How can PAM/PAS solutions integrate with cloud environments and hybrid infrastructures? In today’s fast-paced and interconnected world, businesses are increasingly adopting cloud environments and hybrid [...]
Endpoint Detection and Response (EDR) and Endpoint Prevention are critical components of modern cybersecurity strategies. They focus on protecting endpoints, which are individual devices like [...]
Is Your Organization’s Endpoint Security at Risk? Find Out Now! As organizations navigate the new landscape of remote work, ensuring the security of devices connected [...]
In an era of increasing concerns about security and public safety, Closed Circuit Television (CCTV) surveillance has emerged as a powerful tool in preventing and [...]
How can Artificial Intelligence and Machine Learning be integrated with CCTV cameras to enhance security and analytics? Integrating artificial intelligence (AI) and machine learning (ML) [...]
In the rapidly evolving world of technology, software licenses have become a critical component for businesses to ensure legal compliance and maximize efficiency. However, managing [...]
In today’s rapidly advancing technological landscape, it is crucial for businesses to strategically plan and budget for their IT investments. However, with the ever-changing nature [...]
Managed IT Services can play a crucial role in enhancing cybersecurity and protecting sensitive data. One way they do this is by implementing robust security [...]
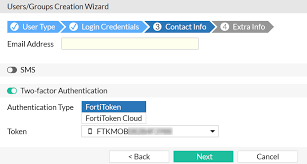
Transfer FortiToken Mobiles: Enhancing Security or Vulnerability Risk? Transfer FortiToken Mobiles is a feature that allows users to seamlessly move their FortiToken Mobile authentication app [...]
What is the Network Load Balncing? Network Load Balancing (NLB) is a technique used to distribute network traffic evenly across multiple servers or network resources [...]