The digital landscape is a constant battleground, and a recent, urgent alert sent shivers through the UK’s cybersecurity community. On January 19, 2026, the National [...]
Gootloader’s Stealthy Resurgence: A Low Detection Threat Bypassing Security Tools The cybersecurity landscape is a constant arms race, and recent intelligence indicates a concerning re-emergence. [...]
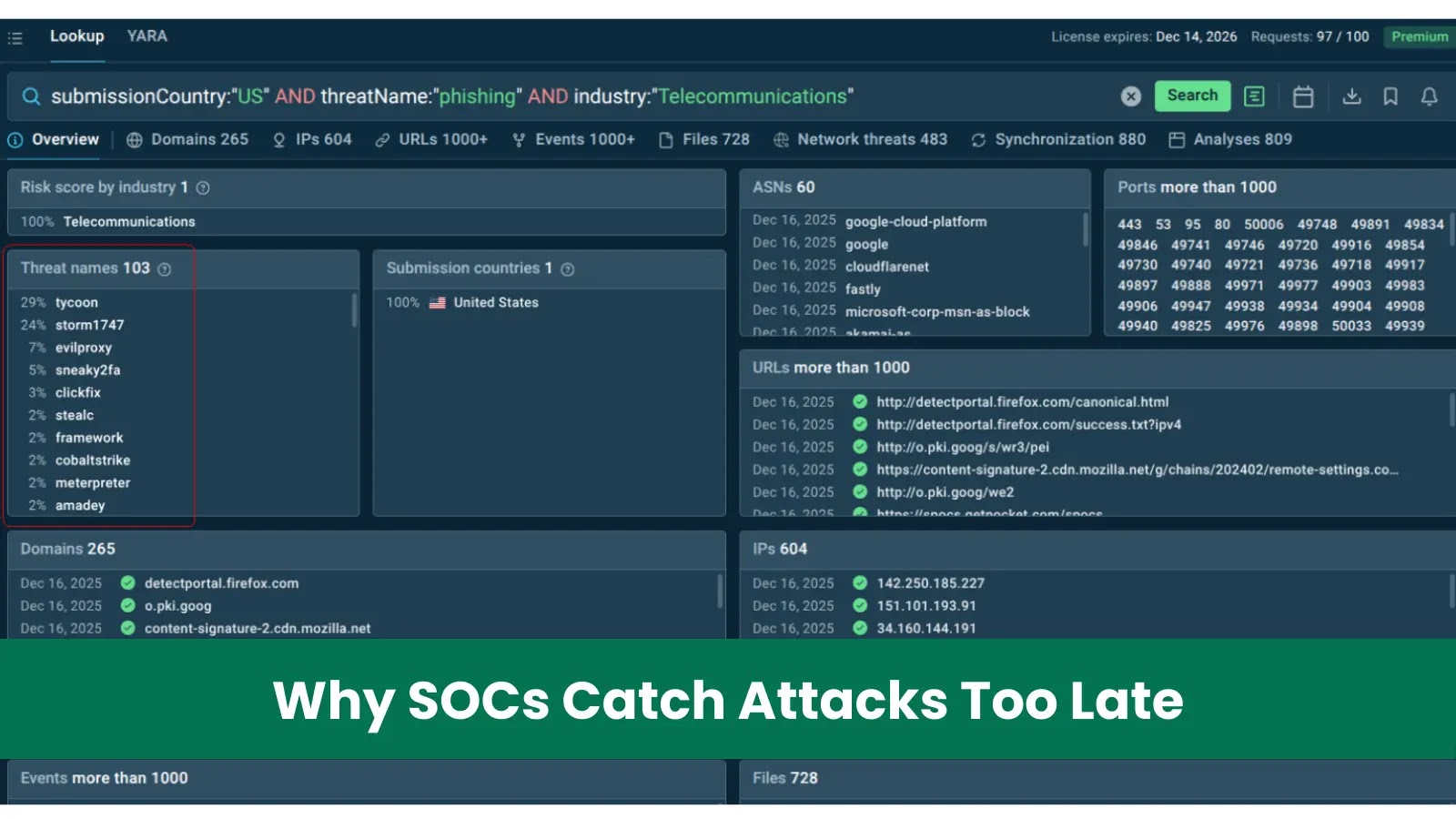
The Costly Reality: Why Delayed Attack Detection Plagues Most SOCs The stark truth for many Security Operations Centers (SOCs) is that they’re consistently a [...]
Critical WordPress Plugin Flaw: Over 100,000 Sites at Risk of Full Takeover A severe vulnerability has surfaced in the widely used Advanced Custom Fields: Extended [...]
Unmasking the Threat: Apache Airflow Vulnerabilities Expose Sensitive Data Data orchestration platforms like Apache Airflow are the backbone of modern data pipelines, managing complex workflows [...]
The digital world thrives on convenience, but with every click, every download, and every streaming session, our personal data is exchanged. This exchange, while enriching [...]
Unmasking the TP-Link VIGI Vulnerability: A Critical Authentication Bypass Exploit In the evolving landscape of interconnected devices, the security of surveillance systems is paramount. A [...]
OPNsense 25.7.11 Released: Enhancing Network Management with Host Discovery Proactive network management and robust security are paramount in today’s complex IT environments. Open-source firewalls like [...]
VoidLink: A New Era of Linux Rootkits Emerges The landscape of cyber threats targeting Linux cloud environments has taken a concerning turn with the discovery [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Remote Code Execution vulnerability in Fortinet Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected FortiSIEM [...]