated cyber threats, speed and precision are paramount. Every second counts when dissecting malicious code and understanding its impact. [...]
The geopolitical landscape of cyber espionage continues to evolve, with nation-state actors pushing the boundaries of attack sophistication. Recent reports detail a chilling new [...]
North Korean APT Hackers Poison CI/CD Pipelines: A New Frontier in Cyber Espionage The digital landscape is a constant battleground, and state-sponsored threat actors continually [...]