One Identity Manager 10.0: Elevating Enterprise Identity Security with Risk-Based Governance Modern enterprise environments face an increasingly complex threat landscape. As organizations expand their digital [...]
Unveiling Significant ROI: Airlock Digital’s Independent TEI Study Reveals 224% Return In an era where cyber threats are increasingly sophisticated and the cost of breaches [...]
Sprocket Security Fortifies Leadership with Cybersecurity Veteran Eric Sheridan as CTO The cybersecurity landscape is in a constant state of flux, demanding visionary leadership and [...]
Shipping documents, the mundane workhorses of global commerce, are now being weaponized in a highly effective and stealthy cyberattack campaign. Threat actors are exploiting [...]
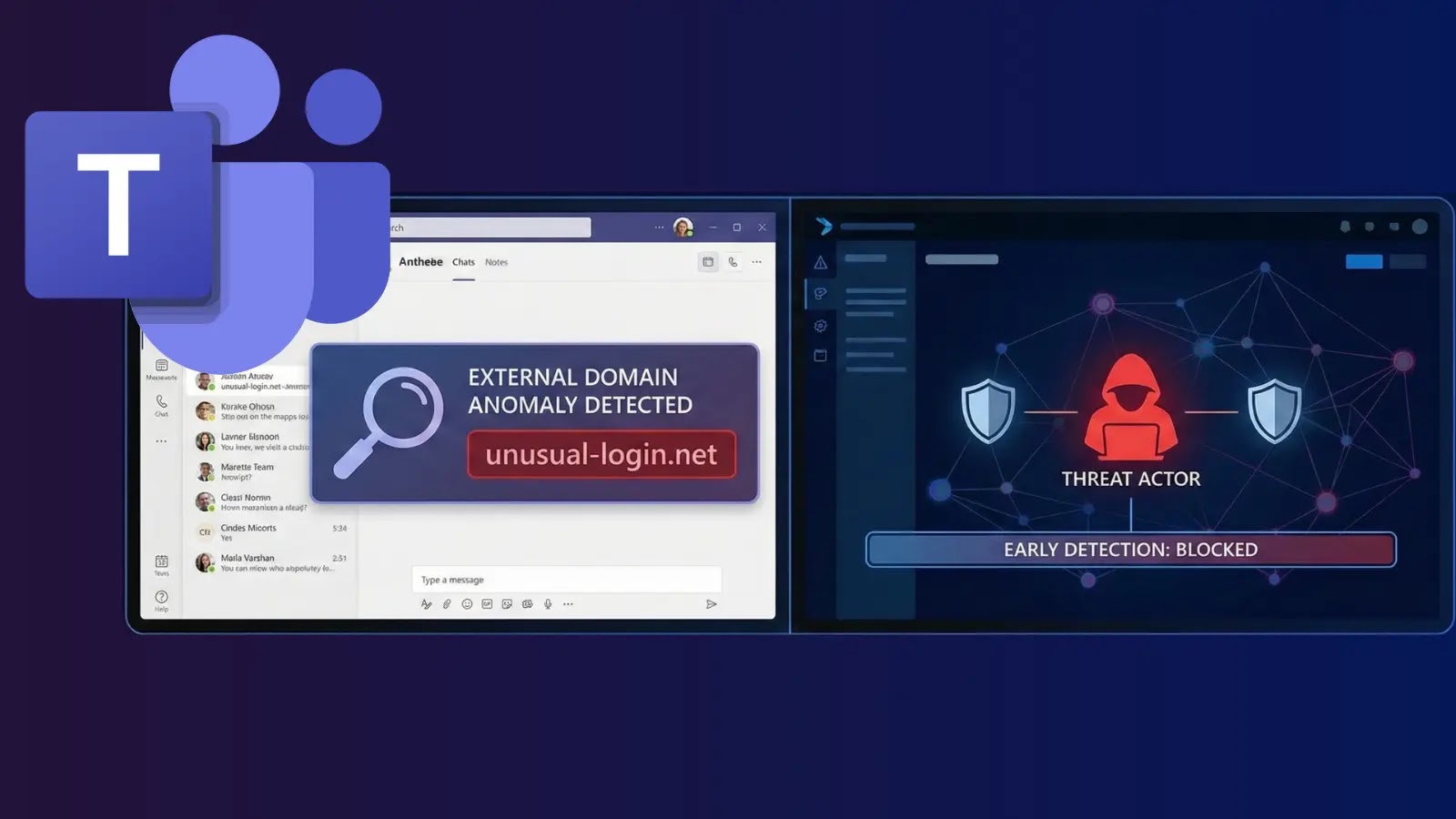
Unmasking Malicious Activity: How Microsoft Teams’ External Domain Anomalies Report Fortifies Your Defenses Modern enterprises rely heavily on collaborative platforms like Microsoft Teams, but [...]
The Trojan in the IDE: North Korean Hackers Weaponize Visual Studio Code The digital battleground continues to shift, and threat actors, particularly those sponsored by [...]
A disturbing trend has emerged in the cybersecurity landscape: attackers are increasingly leveraging the professional credibility of LinkedIn to infiltrate corporate environments. A sophisticated [...]
A critical vulnerability has emerged, striking at the heart of enterprise infrastructure relying on Oracle’s Fusion Middleware. Specifically targeting the Oracle HTTP Server and [...]
Imagine your critical Azure services – Key Vaults safeguarding secrets, CosmosDB powering your applications, or even your Azure OpenAI instances – suddenly becoming inaccessible. This [...]
Unauthenticated Root Access: Unpacking the Critical GNU InetUtils Vulnerability Imagine a scenario where a malicious actor can gain complete control over your critical systems [...]