The Escalating Threat of Credential Theft via Evolving Phishing Attacks Organizations today face an accelerating wave of sophisticated phishing attacks, designed to bypass even [...]
The digital landscape is a battleground where intellectual property often becomes a casualty. In a significant win for content creators and copyright holders, federal authorities [...]
The integrity of national security hinges on the protection of sensitive intelligence. When that trust is breached from within, the implications are profound, extending far [...]
Critical Vulnerability in JavaScript Library Exposes Millions of Apps to Code Execution Attacks A significant cybersecurity threat has emerged, potentially impacting a vast array [...]
The digital landscape is a constant negotiation between innovation and privacy. Nowhere is this more evident than in the recent actions taken by Brave, [...]
The landscape of personal computing is undergoing a significant transformation, driven by the rapid advancements in Artificial Intelligence. Microsoft, a titan in the technology [...]
Coyote Malware Pioneers Windows UI Automation Exploitation for Banking Credential Theft The cybersecurity landscape continually evolves, with threat actors innovating new methods to circumvent defenses [...]
Ransomware Gangs Weaponize RMM Tools: A New Era of Targeted Cyberattacks Once the silent workhorses of IT departments, Remote Monitoring and Management (RMM) software [...]
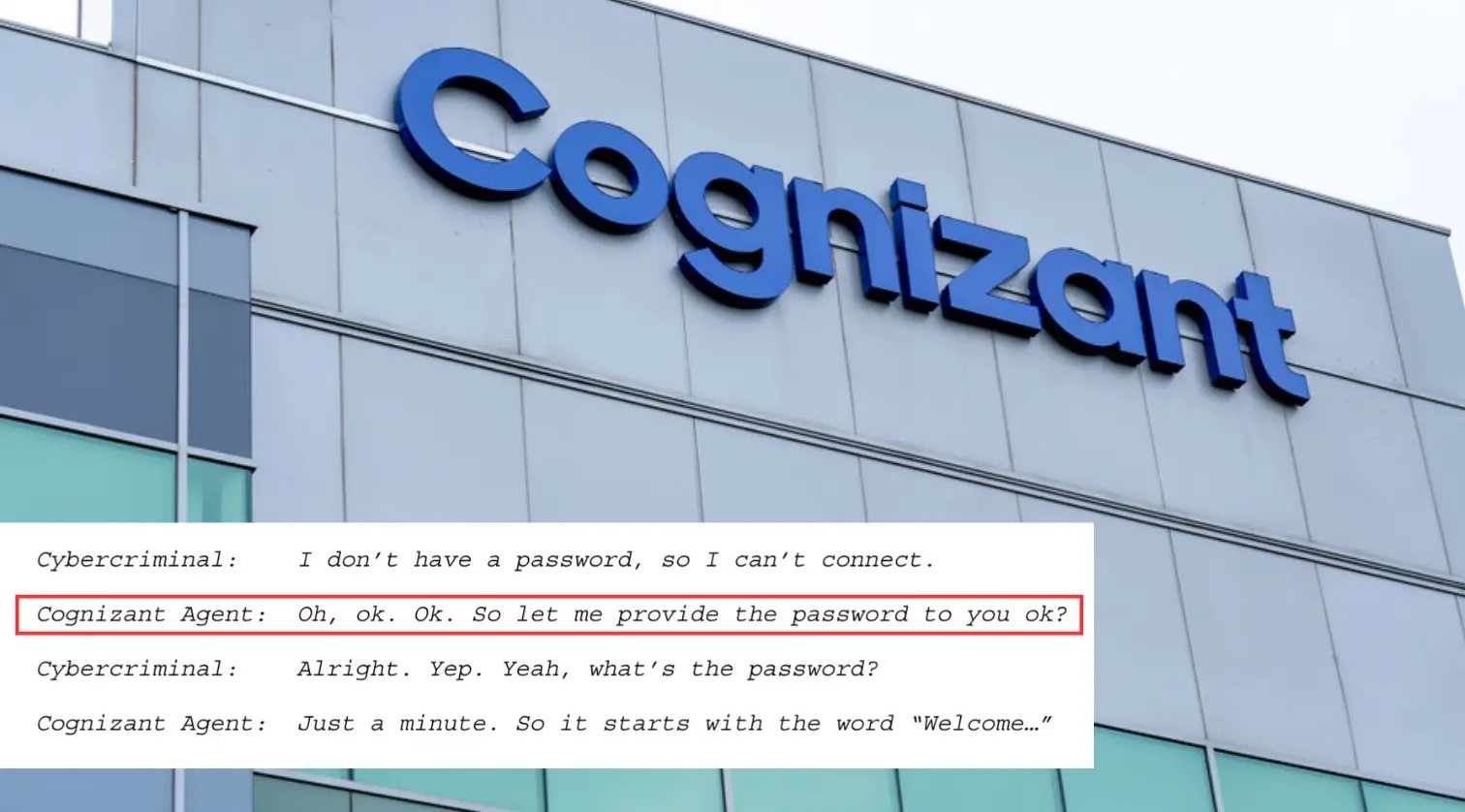
The quiet hum of business operations can turn into a cacophony of disruption when cybersecurity fails. This stark reality has hit The Clorox Company, [...]
Kerberoasting Detections: A New Approach to a Decade-Old Challenge For over a decade, cybersecurity experts have grappled with the persistent threat of Kerberoasting. Despite [...]