A significant security concern has emerged for users of NVIDIA NSIGHT Graphics on Linux platforms. A recently disclosed vulnerability, tracked as CVE-2025-33206, poses a [...]
Oracle, a critical pillar of enterprise IT infrastructure globally, has once again underscored its commitment to security with the release of its January 2026 [...]
Unmasking CVE-2026-22844: A Critical Zoom Command Injection Vulnerability The ubiquity of video conferencing solutions like Zoom has fundamentally reshaped how we work and communicate. [...]
A disturbing new trend has emerged in the cybersecurity landscape, pointing to an advanced attack vector that leverages seemingly innocuous image files to deliver [...]
Unmasking PixelCode: A New Era of Malware Concealment The digital landscape is a battleground where adversaries constantly innovate, pushing the boundaries of stealth and [...]
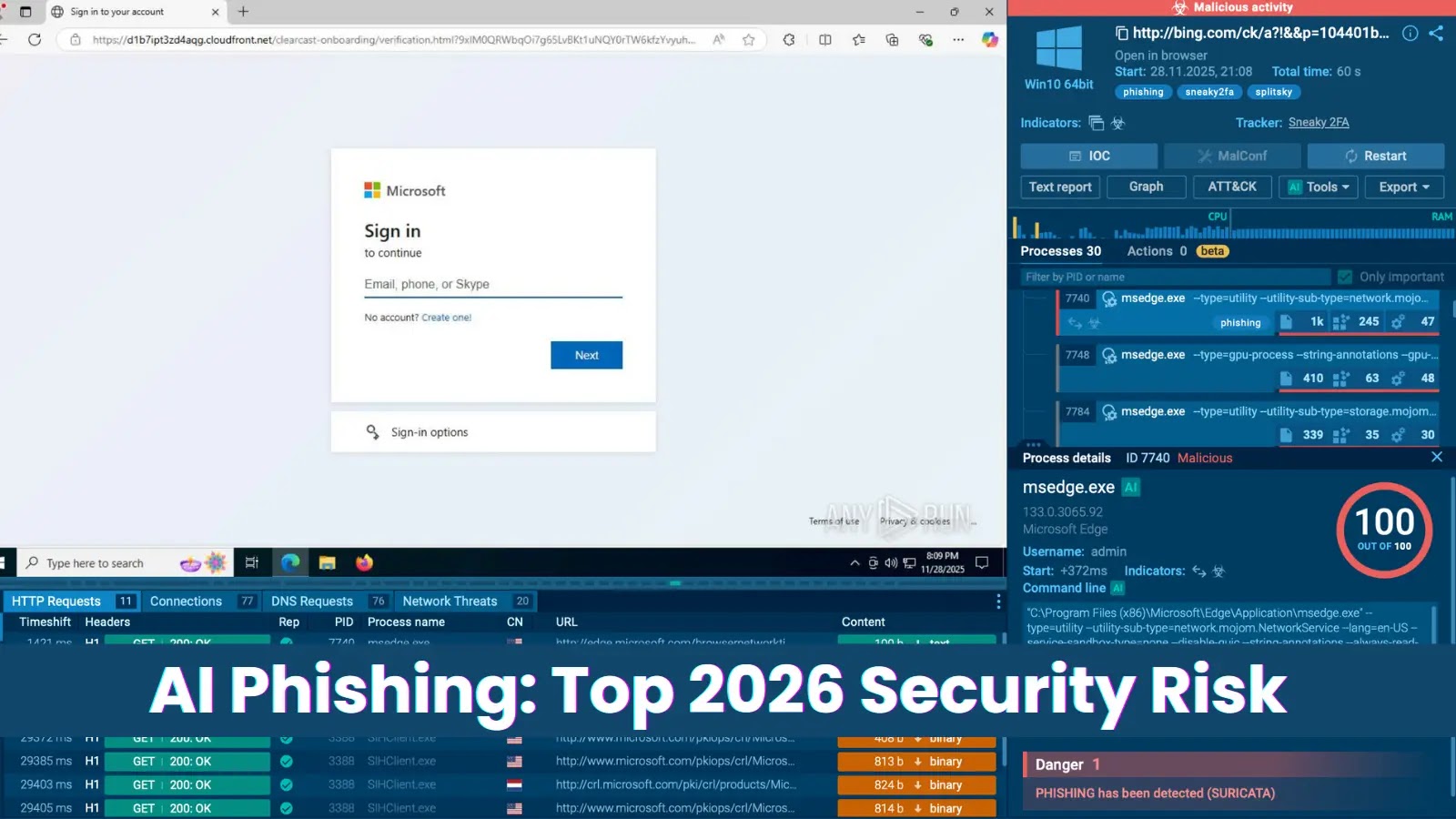
The days of easily identifiable phishing emails are over. Gone are the glaring grammatical errors, the obviously suspicious links, and the poorly disguised attempts [...]
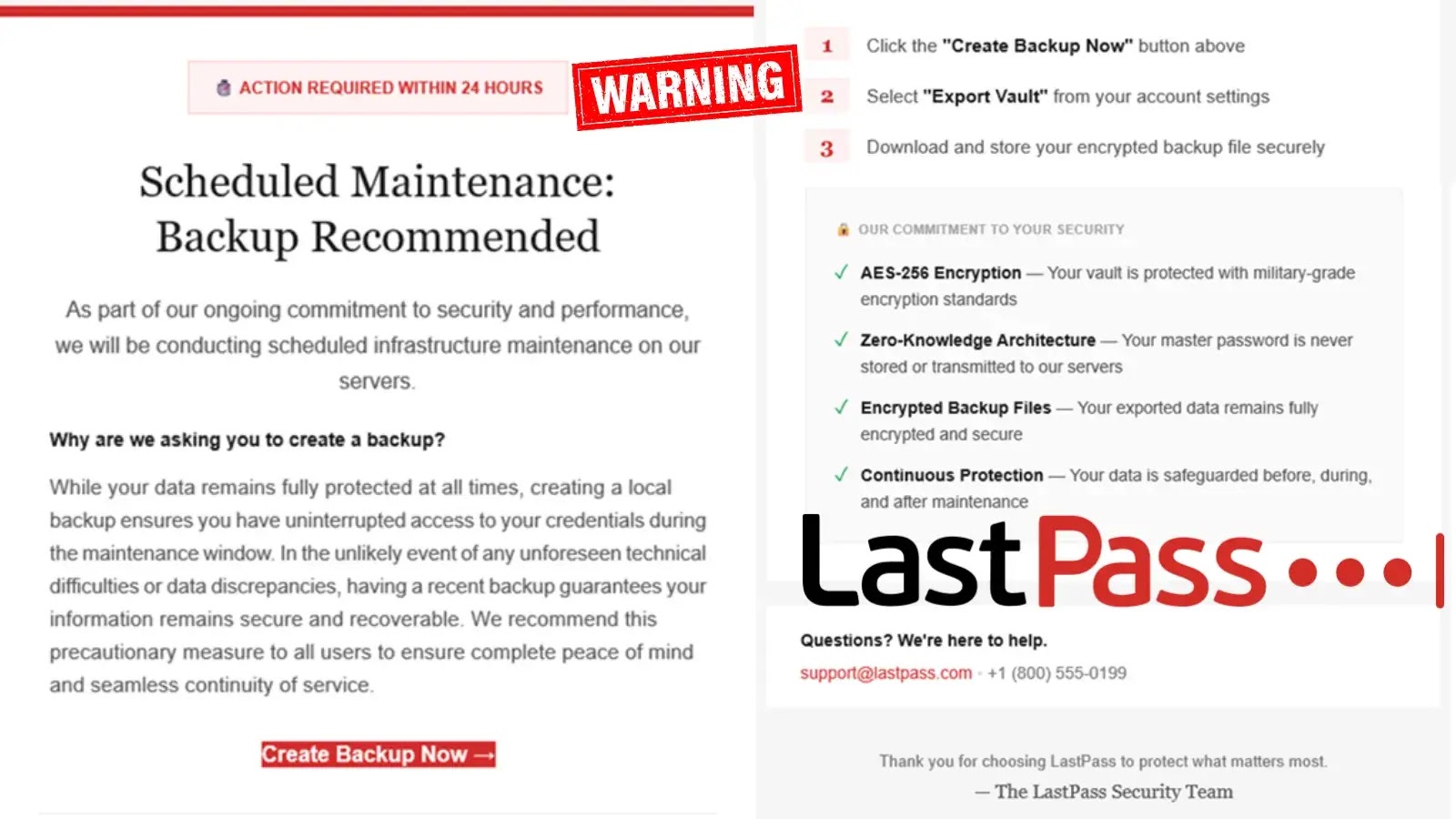
A disturbing new phishing campaign is actively targeting LastPass users, leveraging highly convincing social engineering tactics to steal master passwords. This isn’t a theoretical threat; [...]
GitLab, a cornerstone for millions of developers and IT teams worldwide, has recently rolled out critical security patches addressing a series of vulnerabilities that [...]
Unpacking the Alleged Ransomware Attack on Luxshare: A Supply Chain Security Nightmare for Apple The global technology supply chain, a complex web of manufacturing [...]
Unmasking GlitchFix: How ErrTraffic Weaponizes Visual Breakdown for Malware Delivery In the relentless landscape of cyber threats, attackers constantly innovate, finding new ways to [...]