The integrity of cybersecurity services procured by government entities is not merely a matter of financial accountability; it’s a critical component of national security. [...]
The pace of cybersecurity innovation often feels like a race, with malicious actors constantly probing for weaknesses. But what if the next big breakthrough in [...]
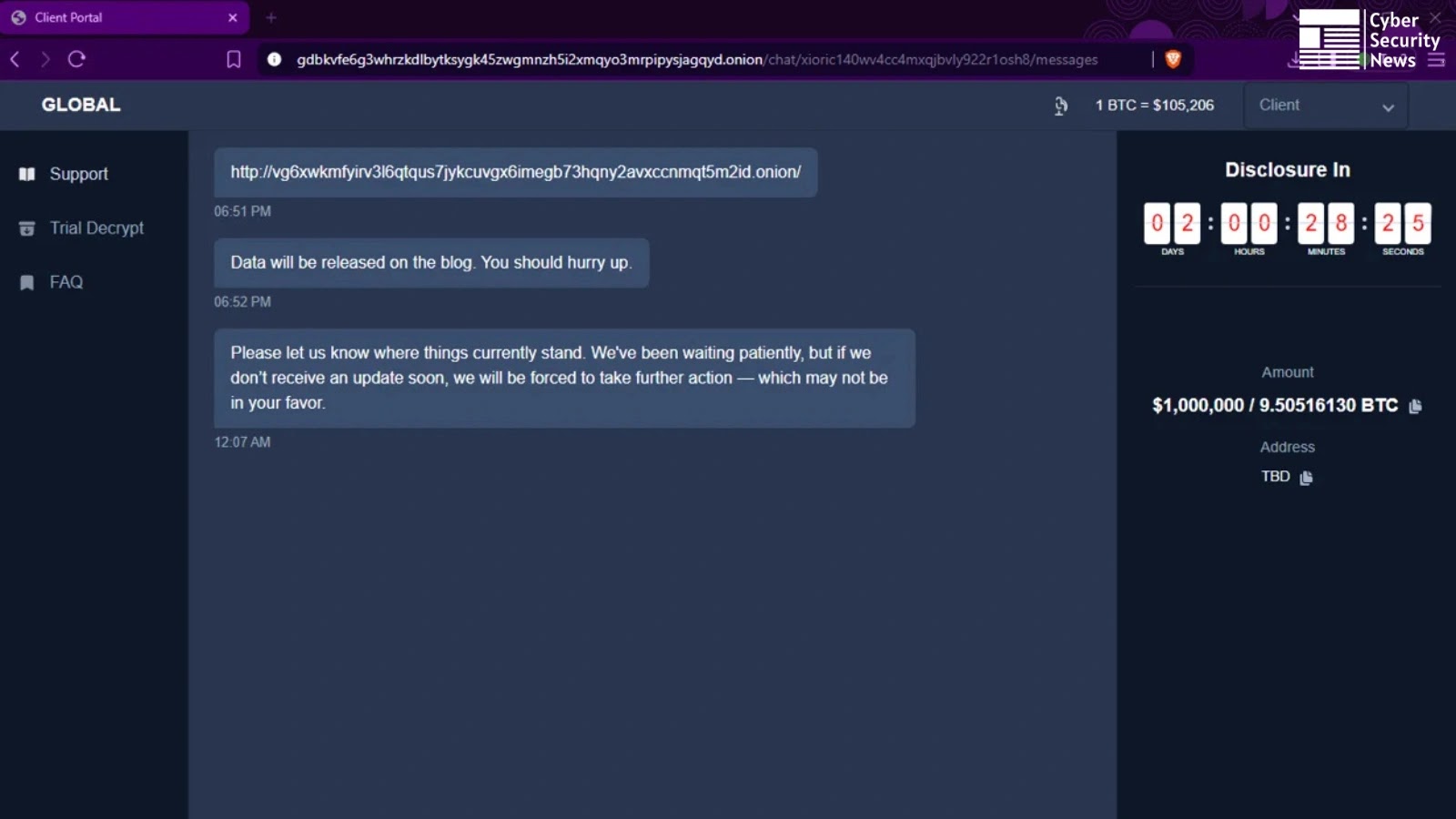
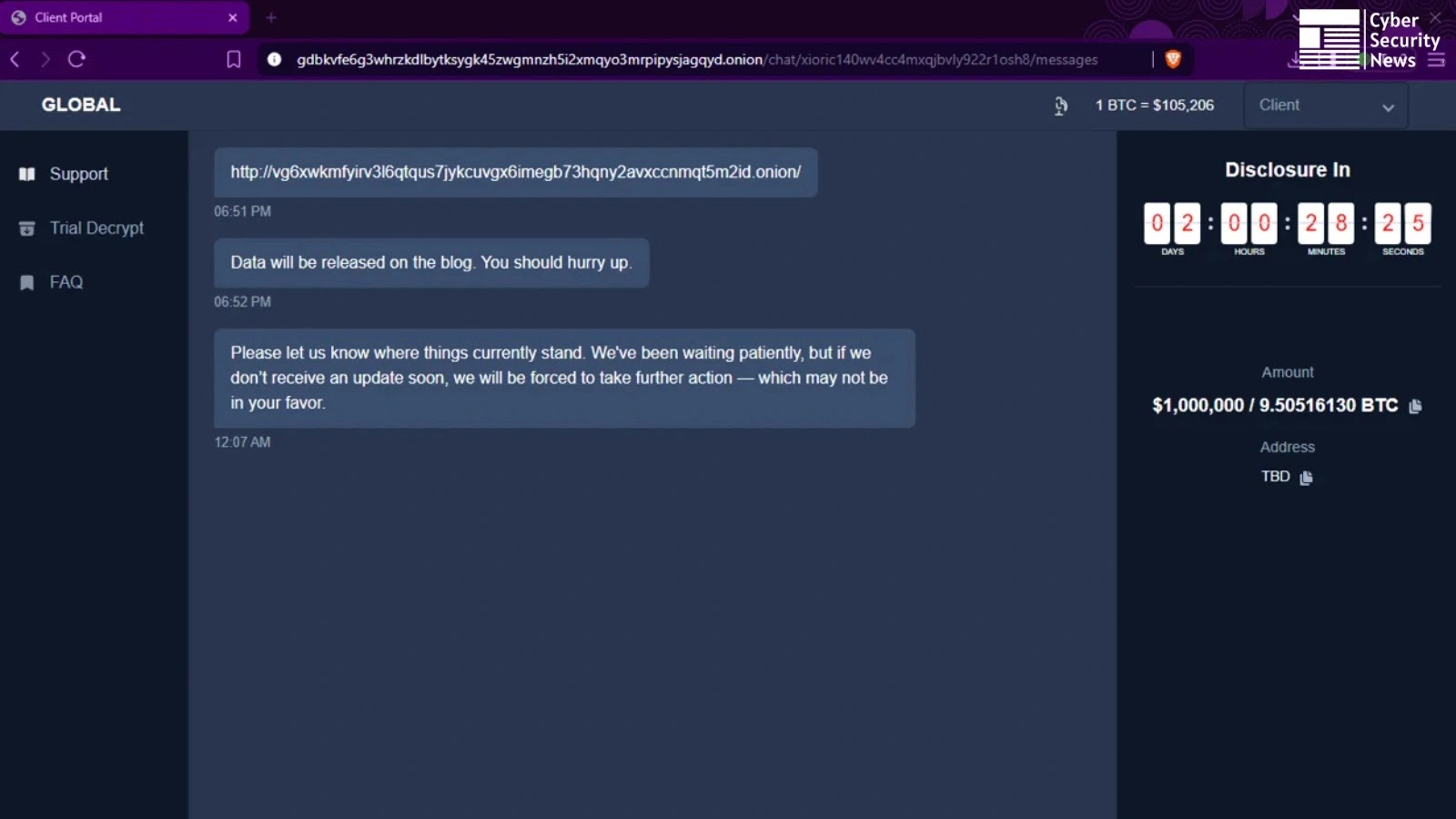
Unmasking GLOBAL GROUP: A New RaaS Threat Leveraging AI for Extortion The cybersecurity landscape has been significantly altered by the emergence of new, sophisticated [...]
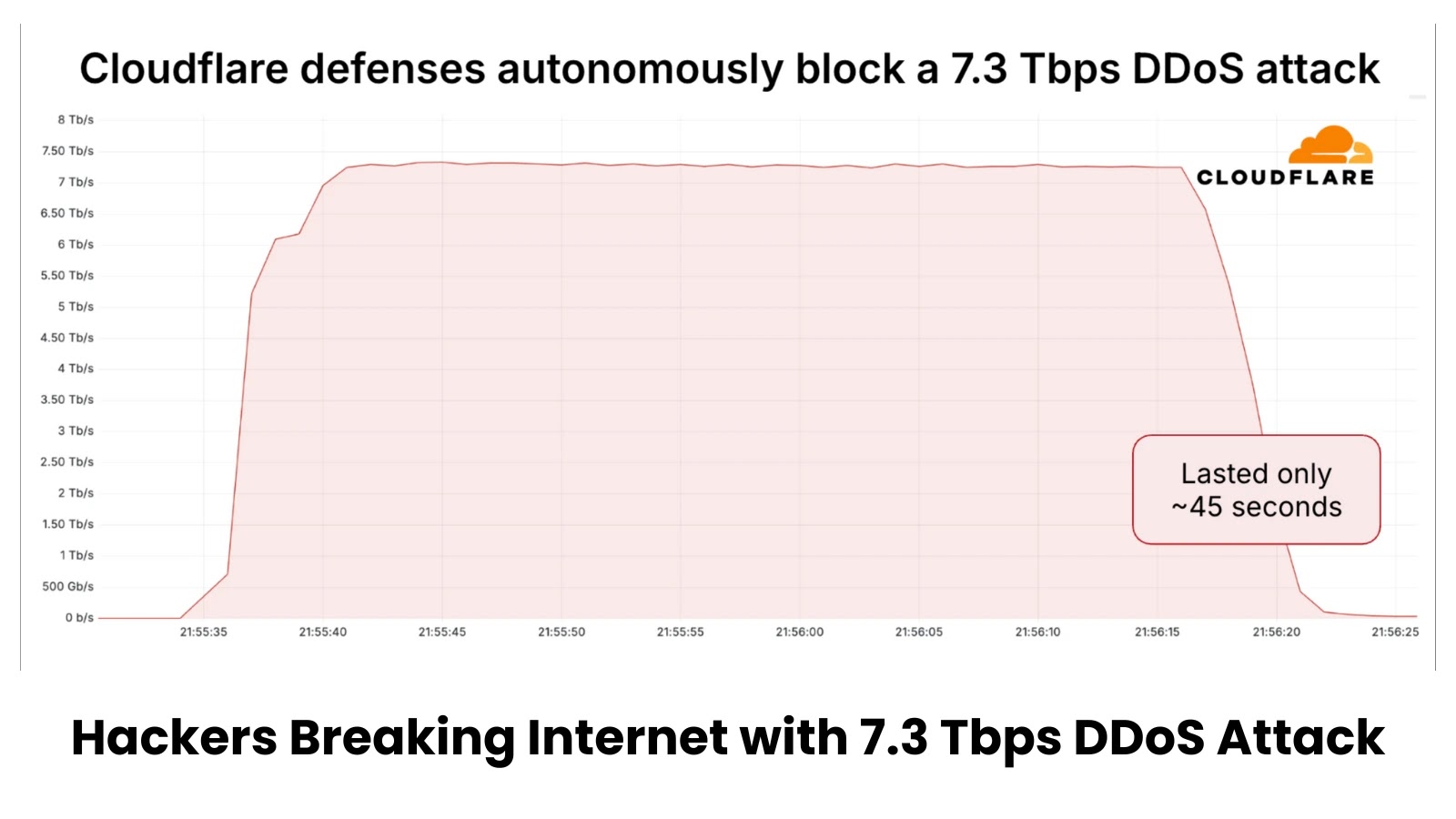
The Unprecedented Deluge: Analyzing the 7.3 Tbps DDoS Attack of 2025 The digital landscape has been irrevocably altered. In 2025, the cybersecurity landscape witnessed [...]
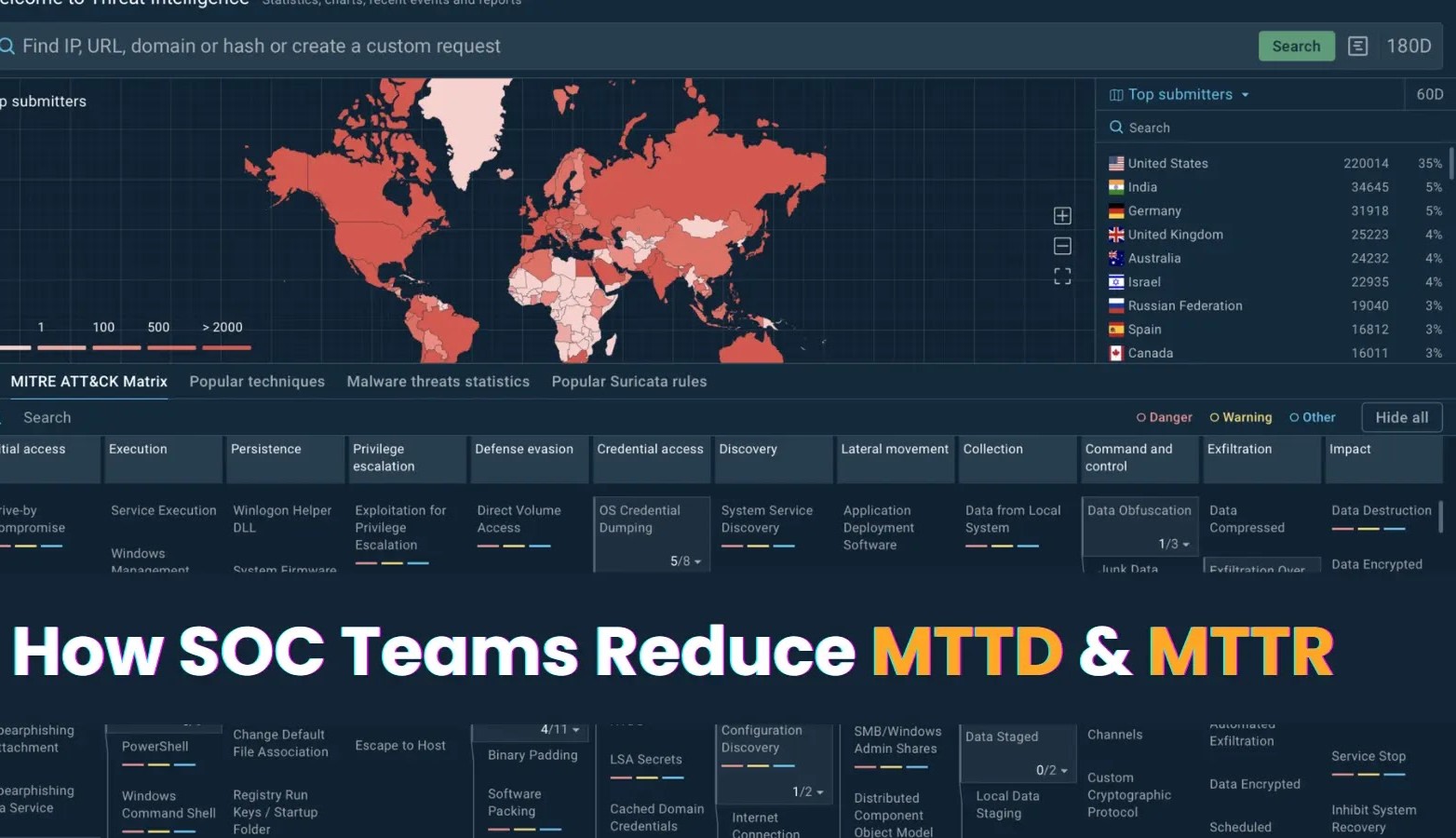
The Critical Role of Threat Context Enrichment in Accelerating SOC Operations In the high-stakes arena of cybersecurity, Security Operations Centers (SOCs) are on the [...]
Unpacking CVE-2025-53506: The Apache Tomcat Coyote Denial-of-Service Vulnerability The digital landscape is a constant ebb and flow of innovation and vulnerability. For organizations heavily [...]
Urgent Alert: Critical VMware ESXi and Workstation Vulnerabilities Demand Immediate Action Organizations worldwide rely heavily on VMware solutions for virtualization infrastructure, from data centers [...]
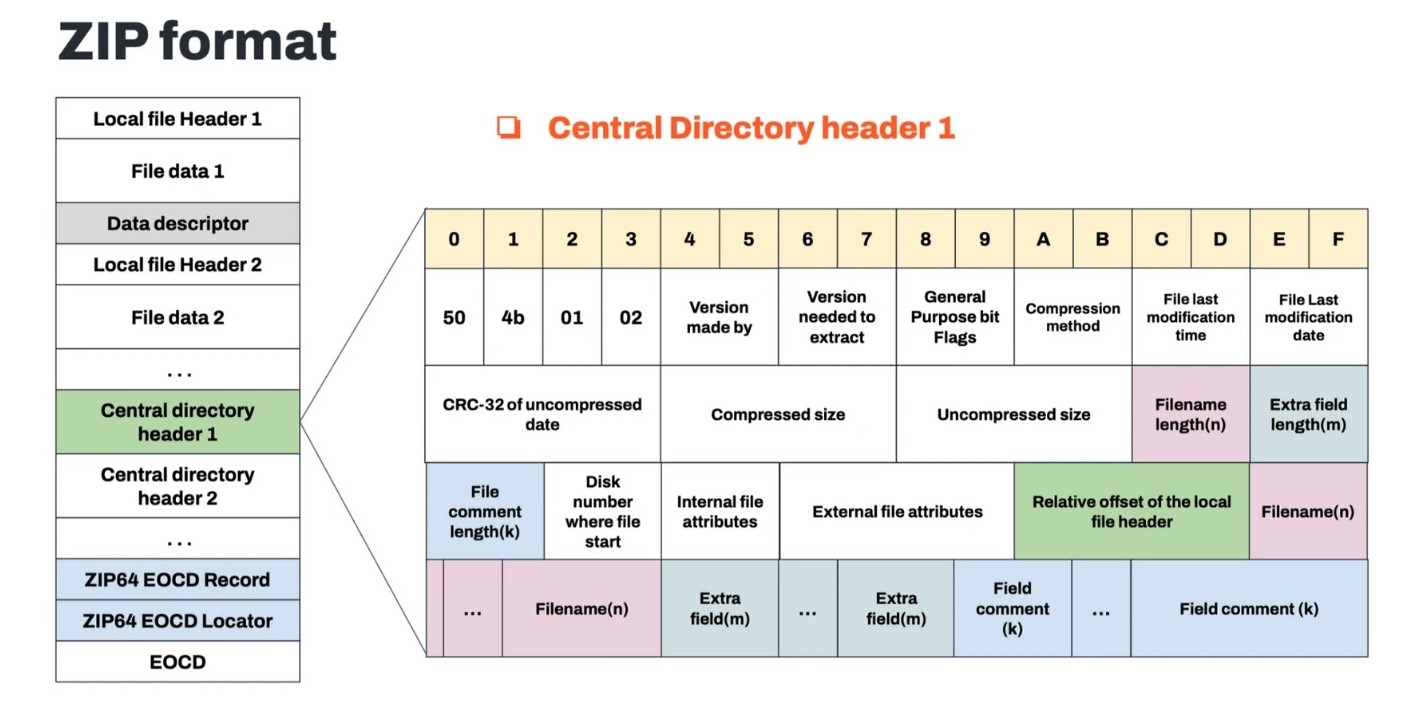
Unmasking Konfety: A Deep Dive into Android Malware’s ZIP Manipulation Tactics on Google Play The digital landscape is a battleground, with sophisticated threats constantly [...]
The landscape of cyber threats continues its relentless evolution, and a formidable new contender has emerged: GLOBAL GROUP, a sophisticated Ransomware-as-a-Service (RaaS) operation. This [...]
Elmo’s X Account Hacked: A Stark Reminder of Social Media Account Security Risks In a deeply disturbing incident that sent shockwaves through the cybersecurity [...]