The global cyber landscape continues to be a hotbed of sophisticated threats, with state-sponsored espionage campaigns relentlessly targeting critical infrastructure and sensitive industries. A [...]
Staying Ahead Of The Curve With A Temporary Email Address The landscape of digital communication evolves rapidly, and with it, the strategies we employ [...]
The AI Revolution in Cloud Threat Detection As organizations increasingly migrate to cloud-native architectures, the sheer volume and velocity of data generated present unprecedented [...]
The digital advertising ecosystem, a vibrant and essential component of the modern internet, faces an increasingly sophisticated threat landscape. At its core, this industry [...]
A disturbing discovery has recently sent ripples through the cybersecurity community, highlighting critical vulnerabilities within a foundational component of virtual machine environments. The VMware [...]
The Unseen Threat: How Google Forms Becomes a Crypto-Theft Weapon In the evolving landscape of cybercrime, threat actors constantly adapt their tactics, leveraging trusted [...]
The digital underworld is in a constant state of flux, with malicious actors continuously adapting their tactics to evade detection and enforcement. A recent, [...]
In the rapidly evolving landscape of artificial intelligence, Generative AI (GenAI) tools are transforming workflows and boosting productivity across industries. However, this powerful technology introduces [...]
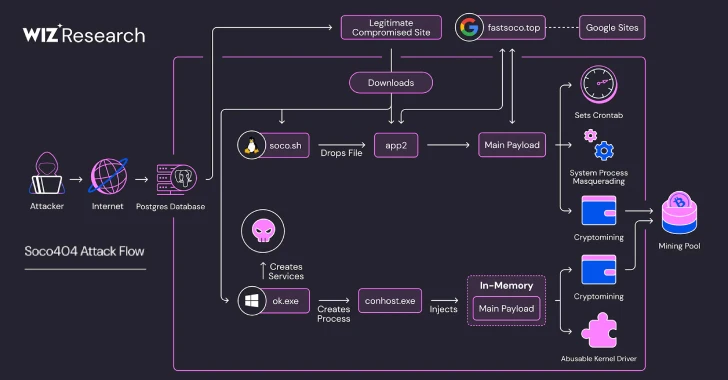
Unmasking Soco404 and Koske: Cryptocurrency Miners Devastating Cloud Environments Cloud infrastructure is the backbone of modern business, yet its very dynamism presents unique security [...]
Malicious Android Banking Apps: A Growing Threat to Indian Mobile Users India’s rapid adoption of mobile banking has unfortunately created a fertile ground for [...]